North Korea is one of the most secluded countries in the world, but it is nonetheless connected to the Internet. We investigate North Korea's Internet connectivity in light of recent outages and discuss the fragile nature of its setup.
North Korea (officially Democratic People's Republic of Korea ) is one of the most secluded countries on Earth , so it's not surprising that the statistics on Internet coverage are quite low and information about the structure of the network is scarce. If we look in BGP, the Internet's traffic signalling system, we find only 1,024 IPv4 addresses registered to a single organisation in North Korea ( Star Joint Venture ( AS131279 ) ), a country of 24.9 million people . In BGP data, we see that this network is connected to the rest of the Internet via a single upstream network, China Unicom ( AS4837 ).
BGP doesn't allow us to see if the connectivity between Star and its international connection consists of a single or multiple physical connections, nor what the capacity of this interconnection is.
No matter how well provisioned the connectivity of North Korea is to China Unicom, having only a single connection in and out of a country is not the best recipe for stability and resiliency. It reminds me a bit of the isle of Mont Saint-Michel , where historically high tides could cut off the only road connecting it to the mainland.

Figure 1: "MtStMichel avion". Licensed under Public Domain via Commons - https://commons.wikimedia.org/wiki/File:MtStMichel_avion.jpg#/media/File:MtStMichel_avion.jpg
In addition to the stability issues inherent in having a single upstream, North Korea's Internet could have been better had it not attracted so many digital adversaries in recent years. Until recently, the country's Internet had been characterised as
"usually stable"
from outside observation, but the connection now appears increasingly unreliable. Infamously, North Korea's Internet suffered from an extended outage, rumoured to be the result of retaliation for the Sony Pictures hack. In other cases, vigilantes have claimed responsibility for downtime.
In the absence of being able to directly observe North Korea's Internet, researchers have previously searched for alternative and hidden links outside of the country. In the past, Star has maintained backup satellite links through Intelsat that were observable through BGP.
In the absence of transparency and access, some have engaged creative measures such as port scanning North Korean addresses to search for clues about the network. Still more can be done with a lighter touch through the measurements and data provided through RIPEstat and RIPE Atlas.
Is Kim Jong-un using one of these 1,024 addresses?
Interesting question. If you are aware of many people that might want to disturb your Internet communications, would you rely on a single link? Would you clearly label all your possible means of communication as yours? I would not, and I suspect the leadership of North Korea wouldn't either. If the 1,024 addresses that are officially registered to Star Joint Venture in North Korea aren't the only ones in use in North Korea, can we identify the rest of these addresses?
There are various sources of information that help determine in what country IP addresses are in use. First, there is the information from the Regional Internet Registry (RIR), APNIC in this case. APNIC has so-called delegated files that associate Internet resources with countries (or economies as they are called in the APNIC region) and a whois database (officially called the APNIC WHOIS Database). The second source of information are GeoIP providers that rely heavily upon the RIR-provided information, which they enrich with finer granularity data.
Using these data sources, researchers have found Internet addresses registered under names associated with the state-owned Korea Post and Telecommunications Corporation (KPTC) within blocks assigned to China, and still others have found addresses belonging to satellite service providers labelled as North Korean customers in their registration. This latter one at least looks to be stale.
While looking at BGP outages of the North Korean Internet, we found an interesting pattern. Figure 2 shows the availability of the four official North Korean prefixes, as well as two Chinese prefixes. The first of these is the block mentioned in the previous paragraph, and sifting through our BGP data we found the second Chinese prefix that shows the same outage pattern. Note that although the outage pattern is similar for these two new prefixes, it is not exactly the same.
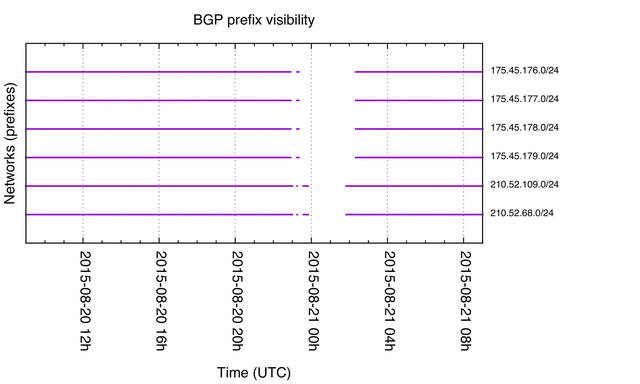
Figure 2: Prefix visibility in BGP for six prefixes around 20 August 2015
Of course, co-occuring outages are far from conclusive evidence of a common root cause of these outages, and for another North Korean outage on 10 August the two Chinese prefixes don't show the same behaviour.
North Korean DNS resiliency
The Domain Name System (DNS) is another fundamental part of the Internet. North Korea has the country top-level domain .kp and using the dig command line tool , we find the following information about it:
e1000$ dig kp. @k.root-servers.net ns
; <<>> DiG 9.8.3-P1 <<>> kp. @k.root-servers.net ns
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 1654
;; flags: qr rd; QUERY: 1, ANSWER: 0, AUTHORITY: 2, ADDITIONAL: 2
;; WARNING: recursion requested but not available
;; QUESTION SECTION:
;kp. IN NS
;; AUTHORITY SECTION:
kp. 172800 IN NS ns1.kptc.kp.
kp. 172800 IN NS ns2.kptc.kp.
;; ADDITIONAL SECTION:
ns1.kptc.kp. 172800 IN A 175.45.176.15
ns2.kptc.kp. 172800 IN A 175.45.176.16
As you can see, both IP addresses responsible for the .kp domain are in the same IP prefix (175.45.176.0/24). So if that gets disconnected from the Internet, the rest of the Internet can't look up domains in the .kp zone from the authoritative source any more.
The Internet Engineering Task Force (IETF) has produced a set of best current practices for DNS server placement ( RFC2182/BCP18 ) that advises DNS setups to be geographically and topologically dispersed. From that RFC:
When selecting secondary servers, attention should be given to the various likely failure modes. Servers should be placed so that it is likely that at least one server will be available to all significant parts of the Internet, for any likely failure. Consequently, placing all servers at the local site, while easy to arrange, and easy to manage, is not a good policy. Should a single link fail, or there be a site, or perhaps even building, or room, power failure, such a configuration can lead to all servers being disconnected from the Internet.
A recommendation to the operators of the .kp zone would be to increase topological and geographical diversity in the name servers, which would make the .kp zone less prone to outages.
Also interesting is the DNS SOA record:
e1000$ dig kp. @ns1.kptc.kp soa
; <<>> DiG 9.8.3-P1 <<>> kp. @ns1.kptc.kp soa
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 18700
;; flags: qr aa rd; QUERY: 1, ANSWER: 1, AUTHORITY: 3, ADDITIONAL: 3
;; WARNING: recursion requested but not available
;; QUESTION SECTION:
;kp. IN SOA
;; ANSWER SECTION:
kp. 432000 IN SOA ns1.kptc.kp. root.kptc.kp. 2013083001 28800 7200 1209600 86400
;; AUTHORITY SECTION:
kp. 432000 IN NS ns1.kptc.kp.
kp. 432000 IN NS ns2.kptc.kp.
kp. 432000 IN NS ns3.kptc.kp.
;; ADDITIONAL SECTION:
ns1.kptc.kp. 432000 IN A 175.45.176.15
ns2.kptc.kp. 432000 IN A 175.45.176.16
ns3.kptc.kp. 432000 IN A 175.45.178.173
We've highlighted some interesting properties here. First the 2013083001 serial number. DNS operators can put in pretty much any numbers they want, as long as an updated zone gets a higher number than the previous. But often DNS operators embed the date of update in the zone. If the .kp operators also do this, that would imply that this zone has not been updated since 30 August 2013, roughly two years ago.
The other interesting part here is that there appears to be a third nameserver ns3.kptc.kp ( 175.45.178.173 ) . We couldn't get any DNS answers from that server, so we assume it is either filtered or simply doesn't exist anymore.
Combining DNS and BGP data
This month (August 2015) we already detected multiple outages of all of the official North Korean Internet; RIPEstat allows anybody to track the status of this in near realtime here: stat.ripe.net/KP
We don't know the cause of the BGP outages, but we can speculate. They could either be due to the intention of the operators of the infrastructure to shut it down, for instance to stop users from accessing information on the Internet, or even for maintenance. It could also be unintentional, for instance due to an attack by a digital adversary.
As part of isnorthkoreaonline.com , we have long-running measurements of the two responsive DNS servers, ns1.kptc.kp and ns2.kptc.kp, from RIPE Atlas probes. Combining the data about the responsiveness of these servers with the outage data we have from BGP provides additional clues about the state of the North Korean Internet around the time of the outages.
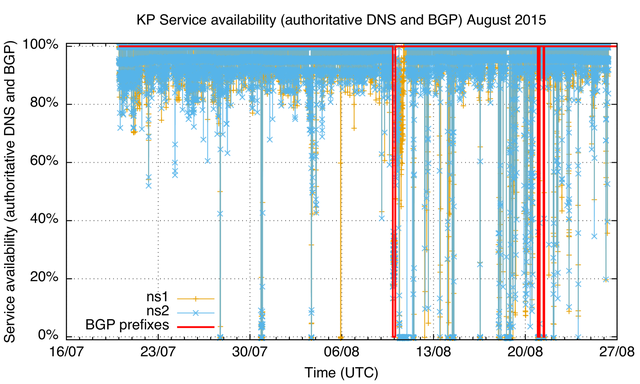
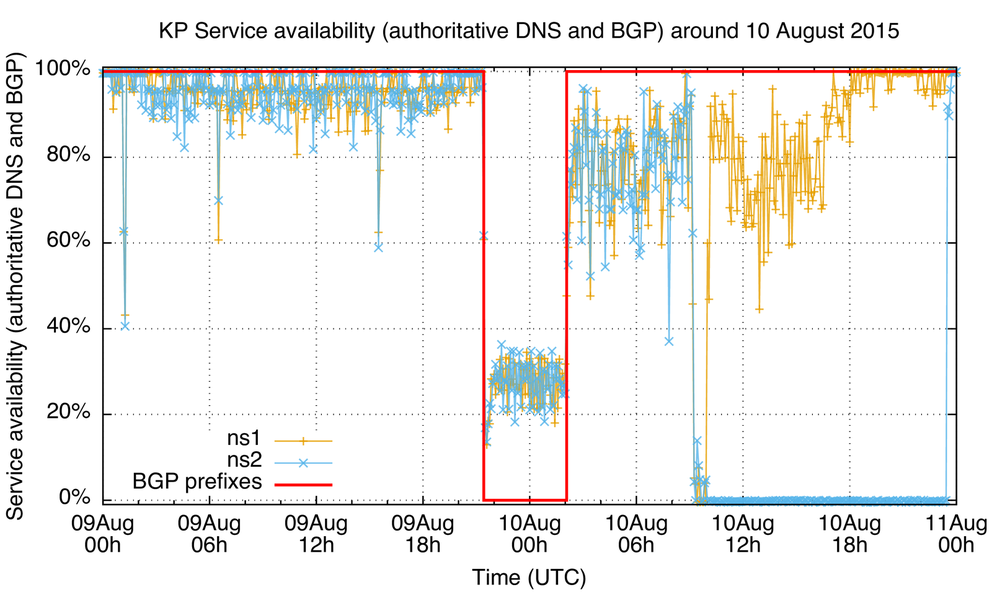
In Figure 3, BGP outages are marked in red (one around midnight 10 August, and two on 21 August). DNS server availability is measured as the percentage of DNS queries to this nameserver from RIPE Atlas probes that did not time out. So if nameserver availability drops to 0% that means that none of the RIPE Atlas probes in this measurement got a response from the nameserver. Before 10 August there are a few distinct drops in nameserver availability (we count three where both ns1 and ns2 were unavailable around midnight 28 July, 31 July and 4 August and one where ns1 was unavailable on 6 August). After the outage on 10 August, it seems the .kp nameservers are generally less available than before. We can speculate as to the cause of this: The DNS servers themselves are busier than before (either with an increased load of normal traffic, or attack traffic). Another possible cause could be the link into North Korea being saturated (again either with normal and/or attack traffic), which would cause packet drop, which causes service unavailability.
Figure 4 and Figure 5 are the same data but zoomed in to the outage periods. There are a couple of interesting things here. First, look at the service availability during the BGP outages: Notice anything weird? You'd expect 0% service availability, but in some 20%-35% of queries from the probes in these measurements both ns1 and ns2 seemed to respond! This could point at non-BGP routing, or an island of connectivity in BGP, that doesn't propagate reachability beyond the networks involved. An alternative explanation is that the responses during this outage are received from faked ns1 and ns2 servers (why?). After the outage, service availability is lower than before. At a certain point both ns1 and ns2 become unavailable, and ns2 stays unavailable for an extended period of time, while ns1 recovers earlier. Again, this could point at increased server load/link load that the nameservers had a hard time coping with.
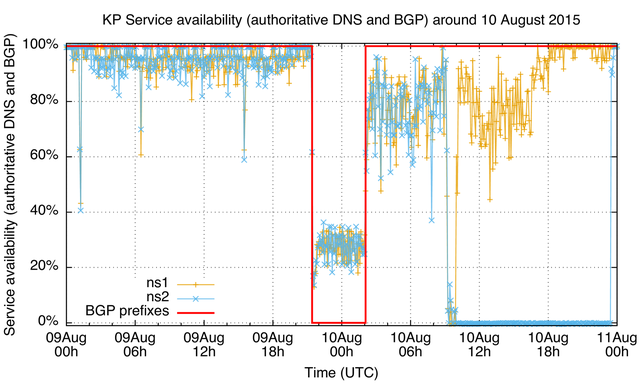
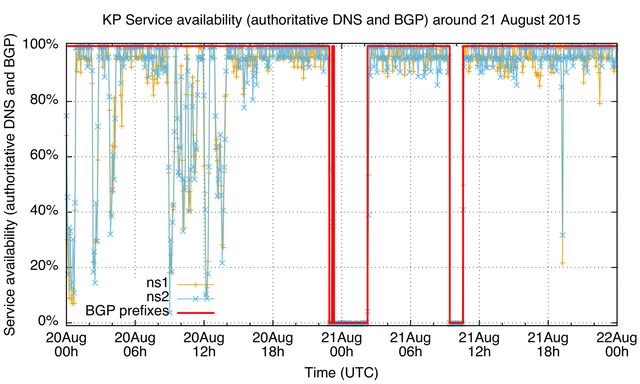
Figure 5: DNS server availability and routing status of North Korean prefixes in BGP around 21 August 2015
In Figure 5, we see DNS service being unavailable during the BGP outage, which is what you'd typically expect. On 20 August, you see downward spikes of nameserver unavailability that seemed to disappear later that day. Also note that the first BGP outage had an interesting start. Measured connectivity went down for 15 minutes and recovered for 20 minutes before the actual three-hour-long outage occurred. Such a signal could point at malfunction, not intent.
Brownout not Blackout?
The service availability during a BGP outage was interesting to investigate further, and as we also collected traceroute data during that outage we can actually see what that connectivity looked like. Figure 6 is a visualisation of that traceroute data (you can click on it to view a bigger version). As you can see there are multiple networks (ASNs) that had connectivity to the authoritative nameservers for .kp during the BGP outage on 20 August.
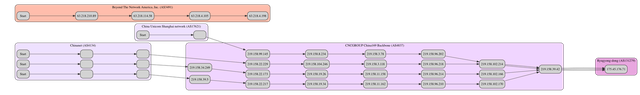
Figure 6: Traceroute visualisation for connectivity to the authoritative nameservers for .kp
Conclusion
We've noticed an increased interest in profiles of the Internet for specific countries. Because the North Korean Internet is technically not very complex, it's relatively easy to study it; and tools like RIPEstat and RIPE Atlas collect a lot of open and transparent Internet data that enable this. But even with this relative ease there are a lot of details that we don't have open and transparent data about. We'd be interested in having a conversation on how to enable open access to relevant Internet data for the purpose of informing network operators, policy makers and anybody else interested in building a better Internet.
If people are interested in collaboratively investigating this further, please have a look at the hackpad where we continue looking into this.




Comments 1
The comments section is closed for articles published more than a year ago. If you'd like to inform us of any issues, please contact us.
Ross •
Ask China Unicom customers to submit traceroutes from different points in China Unicom's network to the North Korean prefixes. That might help fill in more detail about the number of interconnections the two BGP ASs interconnect.