Prompted by a discussion at the last RIPE Meeting, we found out how many maintainer (MNTNER) objects are registered in the RIPE Database and what type of authentication methods are used to secure the data covered by these MNTNER objects.
Objects in the RIPE Database can only be modified by those authorised to do so. For instance, an object representing a certain range of IP addresses assigned to an organisation by the RIPE NCC or a Local Internet Registry (LIR) can be modified by the organisation holding that address space. Each database object contains one or more attributes referencing the maintainer(s) of that object. In a maintainer (MNTNER) object, credentials are listed for those who are authorised to modify any object referencing that MNTNER. A credential can be any of the following:
-
An MD5 encrypted password string
-
A PGP key,
-
An X.509 certificate
These are the authentication methods supported by the RIPE Database software. Each credential should map one to one with a real person.
After a discussion at the recent RIPE 62 Meeting in Amsterdam, we were asked to find out how many MNTNER objects registered in the RIPE Database are actively maintaining other database objects and what type of credentials are used to secure the MNTER object itself and other types of objects.
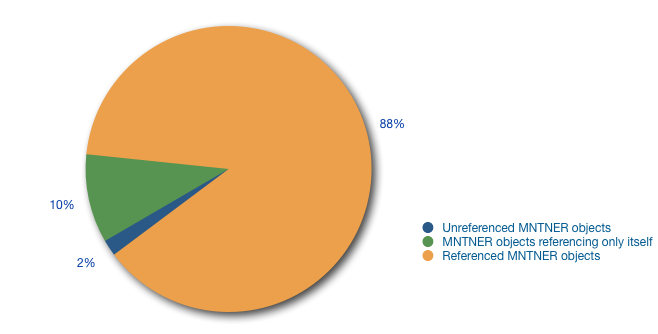
First we looked at the number of MNTNER objects in the RIPE Database and checked to see how many were actively maintaining other objects in the database. We found a total of 36,768 MNTNER objects. Of those, 32,397 were referenced by other objects. That means they are actually used to secure other objects, which is the basic function of a MNTNER. For the remaining 4,371, we saw that 3,692 of them only referenced themselves. This means that they were used to secure the MNTNER object itself, but not any other object in the database. And 672 were not referenced at all. This means these MNTNER objects were not actually used to secure objects in the RIPE Database, not even the MNTNER object itself. (The remaining seven were deleted between collecting the list of MNTNER objects and doing the analysis.)
In Figure 1 below, you can see the distribution of the types of MNTNER objects described above.
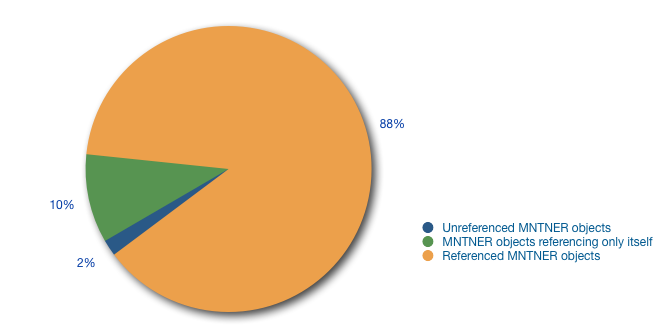
Figure 1: Number of MNTNER objects referenced by other objects in the RIPE Database
Next we looked at how many of the referenced MNTNER objects used each type of authentication method. Multiple authentication methods and credentials are allowed in one MNTNER object. Encrypted passwords are currently the most commonly used method. We found 27,796 MNTNER objects that contained only password credentials and no other authentication methods. A further 1,507 contained only PGP keys and no other methods. And 21 contained only X.509 certificate IDs and no other methods. The remaining 3,073 MNTNER objects contained more than one credential type. This distribution is shown in Figure 2 below (the number of objects only containing X.509 is so small that is not visible on the chart).
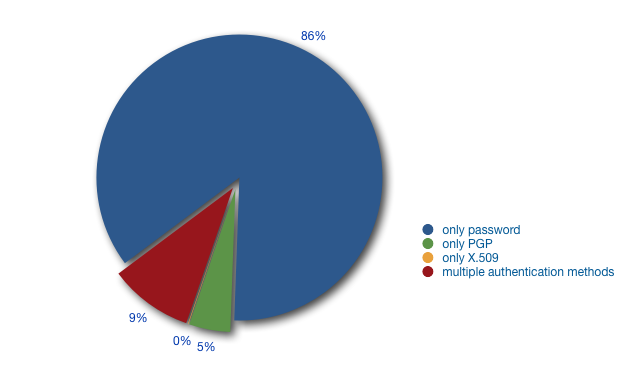 Figure 2: Type of credentials used in MNTNER objects in the RIPE Database
Figure 2: Type of credentials used in MNTNER objects in the RIPE Database
The majority of those MNTNER objects that use password as an authentication method only contain one password. But there are a few with multiple entries. We even found two objects that list 22 different passwords. The majority of those MNTNER objects that use PGP as an authentication method only contain one PGP key. But there are quite a number that contain more than one, with 35 different PGP keys in one MNTNER object. Of those objects that use X.509 as authentication method, we found objects with up to seven different X.509 certificate IDs.
It is interesting to point out that only 50 out of all the MNTNER objects in the RIPE Database do not use passwords as an authentication mechanism. Instead, they use a combination of PGP and/or X.509.
The number of MNTNER objects is not the critical figure here. How much address space is maintained by these 50 MNTNER objects in the RIPE Database is more relevant. There are various ways to calculate this. We looked at the address space allocated to LIRs and how it is further assigned and maintained. If an INETNUM object contains a "mnt-lower:" attribute, this means the holder of the address space represented by this INETNUM object is entitled to make assignments to others from this block of addresses. We looked at the allocations whose re-assignments out of these address ranges are authorised by these 50 MNTNER objects described above. We added together the sizes of the address blocks where one of these 50 MNTNER objects is used in the "mnt-lower:" attribute and calculated the percentage this represented of the total allocated address space.
We found that an amount of 4,722,688 IPv4 assigned addresses are authorised by these 50 MNTNER objects. That is only 0.85% of all the allocations and assignments either made by the RIPE NCC directly or by an LIR using a "mnt-lower:" attribute. The other 99.15% is authorised by MNTNER objects that include one or more password credentials for authentication.
Compared to MD5, PGP is a stronger method of encryption and also provides checks against tampering with the message content. But this is much more aligned with emails. It does not work well with real time web applications.
The MD5 hash is generally thought to be a strong encryption for passwords. This could be improved with some implementation changes in the RIPE Database software, for example by not publicly displaying the encrypted string and limiting the number of failed attempts to authenticate within a given time period.
Further interesting statistics
As discussions continue within the RIPE Community on the way in which authentication is implemented in the RIPE Database we re-ran the statistics program and gathered some additional statistics on the use of different credentials.
Here is a summary of some of the significant numbers with comments. We have rounded them off (mostly) to integers and ignored the (almost insignificant) X.509 usage. So some summations may be slightly out. All percentages relate to the total number of MNTNERs in use.
Total number of MNTNERs in use = 33323
MNTNERs with only password = 28556 86%
MNTNERs with only PGP = 1532 5%
MNTNERs with password and PGP = 3167 10%
Authentication is a logical OR. So password and PGP, in terms of authentication security level (while hashes are exposed) is the same as the lower security of password. So 96% of all MNTNERS use passwords.
Then we looked at the issue of MNTNERs maintaining other MNTNERs. This is where the most corner cases exist with any plan to hide password hashes. In this we did not include MNTNERs that maintain themselves and also have additional MNTNERs maintaining them. We assumed these to be self maintained but simply have extra numbers of credentials to authenticate against.
Total MNTNERs not self maintained = 1550 5%
Subset of these not self maintained MNTNERs that have passwords = 1428 4%
Number of unique MNTNERs maintaining these not self maintained MNTNERs = 909 3%
So 3% of MNTNERs maintain the 5% of MNTNERS that are not self maintained . We then looked at what credentials these 3% (909) MNTNERS use.
Password only = 686 2%
PGP only = 91 0.3%
Password and PGP = 128 0.4%
Finally we looked at how many MNTNER objects are successfully modified each day. Over a seven day period in November there was an average of 22 MNTNER object updates per day.



Comments 1
The comments section is closed for articles published more than a year ago. If you'd like to inform us of any issues, please contact us.
Anonymous •
Does not compute. Article says: "only 50 out of all the MNTNER objects in the RIPE Database do not use passwords as an authentication mechanism." *But* it also says "A further 1,507 contained only PGP keys and no other methods. And 21 contained only X.509 certificate IDs and no other methods." So that's at least 1528 MNTNER objects that don't use passwords.