Amplification DDoS attacks are one of the most prevalent forms of denial-of-service attacks. The SISSDEN project (sissden.eu) operates a network of honeypots designed to detect these attacks, observing 10,000 per day.
Amplification DDoS Attacks
Amplification DDoS attacks are one of the most prevalent forms of denial-of-service attacks. This type of reflective denial-of-service attack abuses two flaws in core networking protocols:
- IP header information is not authenticated
- UDP does not employ a handshake
The first flaw allows an attacker to spoof requests to a vulnerable service in the name of the victim, the second flaw causes the vulnerable service to answer this request immediately.
The benefit of these attacks for attackers are two-fold: Firstly, by using vulnerable services as traffic reflectors, these attacks inherently hide the attacker's address, thereby hindering prosecution. Secondly, small requests usually suffice to trigger large responses, leading to an amplification in attack bandwidth towards the victim. Depending on the protocol being abused, an amplification factor of 100x or more can be achieved. Many popular protocols can be abused for this, including DNS, NTP, SSDP and more.
What makes amplification DDoS attacks even more widespread is the fact that such attacks can easily be purchased online from so-called booter services. These websites often operate under the disguise of a legitimate service offering "stress-testing capabilities" to network operators, but allow one to freely "stress-test" any IP address for only a small fee.
Observing Amplification Attacks
The SISSDEN project (sissden.eu) operates a network of honeypots designed for amplification DDoS attacks. These honeypots mimic vulnerable services with the intent to be "abused" by attackers. However, instead of then relaying attack traffic towards victims, a log-message is generated instead allowing SISSDEN to observe these attacks in near real-time. Over the last year, our honeypots observed between 7,000 and 17,000 amplification attack per day, with an average of about 10,000.
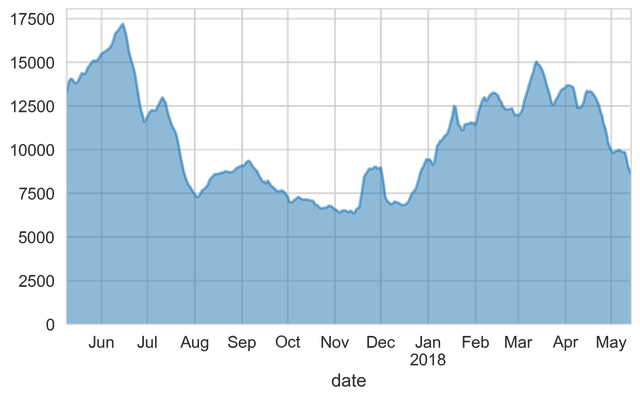
Figure 1: Number of amplification attacks per day
Amplification Vectors
Breaking these down per protocol reveals some interesting insights (see Figure 2). For example, the first spike in January was mainly caused by an increase in DNS-based attacks, as were the ones in mid- and end-of March. On the other hand, the spike in end-of January was caused by CharGen-based attacks, and in mid-April, NTP saw an increase.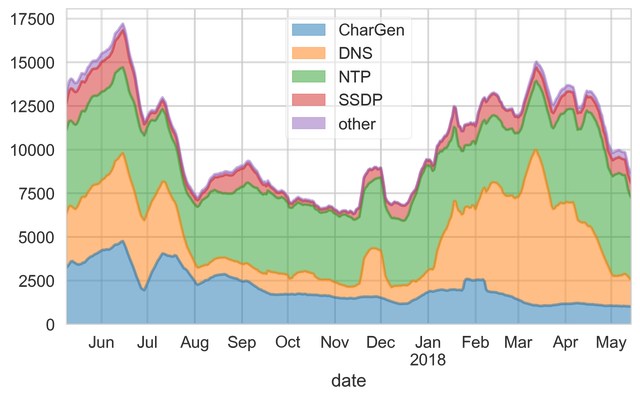
Figure 2: Number of amplification attacks broken down by protocol
These relations can be even better seen in a normalised graph, giving relative percentages between attack protocols. As can be seen, the most prevalent attack vectors are CharGen, DNS, NTP, and SSDP. Two more interesting observations that can be drawn from the graph in Figure 3.
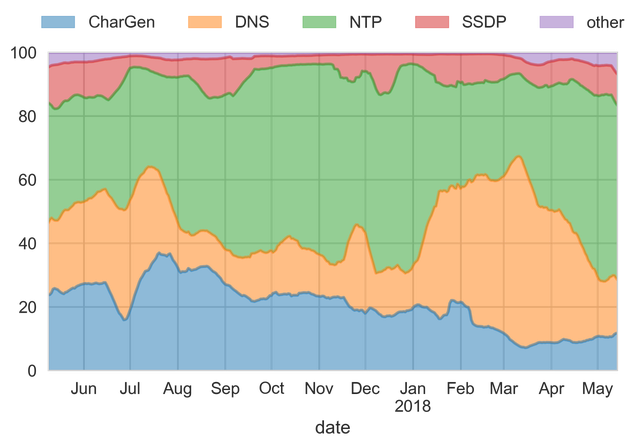
Figure 3: Number of amplification attacks broken down by protocol, normalised
Firstly, attackers are quick to find and abuse vulnerable servers. After the amplification vulnerability in Memcached was revealed, we added support for memcached to our honeypot, with a roll-out in the first days of March. Only a few days later, Memcached can be seen to constitute a notable fraction of attacks observed by our honeypots, meaning that attackers found and added our honeypots to their list of reflectors.
Secondly, many of these attacks seem to stem from booter services. This can be seen, as there is a notable decrease in DNS-based attacks towards the end of April, which coincides very well with Europol's actions against webstresser, one of the biggest booter services to date.
Attack Durations
Interestingly, amplification attacks are not very long-lasting. More than 90% of attacks are shorter than one hour, and more than half last only five minutes. In fact, 20% of all attacks are shorter than one minute.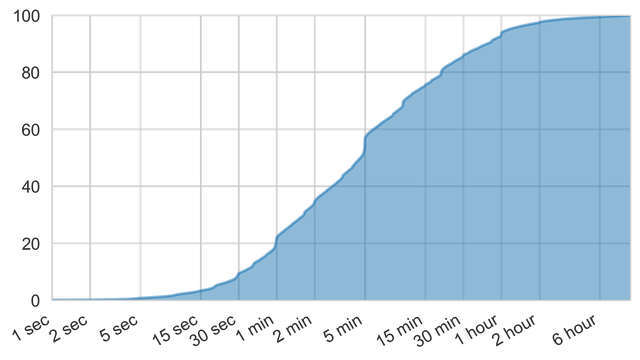
Figure 4: Duration of amplification attacks
Looking at the durations of amplification attacks gives another indication of automated attacks, visible as almost step-wise increases around one and five minutes, respectively. As booter services often only allow to select an attack duration from a predefined list, one would expect to see these steps in the above graph. This is further confirmed by similar steps around 30 seconds, 10 minutes, 20 minutes, and one hour.
Attack Repetitions
On the upside, victims that experience amplification attacks are unlikely to do so more than once. In fact, over 75% of all victim addresses observed by our honeypots were targeted only once, and less than 5% saw more than five attacks (see Figure 5).
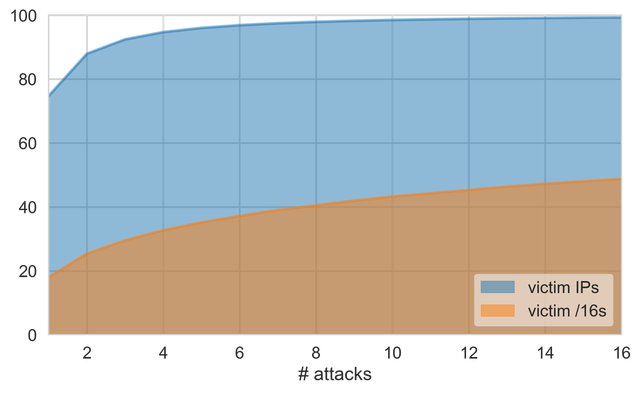
Figure 5: Number of attacks per victim address
Attack Victims
To get a better understanding of who is being hit by these attacks, one can plot all IP addresses into a 2D-plane using a space-filling curve, such as the Hilbert curve (e.g. see here). Choosing a scale such that one pixel corresponds to a /16 network, the entire IPv4 space can then be plotted on a 256x256 grid, with brighter colours corresponding to a higher number of attacks in the given network.
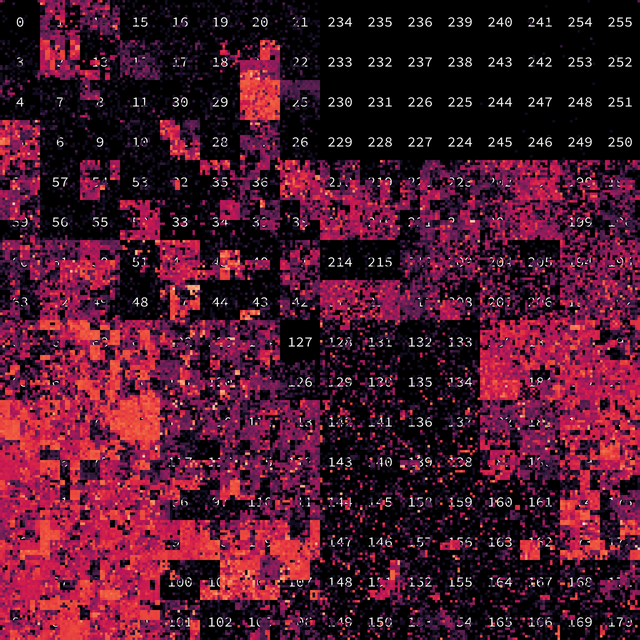
Figure 6: Hilbert curve showing which parts of the IPv4 address space is suffering mostly from attacks
Comparing the above graphs with the allocated ranges shows that the only non-attacked (dark) areas in the graph mostly correspond to reserved or unused IP space (such as 127.0.0.0/8 or 240.0.0.0/4).
Summary
Amplification attacks are still one of the most prevalent threats in 2018, with over 10,000 attacks observed on a daily basis, targeting Internet participants world-wide. However, most of these attacks seem to stem from booter services, indicating that continued effort in their take-down will eventually lead to a reduction in DDoS attacks.

Comments 5
The comments section is closed for articles published more than a year ago. If you'd like to inform us of any issues, please contact us.
Vijay Sarvepalli •
Your study is interesting, thanks for sharing. I noticed though all your graphs are missing Y-axis label. The figure-4 especially is a bit confusing as you have interpret the area under the curve see where it tapers off, it is better reversed (1/x) to show typically 30 minute segments of booster service blackmarket for hire DDOS. Hilbert curve could have a better description that almost nobody is spared from DDOS attacks - if in fact that is your conclusion from this data. Vijay
Eireann Leverett •
Wonderful work, and thank you very kindly for the graphs. They are exactly what I was looking for. I saw this the day it came out on the blog and have cited it in presentations at least twice already, and will no doubt continue to do so for quite a while. Is this part of a wider publication, or should I keep directing people to this blog post?
Mirjam Kühne •
Hi Eireann, many thanks for the feedback. I am happy to hear the information was useful (that's what I was hoping for when I saw Johannes's presentation at the recent TF-CSIRT meeting). The report is part of a wider project ( https://sissden.eu/ ), but for now it might be best to refer back to this blog post as the project is still ongoing.
Lucas •
Hi, Nice work! Do you have the numbers of attack per day and per honeypot? Are the number of attacks observed by each honeypot nearly the same or have a high variation? Thanks.
Johannes Krupp •
Thanks. Yes, we do keep the numbers of attacks per day (and per honeypot as well). So far the number of attacks observed has been nearly the same over all honeypots. Interestingly though, not all attacks are observed by all honeypots. Then again our honeypots only constitute a small fraction of all potential amplifiers out there, so some variation is to be expected.