After the DNS root zone was finally signed and a number of TLDs began signing their zones, we were curious to see how many clients actually request DNSSEC information. First we looked at our server that provides secondary service to several ccTLDs.
This server answers some 5000 queries per second on average. Here is the percentage of those queries that requested DNSSEC information in August 2010:
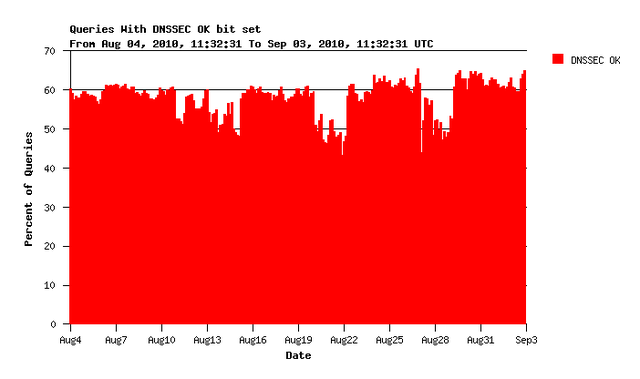
Figure 1: Queries with DNSSEC OK bit set
More than 50% of all queries request DNSSEC information from this server. This is quite encouraging. However, we do not know what the clients do with this information when they receive it.
We noticed a weekly pattern in the graph and investigated a little. Comparing this pattern to the query type looked promising:
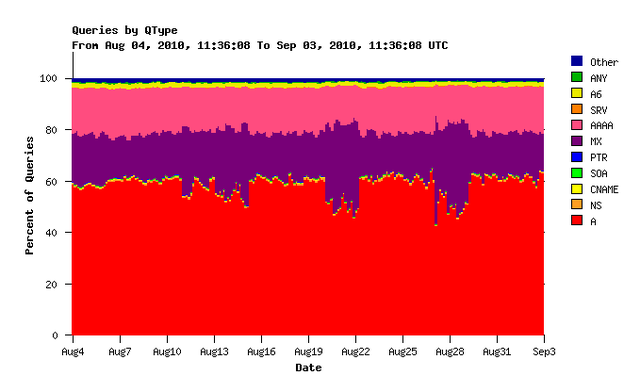
Figure 2: Queries by QType
It seems that the number of queries for mail servers (MX record queries) has a similar pattern. Looking at queries for MX records only confirms this:
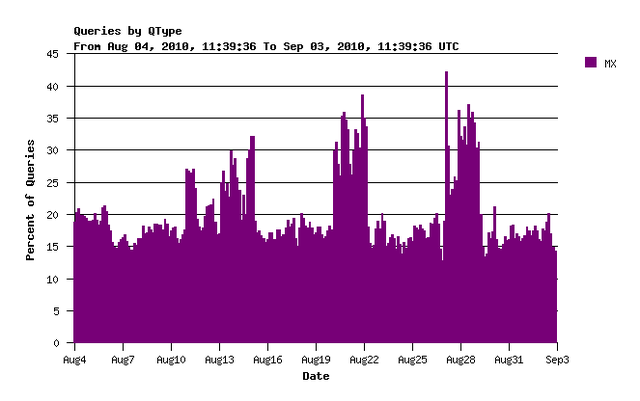
Figure 3: Queries for MX Records
On weekends we see relatively more queries for MX records and relatively fewer requests for DNSSEC information. Whether these MX queries are those that do not request DNSSEC information needs further investigation. However from my personal experience of receiving more SPAM during the weekend than during the week there certainly are a few hypotheses we could investigate here ....
Let us complete the picture with data from some other RIPE NCC servers. Queries arriving at servers for reverse DNS zones show a similar picture with a slightly different pattern:
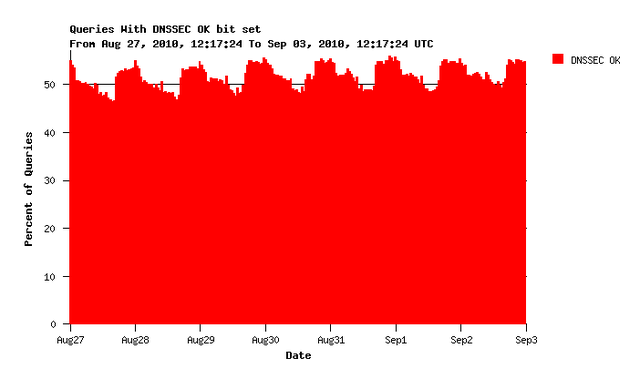
Figure 4: Reverse DNS zone queries with DNSSEC OK bit set
Still about 50% of all queries request DNSSEC information but the patterns are reversed and not quite weekly. Interesting ...
Looking at k.root-servers.net the picture is a little less constant:
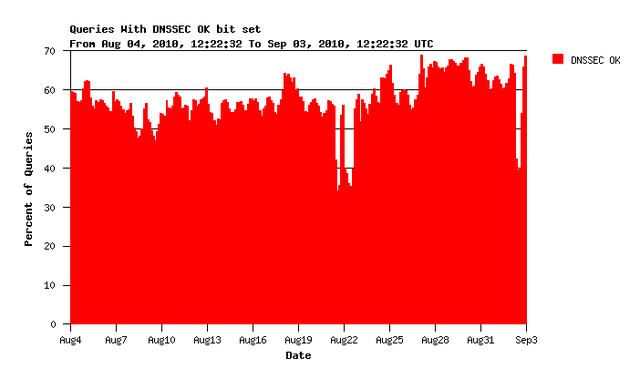
Figure 5: Queries with DNSSEC OK bit set as seen on k.root-servers.net
Again some weekly patterns and normally more than 50%. Root name servers receive more 'anomalous' queries than other servers, a phenomenon often referred to as 'junk'. These queries often arrive at a very high rate and constitute a large percentage of the total load. Consequently a few sources or types of junk queries can influence measurements like this in a big way. The three large dips in this graph, for example, are caused by a high volume of non-EDNS0 queries with a single source address.
In conclusion we can say that the servers we operate consistently receive requests for DNSSEC information with more than half of the queries they answer. That is encouraging.



Comments 3
The comments section is closed for articles published more than a year ago. If you'd like to inform us of any issues, please contact us.
Anonymous •
Just looking at the "DO-bit" tells very little about the amount of resolvers that actually validate, as you already indicated, especially since it is the default of BIND for quite some time.<br /><br /><a href="http://newsgroups.derkeiler.com/Archive/Comp/comp.protocols.dns.bind/2010-06/msg00058.html" rel="nofollow">http://newsgroups.derkeiler.com/[…]/msg00058.html</a><br /><br /><br />
Anonymous •
i concur and would like to add that a client in the scope of a DNS Root nameserver usually is a recursive nameserver acting on an endusers behalf, even if DNSSEC information is passed on to say a Desktop OS it does not mean that this information will actually be evaluated.
Anonymous •
Of course you are both right. We want to look at the actual DNSSEC queries in a later study. But seeing that more than half of the resolvers are requesting the info is noteworthy by itself.