At the RIPE NCC, we get lots of requests for assistance from people dealing with online abuse. In this article, we clarify how you can use our tools to help resolve abuse issues, but also what you can do when further steps need to be taken.
As a Regional Internet Registry (RIR), we make certain information publicly available that can help you tackle online abuse. In particular, if you have some details about where the abuse is coming from, you can use our tools to find out who it should be reported to. In a moment, we’ll look at how that works.
Sometimes that’s enough, but sometimes you’ll need more assistance than we can provide. For that reason, we’ll also talk about further steps you might need to take and who else you can reach out to when such cases arise.
How Can the RIPE NCC Help?
Many Internet users have been on the receiving end of online behaviour that posed them harm – harassment, violation of privacy, loss of reputation, viruses, theft, etc. Depending on the type of abuse, and who’s targeted, the damage done can range from a small annoyance to significant trauma or major business impact.
Although there’s no fixed definition of what constitutes online abuse, and no one method for fighting it, one thing all cases have in common is that they have to originate from somewhere. And when we’re talking about the Internet, that means they have to have come from an IP address.
IP Addresses
IP addresses are usually thought of as the Internet equivalent to real-world addresses. Every packet of information being routed around the Internet has to have a unique IP address as its origin and another as its destination, so being ‘on the Internet’ at all means having a device with an IP address to and from which data can be sent and received.
Our job at the RIPE NCC is to register ranges of these addresses to our members, often Internet Service Providers (ISPs), who often then distribute addresses from those ranges to their customers. However, we do not provide Internet connectivity to these members (or their customers), and as such, we don’t have any say in what content is sent to or from a given IP address.
Since 2012, however, we do require that any member must provide an email address that can be contacted in case abuse is found to have originated from an IP address in a range registered to them. This ‘abuse contact’ is part of the information stored in the RIPE Database, and it can be used to help find out who to report abuse to when it happens.
1. Find which IP address might be responsible for the abuse
The first step is tracking down the IP address. You can do this if you know the domain name of the website or the email address that the abuse is coming from. Once you have this, go to RIPEstat to track down the IP address for that domain.
2. Find the holder of the IP address
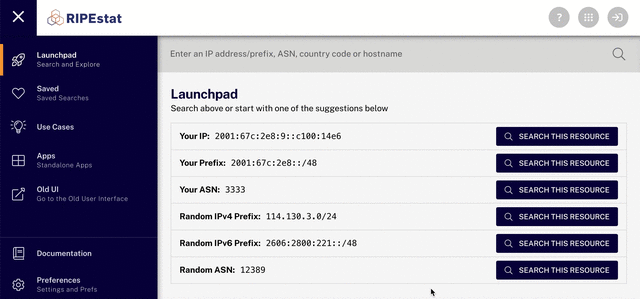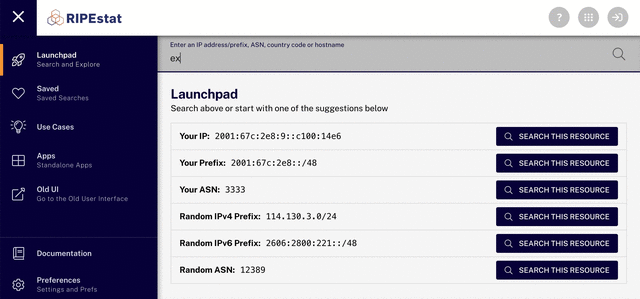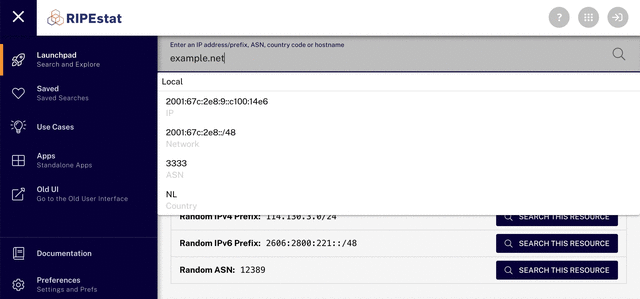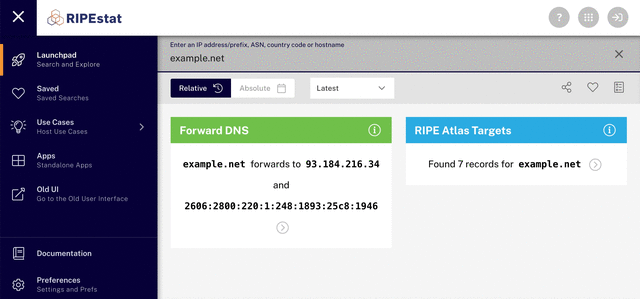
Once you’ve entered the domain in RIPEstat, you’ll see the IP address for that domain. Click it to get further information about the address, including the Autonomous System (AS) number for the network that announces that IP address.
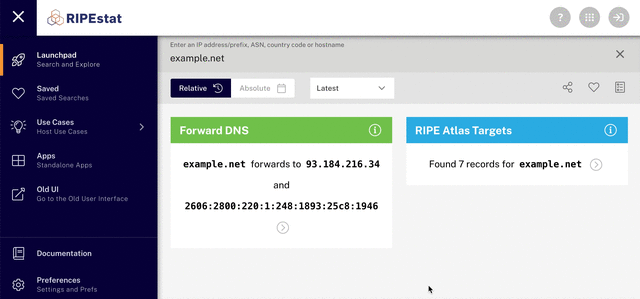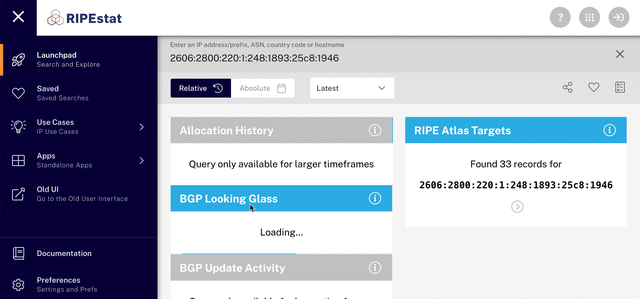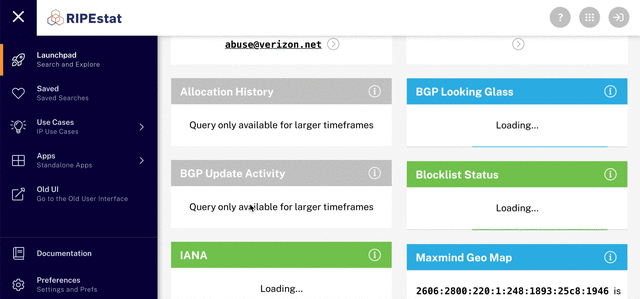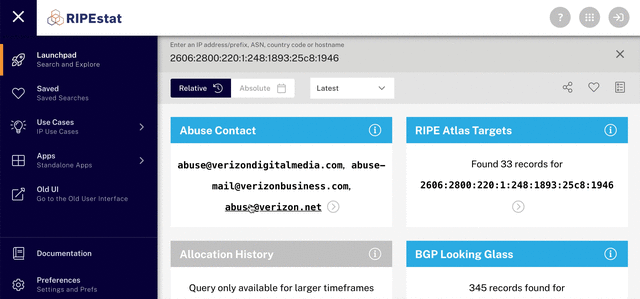
3. Find the abuse contact for a specific IP address
Among the information you see at this point, you’ll find the abuse contact infocard, which contains the abuse contact email address for the IP address you searched for. You can report the abuse you’re dealing with directly to this email address. More details about what to include in your report, along with some other useful information, can be found on our website.
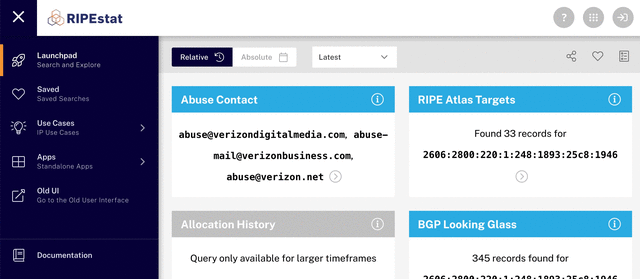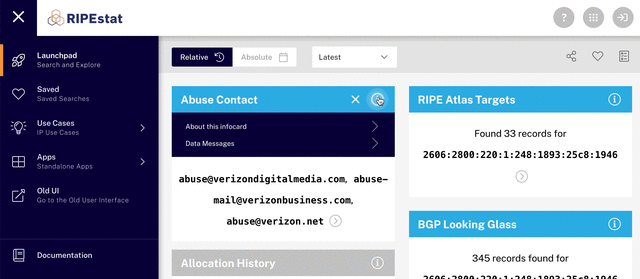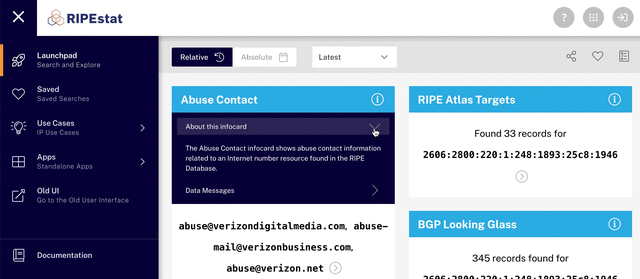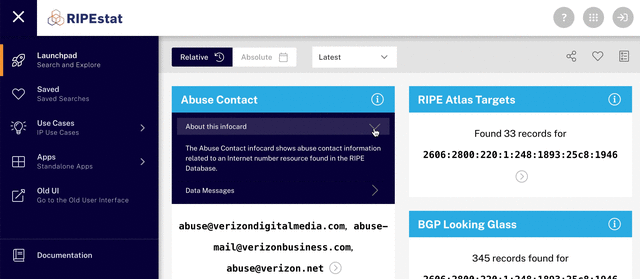
The IP address holder maintains the abuse contact information and the RIPE NCC performs a periodic validation of this abuse contact information. The validation verifies that the address is able to receive messages. You can contact us if an abuse contact is missing or appears to be invalid.
Please note that the above does not apply to:
- Legacy IP addresses and AS numbers, distributed before the RIPE NCC was created – this address space is not subject to RIPE policies. More information on legacy is available here.
- IP addresses and AS numbers distributed by other Regional Registries (AFRINIC, APNIC, ARIN, LACNIC)
This means that in some cases we cannot enforce the requirement of a valid abuse contact.
4. Additional contacts
If the abuse contact doesn’t respond, you could also try to contact the administrative (admin-c) or technical contact (tech-c) for the relevant IP address. These are also stored in the RIPE Database, and we can help you to find them if needed.
Taking Things Further
If all goes well, whether the abuse contact is the entity directly responsible for the abuse or not (for instance, the abuse may be due to the actions of their customer), reporting the issue should start a chain of communication that results in someone putting a stop to the behaviour in question. However, as we know, things don’t always go so smoothly. Sometimes nobody is home; sometimes they may pretend not to be.
When to Contact a Law Enforcement Agency
If harmful abuse persists despite efforts to contact the responsible party, it’s time to seek the support of Law Enforcement Agencies (LEAs). As stated in the advice provided by Interpol, the best place to start is by contacting your local police department. We would certainly recommend that anyone who is reading this right now and is the victim of serious abuse should contact the local police authorities as soon as possible.
Contacting LEAs in Other Countries
As well as contacting your local LEA, you may also wish to report abuse directly to the law enforcement agencies in the country where you believe the relevant network is based. There are certain resources out there that can help you do this. For example:
- Europol hosts an extensive set of information about Cybercrime and provides a list of LEA contacts for different countries
- Some other national authorities try to make this kind of information available as well – for instance, the FBI lists relevant field offices in the US
When reaching out to LEAs in other countries, it’s good to be aware that procedures can vary significantly. LEAs in different places have different requirements on how reports are submitted - for instance, they may restrict communication to specific parties by only allowing you to use specific channels or tools. They might have different thresholds for when reports of abuse need to be acted on, different privacy requirements, and so on. And while some countries have a dedicated team for fighting cybercrime, many do not.
All this can be difficult to navigate. However, many LEAs and inter-governmental organisations are working hard to improve cooperation and make the investigation and prosecution of cybercrime more straightforward. For example, the Council of Europe is supporting many ongoing projects aimed at capacity building to address cybercrime challenges, including a 24/7 network of points of contact for international cooperation in such investigations.
Anti-Abuse
The RIPE community and the RIPE NCC are both very actively involved in supporting anti-abuse measures. The RIPE Anti-Abuse Working Group is continuously providing input on abuse handling and how to fight it at a technical level. And here at the RIPE NCC, we’re actively participating in discussions with LEAs and other parties about possible improvements in abuse handling and the fight against cybercrime.
That said, our role in all this as an organisation is to make sure that abuse contact information for holders of the IP addresses we distribute is readily available to the public. The information we make available on our website and tools like RIPEstat are there to ensure this. But ultimately, it is important to end by noting that we have no direct mandate to act on behalf of third parties by taking part in disputes or filing reports. It’s the responsibility of network operators to follow up on any abuse reports they receive. And while many network operators take that responsibility very seriously, being good netizens (and with certain incentives to do so), there will always be cases where reports get ignored. We very much hope that the information we’ve provided here will help you take the appropriate steps if you find yourself in such a situation.



Comments 2
The comments section is closed for articles published more than a year ago. If you'd like to inform us of any issues, please contact us.
Daniel Karrenberg •
Very nice article considering that you have to say 'Do not call us!'. ;-) When using IP addresses to identify the source of abuse it is important to keep in mind the possibility of the source address being 'spoofed'. Especially in denial of service attacks what appears to be the address of the source may in fact be the address of the victim. Designers and implementers of automated processes that use IP addresses should take great care about the semantics of IP addresses too. As an author of RFC1918 I regularly get e-mails from automated tools asking me to stop hacking or attacking someone. The only positive development here is that I have not had a query from an LEA about private IP addresses in the past two years or so.
Angela Dall'Ara •
Hi Daniel, many thanks for your comment. Very useful information. The RIPE NCC abuse contact is registered in the parent block for all IP ranges, so we also receive many automatically generated reports where it's assumed we are the malicious party. Reporting systems could definitely be improved :-)