This is an experiment to see if we can increase the capacity and resiliency of the RIPE NCC's authoritative DNS service (AS197000). This service hosts all the reverse DNS zones, ripe.net and provides secondary service for various ccTLDs.
RIPE NCC's Authoritative DNS Service
The RIPE NCC operates two distinct DNS services. One of these, K-root, is well known. However, although the other service is less well known, it is just as important as K-root, if not more so.
The authoritative DNS service (or AuthDNS) carries over 4,000 zones, including:
- ripe.net and other RIPE NCC infrastructure domains
- The reverse DNS zones of address space allocated to the RIPE NCC (eg. 193.in-addr.arpa)
- The reverse DNS zones of address space allocation to the other RIRs (secondary DNS)
- Over 30 ccTLDs (secondary DNS)
- ENUM (e164.arpa)
- Large reverse DNS zones of some of our LIRs (only if the zone is for an IPv4 /16-sized prefix, or a /32-sized IPv6 prefix)
- Some miscellaneous infrastructure domains, such as root-servers.org and as112.net
AuthDNS is quite distinct from K-root. It has its own AS number (AS197000) and address prefixes and its routers and servers are separate from those of K-root. So, apart from some common elements in our configuration management, K-root and AuthDNS are completely independent.
Current Locations and Query Load
This AuthDNS service is currently anycasted from three locations in Europe:
- Amsterdam
- London
- Stockholm
At each site, we have networking gear connected to three servers. These nine servers across three sites handle about 90,000 q/s, with peaks of over 120,000 q/s.
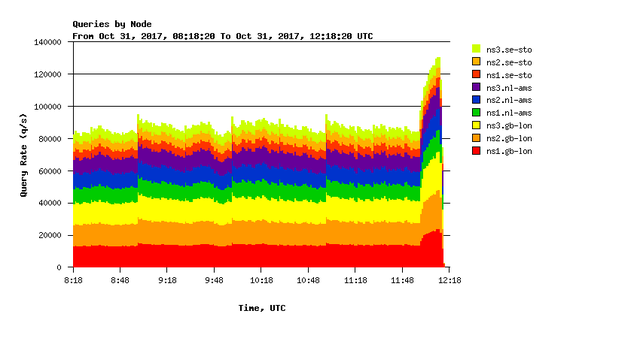
Wider Anycast Experiment
While our three locations are serving us fairly well, we feel that we can add even more capacity to this service by introducing more locations. This would also provide more DDoS resiliency, while lowering the latency from DNS resolvers to the zones hosted on this service.
We have been quite successful at increasing the K-root network by cooperating with hosts who provide a single server in their network, from which to announce K-root prefixes. We are therefore about to start an experiment using a similar model of deploying a single server, which provides the DNS service as well as handling the BGP peerings. Our host for this experiment is Anexia IT, which has its main office in Vienna. We will start by announcing AuthDNS prefixes from a server in their network in Vienna, and observe the effects of it on routing, query load distribution and any other effects. We expect to run this experiment for three months, at the end of which we can decide if this model is worth pursuing.
If you have any questions of comments about the experiment, or would like to find out more, please feel free to let us know in the comments section below.


Comments 8
The comments section is closed for articles published more than a year ago. If you'd like to inform us of any issues, please contact us.
Brett •
Can you provide any more in depth detail about the technologies and configuration you use.
Romeo •
Hi Brett, this article is only an announcement to inform the community that we have started this experiment. We will have more technical information and share our further planning in a later stage. Regards, Romeo
randy •
good move! but how about some nodes outside of europe? folk need to resolve reverses all over the internet.
Romeo Zwart •
Hi Randy, If this experiment works out as expected, we will be open to add locations globally, much like we do with K-root. This is in fact one of the reasons why we want to take this approach, because it will allow us to improve our reachability in other regions quite easily.
Besmir Zanaj •
Looking forward for the experiment's results. Where do I find that chart in ripestats? Thank you
Romeo Zwart •
Hi Besmir, As mentioned above, we will have more details later. The chart above is currently not publicly available.
danilo cicalese •
Hi Anand, it's really interesting. I am curious how you decided the location. It seems the ~45% of the request are served from the servers in London. Best, Danilo
Romeo Zwart •
Hi Danilo, The location of this new, experimental, node was not chosen for any specific reason. It is an experiment and as such could have been done in other locations as well. The location of the other service clusters is mostly 'historical'. Amsterdam and London where the first two locations where K-root started, so many many years ago it was a relatively simple next step to add a second DNS cluster to those locations. The Stockholm node was added some time later as part of a broader effort to add more resilience to RIPE NCC's services. Romeo