Amidst the recent political unrest in the Middle East, researchers have observed significant changes in Internet traffic and connectivity. In this article we tap into a previously unused source of data: unsolicited Internet traffic arriving from Libya. The traffic data we captured shows distinct changes in unsolicited traffic patterns since 17 February 2011.
Most of the information already published about Internet connectivity in the Middle East has been based on four types of data:
In this article we discuss another type of Internet measurement data that can be useful in monitoring macroscopically visible Internet events: unsolicited packets destined to unused address space. Similar to the notion of Cosmic Microwave Background Radiation , this Internet "background noise" of unsolicited packets consists of packets sent by misconfigured hosts, hosts that are scanning the network, or victims of DoS attacks with spoofed source addresses.
On 21 November 2008, the amount of unsolicited traffic at the UCSD network telescope (described below) grew dramatically with the advent of the Conficker worm , which widely infected Windows hosts and actively scanned for hosts to infect on TCP port 445. From that point on about 60-80% of unsolicited Internet traffic is via TCP port 445 . Sufficiently pervasive worms such as Conficker allow informed estimates of aggregate infection rates -- in this case of a vulnerable (ie. unpatched) Windows population -- by monitoring traffic to unassigned IP address space.
The Conficker worm scans whenever a host is online, although its rate of scanning is higher when it detects no user activity on a machine (see this report by Symantec). So the amount of unsolicited traffic originating from Conficker's network scanning allows us to see hosts that are online, but where the user is not actively generating Internet traffic.
The UCSD network telescope captures traffic destined to the unassigned address space in a /8 network, with relatively few blocks in this /8 where end hosts are active. Filtering this data for source addresses from a specific region provides an indication of host activity for that region. We used the MaxMind GeoIP Lite database, January 2011 edition, to map IP addresses to geographic regions, and recorded the per-second packet rate (averaged over 60 seconds) from address ranges that geolocated to Libya. Figure 1 shows five weeks of these packet-per-second averages, and Figures 2, 3 and 4 show the same data zoomed in to interesting 2-day, 3-day and 7-day intervals, respectively.
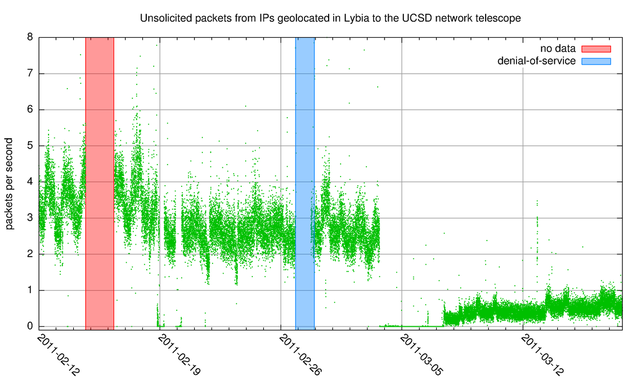
Figure 1 shows unsolicited one-way traffic for five weeks, including some "silent" gaps with absolutely no traffic, and other intervals with larger and more typical levels. During these five weeks there was an interval of about one-and-a-half days where the data collection server didn't collect data, indicated in light red with label 'no data', and for a period of about a day where traffic levels were almost always higher then 8 packets per second (pps), indicated in light blue with label 'denial-of-service'. Figure 1 also shows a number of intervals with next to no traffic, notably in the 18 - 21 February period and between 3 and 8 March. This is shown in more detail in Figure 3 and Figure 4 below. After 8 March the amount of unsolicited traffic is slowly picking up again, but not to the levels from before 3 March.
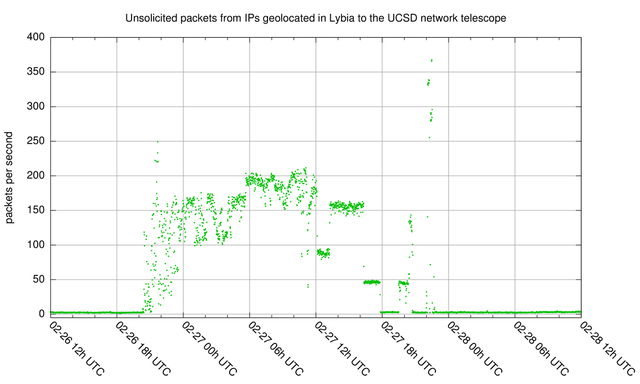
Figure 2 shows a 2-day period that includes an interval of higher packet rates, labeled "denial-of-service" in Figure 1, on a different y-scale. Where outside of this period the packet rate usually is below 5 pps, during this period the packet rates received go up to 367 pps at the highest peak. While the unsolicited traffic outside this interval is dominated by traffic to TCP/445, the higher-packet rates interval is dominated by SYN/ACK packets from TCP/80 from a single source IP address to seemingly random destinations in the UCSD network telescope. This is typical " backscatter " of a denial-of-service attack, in this case of a single webserver we geolocated to Libya. There are intervals where packet rates stay around 50, 100, 150 and 200 pps, which could point at an attacker stepping their attack up and down. Note that we only saw a small fraction of the return traffic from this attack, but it looks like this attack was very modest by current standards (see for instance this news report on a tens of millons of pps attack on Wordpress ).
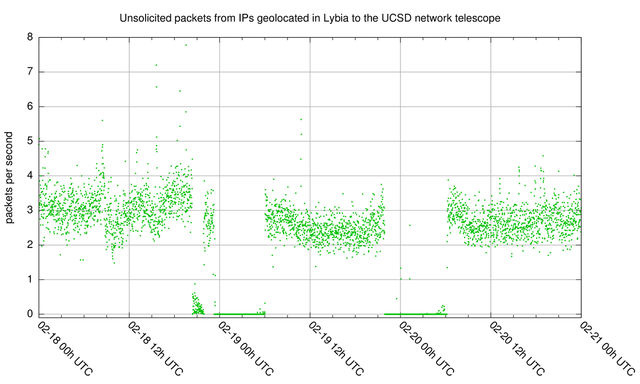
Figure 3 shows two distinct overnight outages consistent with Arbor Networks's netflow measurements during the same period (18 - 21 February 2011). Interestingly in both cases, a small trickle of traffic begins right before the outage ends. Occasional traffic is often observed during these outages, which could be an artifact of traffic with spoofed IP addresses or inaccuracy in the geolocation database we used for prefix selection.
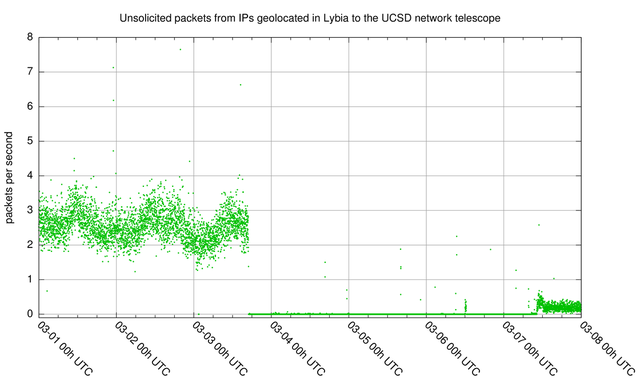
Figure 4. Unsolicited Internet traffic during 1 - 8 March 2011 from IP address blocks that geolocated to Libya according to MaxMind GeoIP Lite database, January 2011 edition.
Figure 4 reveals a longer outage visible from approximately 3 March 18:00 UTC to 7 March 11:00 UTC. The traffic levels after this outage were significantly lower then before. Figure 1 shows a slow subsequent increase after this outage to roughly 20% of pre-outage traffic levels. In Google's transparency index search queries are less then 5% of pre-outage levels, so it seems that the few hosts we observe sending out unsolicited traffic after this outage do significantly fewer search queries to Google than the population of hosts before the outage. It is unclear if this is due to stricter filtering of traffic to Google, and potentially other websites. A tiny spike in traffic around 12 March 19:58 UTC to pre-outage levels is visible in Figure 1, and also visible in Google's data, which could be interpreted as a temporary glitch of an Internet filter.
Conclusion
Ironically, the insidious pervasive reach of malware like the Conficker worm enables observation and detection of macroscopic changes in Internet behaviour.
In this case we saw several anomalies in the amount of unsolicited traffic out of networks we geolocated to Libya over the last couple of weeks.
CAIDA is coordinating further analysis of this data by a team of vetted researchers. Please comment below if you have any questions.





Comments 6
The comments section is closed for articles published more than a year ago. If you'd like to inform us of any issues, please contact us.
Anonymous •
Very neat work Emile! You should take a look at our P2P perspective on the same event - we posted it in the aqualab blog.
Anonymous •
Hi Emile<br /><br />I have to say I love your approach to use Internet Background Noise as a detection method.<br /><br />I'm doing currently a master in forensic information technologies at the Auckland University of Technology (AUT). I would like to do a small research project where I would try to analyse the influence of a natural disaster on the IBN. Therefore I'm currently trying to get access to some relevant data and I would like to ask you if it would be possible for me as a student to get access to your data source and if so under which conditions.<br /><br />Thank you for your feedback<br />- Roman Ammann, <a href="mailto:aut@xxo.ch">aut@xxo.ch</a>
Anonymous •
Hi Roman,<br /><br />CAIDA is doing the vetting for data access, so you'd typically contact them with a good description of the research you plan to do. I'll put your request in email, so it can be taken care of.<br /><br />regards,<br />Emile<br />
Anonymous •
To get knowledge about this area, internet connected computers which are using Microsoft systems, triggered to upload or fetched remotely valuable datas to be used by some group/groups (military or political).<br /><br />It will be understood enough if you provide not only the source but also the target of these packets.<br /><br />If you do not publish the target of those packets, then you are one of other side. To be honest to the world, do not hesitate to publish target maps. Otherwise people will have some suspect in their minds.
Anonymous •
Dear Kesret,<br /><br />If I understand your request correctly, you would like to see the destination of the unsolicited traffic from Libyan source IP addresses.<br /><br />The UCSD Network Telescope only sees traffic that is destined to the address space of it's own network, not of any other networks, so it is impossible to see traffic to any other network from this data.<br /><br />regards,<br />Emile
Doug Wulff •
Emilie, Thanks for the data. Even the latest Q2 2012 attack report by Prolexic shows 91% of DDoS attacks originate in countries outside the United States. The question is if a country offers no business value, why not block the traffic your network? We use the PoliWall in-line appliance to block foreign traffic and can throttle bandwidth by country to mitigate against DDoS attacks. Hope this helps. http://www.techguard.com