The RIPE NCC has been signing its zones since 2005. Other operators waited for the root to be signed. And signing the root zone in June 2010 clearly encouraged others to deploy DNSSEC. In this article we describe the status of those zones maintained by the RIPE NCC and give an overview of the global deployment of DNSSEC.
The Domain Name System Security Extensions (DNSSEC) is a suite of IETF developed specifications designed to validate information provided by the Domain Name System (DNS).
A number of early adopters deployed DNSSEC for the domain they are responsible for. Among these early adopters were the country code Top Level Domains (ccTLDs) .br, .bg, .cz, .pr, .se and the generic Top Level Domain (gTLD) .org. Besides TLD operators, organisations like the RIPE NCC and the RIPE community as a whole were on the forefront of DNSSEC development. The RIPE NCC has signed it’s DNS zones since 2005. However, many TLD operators waited for the root zone to be signed before they started deploying DNSSEC.
When the root zone has been signed in June 2010, this acted as a catalyst for TLD operators to deploy DNSSEC on their side. We have seen a gradual but significant increase in signed TLDs since then.
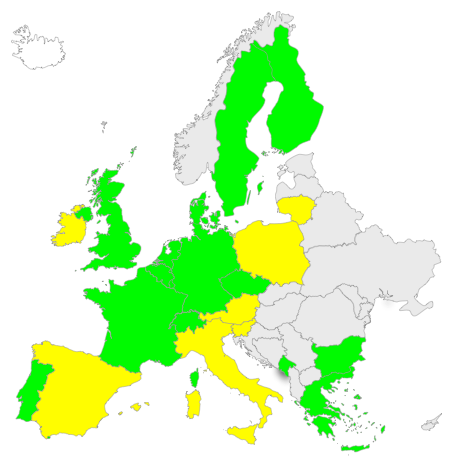
The maps below show the level of DNSSEC deployment in the world to date. Those countries marked green have deployed DNSSEC in their ccTLD today. Those marked yellow have plans to deploy it in the near future.
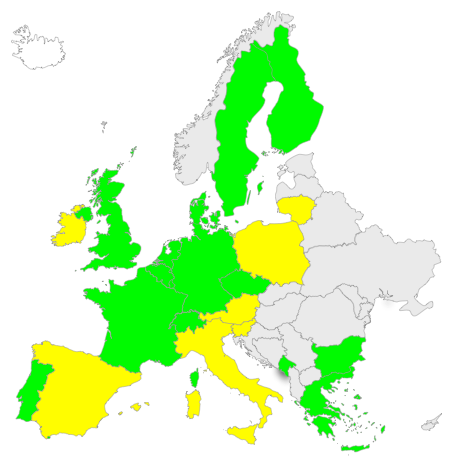
Figure 1: DNSSEC in European ccTLDs (green=deployed, yellow=planning to deploy)
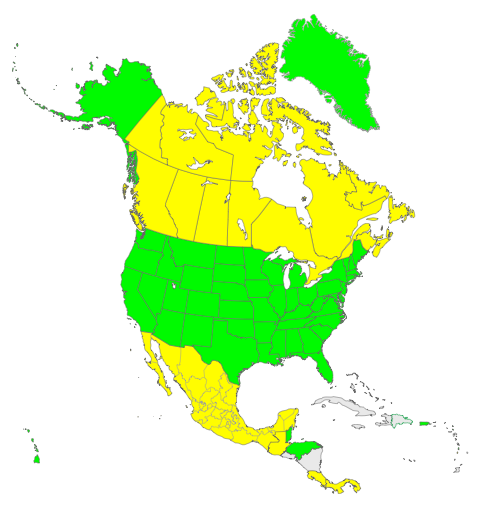
Figure 2: DNSSEC Deployment in North America
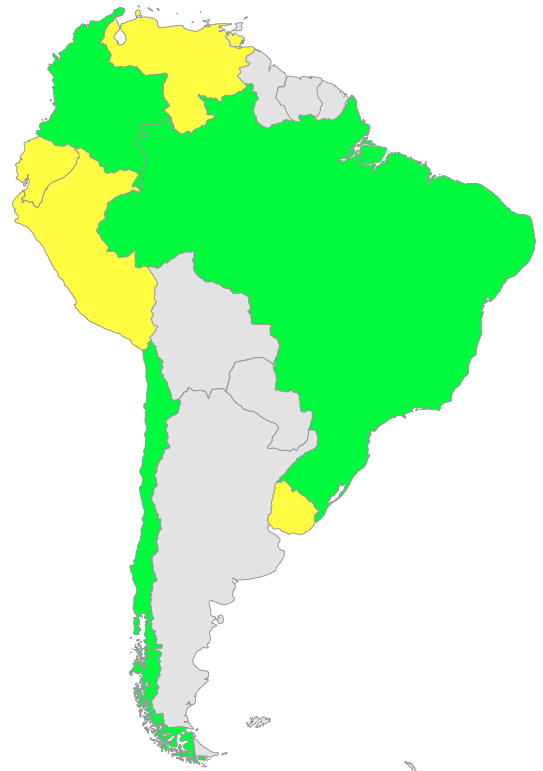
Figure 3: DNSSEC Deployment in South America
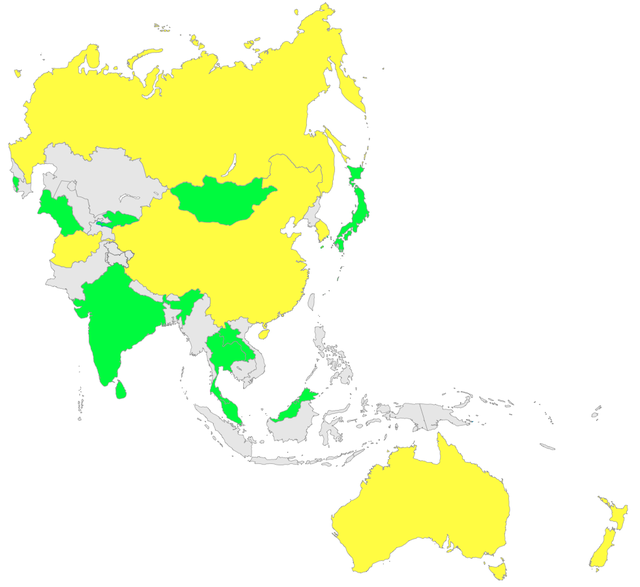
Figure 4: DNSSEC Deployment in Asia Pacific
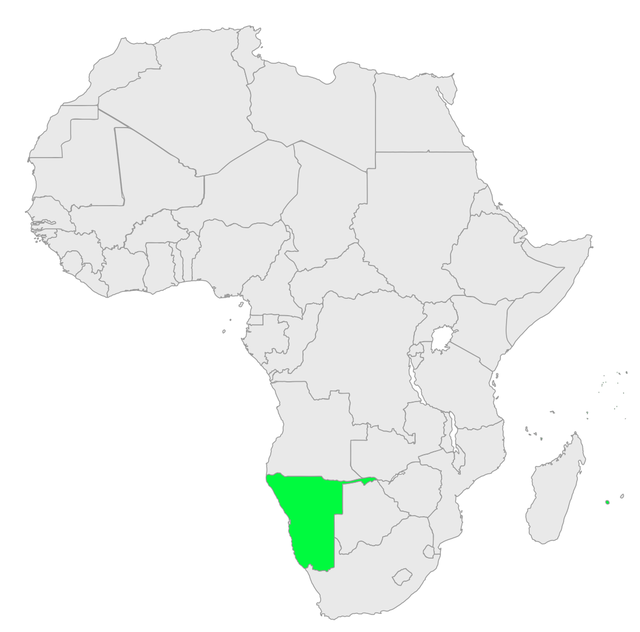
Figure 5: DNSSEC Deployment in Africa
As far as we are informed, no countries in the Middle East are currently planning to deploy DNSSEC. If you have other information, please let us know so that we can update the article.
At the core of DNSSEC is a so called chain-of-trust which uses the hierarchy by which a domain is delegated from the root zone to a TLD and then to the domain operator. For DNSSEC to be fully useful, this chain of trust needs to be complete. This means that for a domain owner DNSSEC becomes truly useful once the TLD that domain is under is signed, too.
The RIPE NCC is maintaining zones in domains under several TLDs. The vast majority of the zones under these TLDs are by now supporting DNSSEC, because the parent zones allow delegation signer (DS) records to be included and therefore completing the chain of trust. Recently we also enabled the IPv4 reverse zones in the in-addr.arpa parent zone.
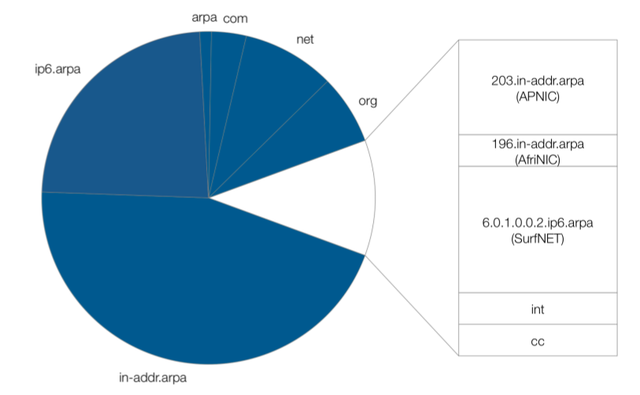
Figure 6: Zones with (blue) and without DNSSEC
As shown on the right hand side of Figure 2 above, the only zones in which we cannot yet include the trust anchors in the parent zone, are:
- 203.in-addr.arpa (maintained by APNIC)
- 196.in-addr.arpa (maintained by AfriNIC)
- 6.0.1.0.0.2.ip6.arpa (maintained by SurfNET)
- .int (maintained by IANA)
- .cc (ccTLD of the Cocos (Keeling) Islands)
We expect that at the end of this year, only three of them will be left in which we cannot include our DS records: 196.in-addr.arpa, .int and .cc. That is considered a huge progress since the root zone has been signed.
Below you can see a graph showing DS records inside our reverse zones. We observe a steady increase. In total there are currently 450 DS records in our zones.
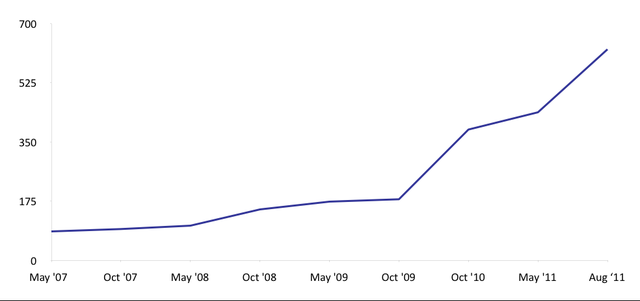
Considering that the RIPE NCC maintains some 500.000 reverse delegations, this number is still very small. However, the recent increase is encouraging.
From our point of view we are pleased with the progress that DNSSEC has made since the root zone has been signed a year ago. There has been a lot of speculation, and in a poll done amongst many industry experts very few expected that signing the root zone would have such a substantial and fast impact on the number of TLDs getting signed.


Comments 8
The comments section is closed for articles published more than a year ago. If you'd like to inform us of any issues, please contact us.
Anonymous •
Correction: 6.0.1.0.0.2.ip6.arpa is not maintained by SURFnet, although 0.1.6.0.1.0.0.2.ip6.arpa is.
Anonymous •
Hi Simon,<br /><br />The pie chart was trying to reflect the top-level zones (by our very own definition ;)). The idea was to have a "normalized" pie-chart with equally-weighted zones.<br /><br />Regards,<br />Wolfgang
Anonymous •
Nice graphics!<br /><br />I was wondering about the percentage of zones that are covered by these DS records. As we saw with IPv6 traffic reported by Arbor Networks, growth in absolute numbers may still mean a decline in relative numbers. :(<br /><br />For the reverse tree, this can be measured by domains, but even more interestingly by address space that those domains represent.<br /><br />Just a thought. :)
Anonymous •
I don't know where the information regarding the "DNSSEC Deployment Today" has been collected. Italy is grey in map, while .IT is working on DNSSEC and plans to deploy it in the near future.<br /><br />Best regards,<br />Maurizio Martinelli<br />.IT Technical Manager
Anonymous •
Dear Maurizio,<br />Sorry for the late response. We used the data listed in the ICANN TLD DNSSEC Report. If .it is planning to deploy DNSSEC, we'd be happy to update the map in the article. Do you know when DNSSEC will be deployed in the .it registry? <br /><br />Kind Regards,<br />Mirjam Kuehne
Anonymous •
Hi Maurizio,<br /><br />As for the planned deployments - we did our best in summarizing the DNSSEC plans we could find on public mailing lists. We are very happy to hear about plans of others and update the map accordingly.<br /><br />Regards,<br />Wolfgang
Luis Espinoza •
.cr is already signed
Mirjam Kühne •
Thanks, Luis. We will include .cr next time we'll update the maps.