The advent of IPv6 changes not only the network components, but also the security field shifts. We see new types of attacks or at least variations of the attacks we know from IPv4. This article provides an overview of the IPv6 security vulnerabilities that arise with the launch of IPv6.
1. Attacks against the IPv6 protocol
1.1. Multicast
Via certain multicast messages an attacker can very fast do a reconnaissance attack on a local network. Simply pinging the all-nodes multicast address ff02::1 shows several machines that are alive. Additionally, some NMAP scripts can be used to reveal almost all IPv6 clients on the network via forcing them to generate new (temporary) IPv6 addresses via SLAAC. The corresponding Multicast Listener Discovery messages from the clients, which are sent via multicast, reveal their interface IDs.
1.2. Extension Headers
Inside extension headers an attacker can send information that remain undetected if the intermediary firewalls do not fully check the options of these headers. This kind of attack is called "covert channel". For example, inside the Hop-by-Hop extension header, the PadN option which according to the standard must contain zeros, can be filled with any characters. That means, hidden information can be sent via the network without touching the upper layer protocols.
Another vulnerability arises with the routing header 0 (RH0). With its usage, a Denial-of-Service (DoS) attack between two nodes or firewall bypassing strategies can be performed. But since
RFC 5095
deprecated the overall usage of RH0 in 2007, these attacks are not explained here one more time. (Please refer to the RFC for further details.)
2. Attacks against ICMPv6
ICMPv6 plays a key role in the proper usage of IPv6. Especially the Neighbor Discovery messages such as Router Advertisements (RAs) and Neighbor Solicitation/Advertisements (NS/NA) are needed for the straightforward usage of the new Internet Protocol.
2.1. Router Advertisement Spoofing
If an attacker sends spoofed Router Advertisements inside a subnet, all IPv6 nodes will immediately change their routing tables and store the attacker as one of the default routers. If they send traffic to the Internet, this new default router will be used. This leads to a situation in which the attacker can fully see (and even modify) all outgoing traffic from the IPv6 nodes to the Internet. This is called a Man-in-the-Middle (MITM) attack. Meanwhile the attacker can not see the returning traffic from the Internet since he is not able to spoof the real default router on the network. See Figure 1 below for an illustration of this attack.
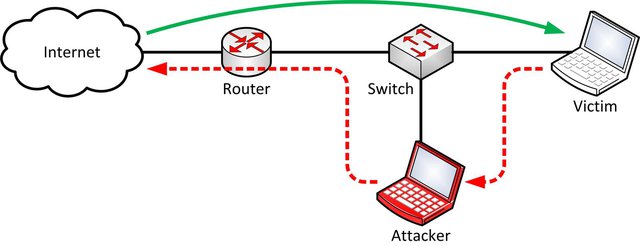
Figure 1: Router Advertisement Man-in-the-Middle Attack
2.2. Router Advertisement Flooding
The attacker can also flood many thousand RAs which immediately freezes all Microsoft Windows computers since they are completely overloaded with that many SLAAC processes. This bug is known for many years but still exploitable. That means: If an attacker has access to a local network and is not stopped by the intermediary switch while sending spoofed RAs, the complete Windows environment will be frozen!
2.3. Neighbor Discovery Spoofing
When the attacker spoofs certain Neighbor Advertisements, he can execute a MITM attack. By answering falsified Neighbor Advertisements to the issued Neighbor Solicitations from the victims, he redirects all IPv6 traffic over his "routing instance" in the same subnet (see Figure 2).
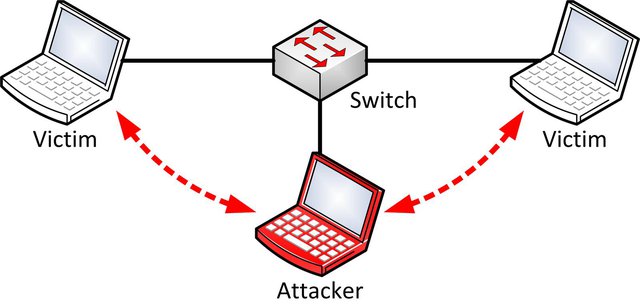
Figure 2: Neighbor Advertisement Man-in-the-Middle Attack
2.4. Duplicate Address Detection
A DoS attack is executed if the attacker answeres to all Duplicate Address Detection messages (DADs) from a new IPv6 node (with a not yet assigned IPv6 address). The node always believes that this address is already in use and will never get an available IPv6 address and is therefore unable to access the network. This situation remains until the attacker stops the attack.
3. Attacks against DHCPv6
3.1. Address Space Exhaustion
If the concept of stateful DHCPv6 is used, an attacker can exhaust the IPv6 address pool on the server, similar to a DHCPv4 server. Even though the DHCPv6 server could provide enough IPv6 addresses, it has to store a small binding for each address and the corresponding DUID from the client which will at least exhaust the memory of the server if it is flooded with many requests.
3.2. Rogue DHCPv6 Server
An attacker can also place his own DHCPv6 server inside a network and distribute falsified values, e.g. a spoofed DNSv6 server address. If the clients accept this DNS server, they will get falsified DNS responses from now on if the attacker also owns the spoofed DNS server. With this attack, internal IPv6 users can be redirected to other (web-) servers than they intended to access. The picture below shows the basic attack in the local network.
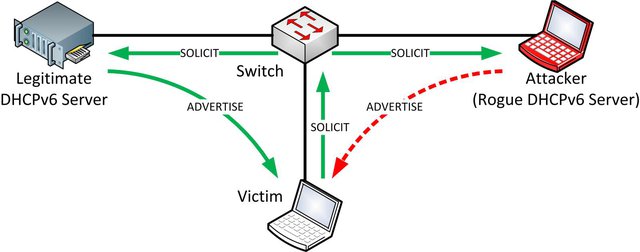
Figure 3: Rogue DHCPv6 Server
4. Attack Toolkits
In order to test own equipment and security appliances, the following IPv6 attack toolkits can be used:
- THC-IPv6 : The toolkit from Marc Heuse provides many easy to use tools which require almost only the specification of the network interface.
- SI6 Networks' IPv6 Toolkit : This package of tools from Fernando Gont can be used in a more precise manner since it can be fine-tuned with many options. Likewise it is more complicated to use compared to the THC-IPv6 toolkit.
- Scapy : To send completely crafted IPv6 packets, the packet manipulation tool Scapy from Philippe Biondi can be used.
5. Conclusion
From a top view, the vulnerability concepts have not changed that much with the advent of IPv6, while the concrete methods are modified to the new protocol. It was also possible in IPv4 networks to execute a Man-in-the-Middle attack on the local network or to spoof the DHCPv4 server. However, it will still take some time until all network and security devices have a full adoption of all IPv6 defense methods such as the RA Guard in switches or explicit Exentsion Header detection/filtering in firewalls.
Furthermore, some attacks are possible against the transition methods from IPv4 to IPv6 (not listed here) and of course IPv6 stack implementations in all operating systems will have errors. That means: Not only the generic IPv6 security issues shown in this summary are relevant for security experts, but also application specific vulnerabilities that are new due to the usage of IPv6.
Reference
This article is a summary of the master thesis from Johannes Weber " IPv6 Security Test Laboratory ". In the thesis, 20 IPv6 security attacks are explained in detail and three firewalls are tested in an isolated test laboratory (Cisco ASA, Juniper SSG, Palo Alto PA). The test results of these firewalls are shown in the thesis as well as all further references from the attacks.
About the author
Johannes Weber has a master's degree in IT-Security. In his master thesis he studied the details of IPv6 security, explained the appropriate tools and tested a few firewalls against these vulnerabilities. He is now working for the German TÜV Rheinland i-sec GmbH as a network security consultant.


Comments 3
The comments section is closed for articles published more than a year ago. If you'd like to inform us of any issues, please contact us.
Christian •
Hej, you might want to add SendIP to the list of tools for crafting IPv6 packets. http://snad.ncsl.nist.gov/ipv6/sendip.html Cheers
Johannes •
Hey Christian, thanks for your hint. I have not yet tried SendIP - but I will. (Until now, Scapy fitted for all may cases...) Regards, Johannes
Leonard •
Thanks for the information.