This project aims at creating a simple, copy & paste-able HOWTO for secure crypto settings of the most common services (webservers, mail, ssh, etc.). It was presented at the recent RIPE 68 Meeting in Warsaw. For those of you who couldn't attend the meeting, here is summary of the talk.
Introduction
The
bettercrypto guide
arose out of the need for system administrators to have an updated, solid, well researched and thought-through guide for configuring SSL, PGP, SSH and other cryptographic tools in the post-Snowden age. Triggered by the NSA leaks in the summer of 2013, many system administrators and IT security specialists saw the need to strengthen their encryption settings. This guide is specifically written for these system administrators.
Unfortunately, if one is to believe these revelations,
sysadmins, networks and network services are potential targets
for pervasive surveillance. Therefore network operators and system administrators need to do everything possible to protect the data sent through their network. Even though, cryptography doesn't solve all the problems, it does help to a certain extend. However, good cryptography is hard to achieve. The document presented here is meant to help you to implement good cryptography by providing some practical and easy to implement recommendations.
Current work
We want to contribute some practical hints and tips for SSL, SSH and PGP crypto settings in the most common services and certificates, such as:
- Apache, Nginx, lighthttp
- IMAP/POP servers (dovecot, cyrus, ...)
- openssl.conf
- Etc.
The document provides easy, copy & paste-able settings which are „OK“ (as far as we know) for sysadmins. We describe a number of potential attacks and provide some settings that can be used for your operations. So far, the document covers the following sections:
- Disclaimer
- Methods
- Elliptic Curve Cryptography
- Keylengths
- Random Number Generators
- Cipher suites – general overview & how to choose one
- Recommendations on practical settings
- Tools
- Links
In the practical recommendation section we provide two options:
- Variant A: fewer supported clients
- Variant B: more clients, weaker settings
In general we propose the following general settings:
- Disable SSL 2.0 (weak algorithms)
- Disable SSL 3.0 (BEAST vs IE/XP)
- Enable TLS 1.0 or better
- Disable TLS-Compression (SSL-CRIME Attack)
- Implement HSTS (HTTP Strict Transport Security)
We tested our recommended settings for both variant A and B for the following applications:
- Web server: Apache, nginx, MS IIS, lighttpd
- Mail: Dovecot, cyrus, PosÄix, Exim
- Databases: Mysql, Oracle, Postgresql, DB2
- VPN: OpenVPN, IPSec, Checkpoint
- Proxies: Squid, Pound
- GnuPG - SSH
- Instant Message servers (jabber, irc)
Testing tools
We would also like to recommend a number of tools that can be used to test the security settings of your network:
- openssl s_client (or gnutls-cli)
- SSL Labs (checks for servers as well as clients)
- Xmpp
- sslscan
- SSLyze
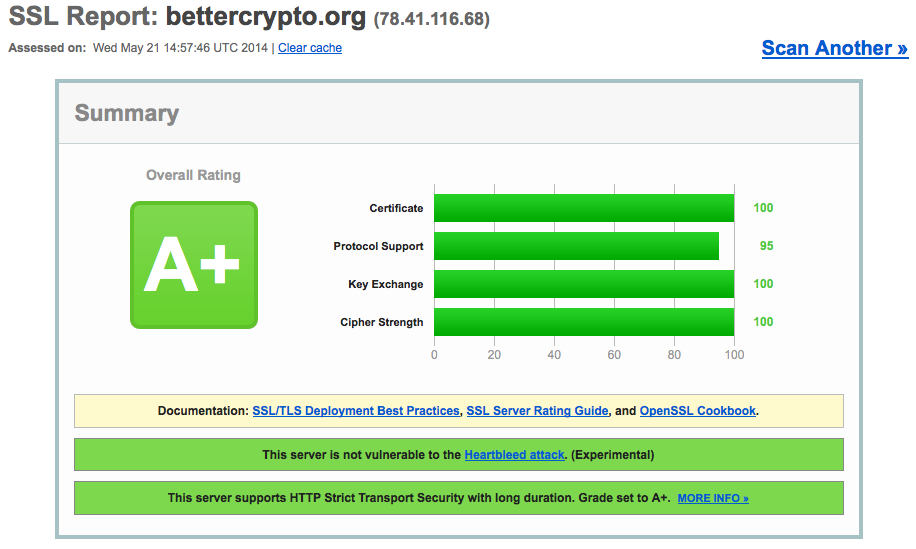
See below an example output from SSL Labs. It runs a number of tests and provides you with feedback and advice on how to improve the security settings.
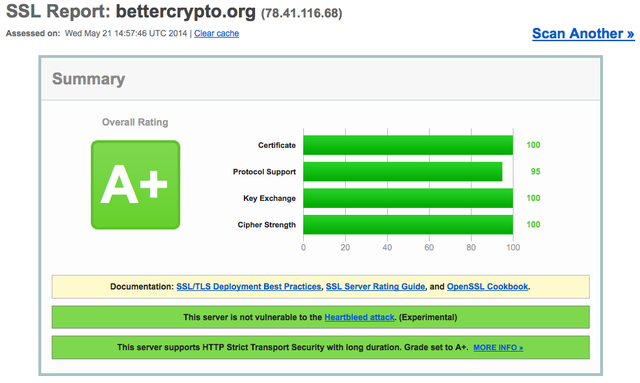
Please note that this project is completely open sourced, every step in the creation of this guide is public, discussed on a public mailing list and any changes to the text are documented in a publicly readable version control system.
Help needed!
We need your help! We are looking for people who can review this document and test the settings provided in it. We particularly need people who:
- Are cryptologists, sysadmins, hackers
- Read the document and find bugs
- Subscribe to the mailing list
- Understand the cipher strings Variant (A) and (B) before proposing some changes
If you add content to a subsection, make a sample config with variant (B). The Git repository is world-readable. Please add content to any subsectioon from the TODO list and send us the diffs.
More Information
- Website: https://www.bettercrypto.org
- Git repository: https://git.bettercrypto.org
- Mailing list: http://lists.cert.at/cgi-bin/mailman/listinfo/ach
Co-authors of the bettercrypto document
Wolfgang Breyha (uni VIE), David Durvaux (CERT.be), Tobias Dussa (KIT-CERT), L. Aaron Kaplan (CERT.at), Chris=an Mock (coretec), Daniel Kovacic (A-Trust), Manuel Koschuch (FH Campus Wien), Adi Kriegisch (VRVis), Ramin Sabet (A-Trust), Aaron Zauner (azet.org), Pepi Zawodsky (maclemon.at), Tobias Pape
New contributors: IAIK, A-Sit
In addition , a great number of people helped with formatting, bug hunting, etc.

Comments 2
The comments section is closed for articles published more than a year ago. If you'd like to inform us of any issues, please contact us.
Antonio Prado •
Hi, thank you for your effort. Just to note that the mailing list link is not working. Thank you -- antonio
Mirjam Kühne •
Sorry, my bad. Should work now.