With the increased deployment of IPv6, we were curious to see how much the amount of spam sent over IPv6 increases.
We looked at the e-mail system of the RIPE NCC and produced some statistics that could be seen as an indication for the overall trend of spam sent over IPv6.
After we evaluated one week’s worth of data, we observed the following [please note that this excludes messages already rejected by blacklisting and greylisting (more on this below)]:
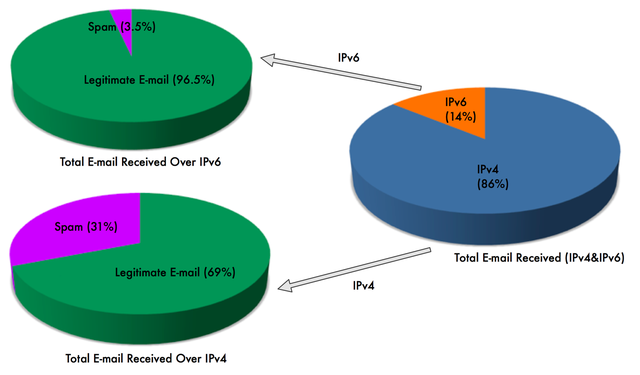
Figure 1: Number of spam emails received in one week
Figure 1 shows that:
- Out of the total number of emails received, 14% were received over IPv6, the rest over IPv4.
- Looking only at the number of emails received over IPv4: 31% were classified as spam, the rest were legitimate.
- Looking only at the number of e-mails received over IPv6, 3.5% were classified as spam, the rest were legitimate.
If we now take into account the total number of spam emails received, we observe the following:
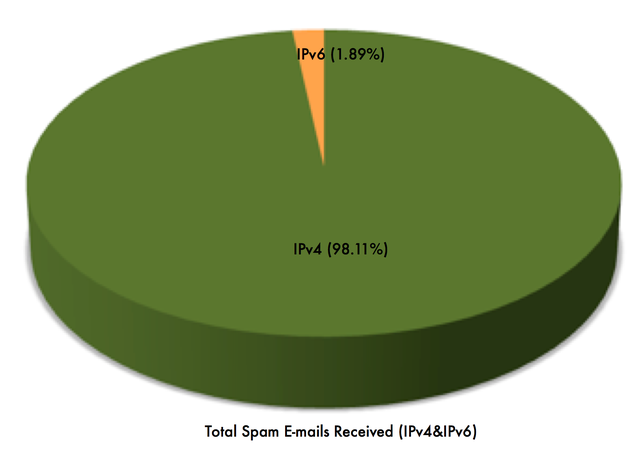
Figure 2: Total spam e-mails received (over IPv4 and IPv6)
Figure 2 shows, that out of the total number of spam emails, 1.89% were received over IPv6, the rest were received over IPv4. The data above shows that the percentage of spam in IPv6 is much smaller than the percentage of spam in IPv4 (not surprisingly). We will observe how the relation between IPv4 spam and IPv6 spam evolves over time. In order to achieve this, we produced the graph (Figure 3) that shows in real-time the number of spam emails received over IPv4 compared to those spam e-mails received over IPv6.
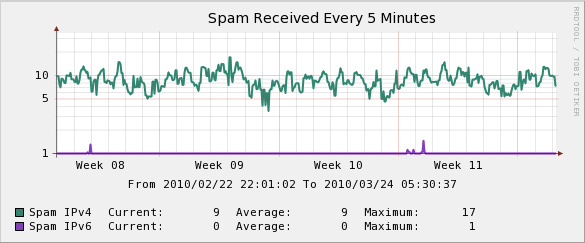
Figure 3: Amount of spam received over IPv4 vs. spam received over IPv6
The graph in Figure 3 is produced by looking at the total number of spam emails received in five minutes for both IPv4 and IPv6.
- IPv4: An average of nine spam emails were received within five minutes
- IPv6: An average of nearly zero spam emails were received within five minutes
The graph above shows a period of three weeks, although we will be examining longer periods of time in the future. It will be interesting to see the evolution of spam over both IPv4 and IPv6 over a longer period of time (months and years).
It might also be interesting to note that we did not observe any spam sent over 6to4 or Teredo.
Methodology
Our measurements of spam sent over IPv4 appear to be much lower compared to other sites. This is because our measurement methodology does not include spam that:
- Is on DNS Blacklists
The RIPE NCC mail system rejects spam sent from hosts listed on the DNS blacklists (no further SMTP is carried out), including multiple spamming attempts.
- Is sent to non-existent email addresses
Our mail system refuses connections trying to deliver spam to non-existent email addresses within the ripe.net domain. Since we wouldn’t have received the email anyways, we don’t take these spam emails into account in our measurements.
- Is Greylisted
We use a method of greylisting for a subset of our email addresses (see: http://en.wikipedia.org/wiki/Greylisting for a description of this method). Using greylisting also filters out a significant portion of spam.
Additionally, our statistics only take our primary MX system into account (and not email sent from the secondary MX system to the primary).
We are not the only ones looking into this. After a discussion on the IPv6-ops mailing list , Tim Chown of the University of Southampton did some measurements on his campus network and presented the results at UKNOF in May 2008 (see " IPv6 Experience at a campus site "). However, we are not aware of any recent statistics on spam and IPv6.
Future Developments
We will continue to collect these statistics to track the increase in spam sent over IPv6, and potentially whether this means that the amount of spam sent over IPv4 decreases. DNS blacklists (DNSBLs) are one of the counter-measures used extensively to block spam sent over IPv4, though not without controversy [see (1) and (2) ].
The effectiveness of DNSBLs to block spam sent over IPv6 is even more controversial because the probability of false positives is higher [see a recent discussion about this here ].
At the moment, the only DNSBL for IPv6 we are aware of is http://virbl.bit.nl . The idea for this interesting initiative was born during RIPE 48 (Note that it was actually created to list viruses, not spam).
We expect to see the amount of spam sent over IPv6 to grow over the next few years. The use of reputation systems in general, and DNSBLs in particular, are not widely used yet in IPv6, because of the concerns mentioned above. Also, with the number of addresses available in IPv6 (also for spammers), the use of DNSBLs is not seen as effective enough.
This means that we might have to adjust the reputation based mechanisms such as DNSBLs to the particular characteristics of IPv6. Depending on how this adaption evolves and how effective it proves to be, we might have to rely more on email content scanning and less on reputation-based mechanisms to counter the expected increase of spam in IPv6.
At the moment these are open questions. We will follow the developments and will keep you informed about this topic on RIPE Labs.


Comments 6
The comments section is closed for articles published more than a year ago. If you'd like to inform us of any issues, please contact us.
Anonymous •
<div class="content legacycomment"> <p> The IPv6 spam can be the two types. </p> <p> </p> <p> First, is when the mail is sent from dual-stack PC and the spammer don't care about IPv6 at all. The example is mail from infected PC, such as from botnet. The spamming software send the mail through mail client of the infected user, and if PC is dual-stacked and target is IPv6 capable, the letter will fly through IPv6, BUT the sammer even don't know about it. </p> <p> </p> <p> Second, if the spammer care about IPv6 and use it as there is less anti-spam filters can work with IPv6 mail. </p> <p> </p> <p> What kind of IPv6 spam is growing now? </p> <p> </p> </div>
Anonymous •
<div class="content legacycomment"> <p> Hello Max, </p> <p> </p> <p> That's a very good point. Good observation. </p> <p> </p> <p> The type of analysis that we carried out doesn't differentiate between those two scenarios that you present. We analyse the activity on our side, the incoming connections and its type (IPv4 or IPv6). </p> <p> </p> <p> In order to distinguish between intentional/aware and unintentional/unaware IPv6 connections we would have to carry out a completely different type of analysis. </p> <p> </p> <p> If someone already has some information, statistics, trends, etc it would be very interesting to have a look at it. </p> <p> </p> <p> Thank you very much for the feedback. </p> <p> </p> <p> Regards, </p> </div>
Anonymous •
<div class="content legacycomment"> <p> Interesting article, I'm surprised it's not being tracked more. </p> </div>
Anonymous •
I find it entertaining that this article about email spam has got a couple of unmoderated comment spams. The comments have links converted to URLs, which presumably is attractive to spammers.
Anonymous •
Oops. Thanks for pointing this out. I removed these comments now.
Mohammed Habib •
I'm trying to look on the problem of how can we improve the use of IP Block lists as a mechanism to prevent spam on IPv6 and the issue as it been addressed by many is the huge address space in IPv6 which would not the existing technique feasible. I have just started preparing a proposal for a PhD ... But I'm willing to get corporation or atleast suggestion because I'm not the expert in the area. here's my contact mhabib1981 -at- gmail