Taking down malicious websites means understanding which geographical regions or IP ranges can access them. RIPE Atlas can help collect the technical evidence needed to determine the geographic reach of a malicious site and provide accurate, location-based reports for its takedown.
In this article, we explore how RIPE Atlas - a network of probes that allows geographically distributed Internet measurements - can be put to use in assessing the persistence and geographic reach of malicious sites.
Key information for investigating a malicious site
An investigation into a malicious site should collect, at a minimum, the following information:
- Relevant dates: discovery, creation of the domain, takedown, etc.
- Domain name(s)
- URL
- IP addresses
- Source code
- Screenshots or videos of the behaviour
- Contact details: domain registrant, holder of the IP address, CSIRTs/CERTs, etc.
Sometimes, phishing or malicious websites adopt mechanisms that obfuscate such information, so complicating their takedown. This includes the use of CDNs or hosting providers with identity protection for the site owner, or geo-blocking where the site is only accessible from specific geographic locations. However, when reporting a malicious site, it’s important to include the geographic location from which the malicious content is accessible. This allows those receiving the report to replicate the malicious behaviour that is being reported.
There are different methods for determining which locations can access the malicious content. One option would be to use VPN services or proxies, which provide an IP address corresponding to the country where we want to verify the malicious behaviour. In this article, however, we’ll explain how to achieve this using RIPE Atlas.
What is RIPE Atlas and how can it help?
RIPE Atlas is a network of globally distributed probes that continuously measure Internet connectivity and performance, providing technical information about its operation. It also allows for the performance of user-defined measurements toward specific destinations. The different kinds of measurements that can be performed with RIPE Atlas probes are as follows:
- PING
- Traceroute
- DNS
- TLS
- HTTP (only for anchors)
- NTP
As well as providing different ways to measure the state of the Internet, a particularly interesting feature of RIPE Atlas is that each probe acts as a vantage point from a known location on the Internet. This is especially useful for the analysis of malicious sites, since knowing the location from which a measurement was taken lets us determine whether the site is accessible from that part of the world. This feature allows us to determine if a phishing attack is geographically targeted.
Using RIPE Atlas to analyse malicious sites
Of the various measurement types available in RIPE Atlas, the following four are particularly useful when it comes to the analysis of malicious websites: PING, Traceroute, DNS, and TLS. Before we get into how each of these contributes to the analysis of malicious sites, let's start by looking at how to create measurements in RIPE Atlas (more details are available in RIPE Atlas documentation).
Assume we have a basic malicious website identified by a domain name and, optionally, a basic path. For example: http[s]://example.com/recurso_malicioso. To start examining the site with RIPE Atlas, you’ll need an account at https://atlas.ripe.net/. Once logged in, go to “Measurements” and then “Create Measurement”:
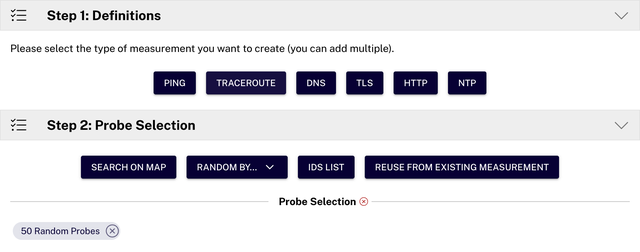
Select the desired tool: PING, Traceroute, DNS, or TLS (the specifics of each method will be explained below).
Then select the probes that will participate in the measurements, aiming for a uniform geographic distribution. Probes can be selected manually on a map or randomly. By default, a single measurement is configured, and the corresponding cost (in credits) is displayed.
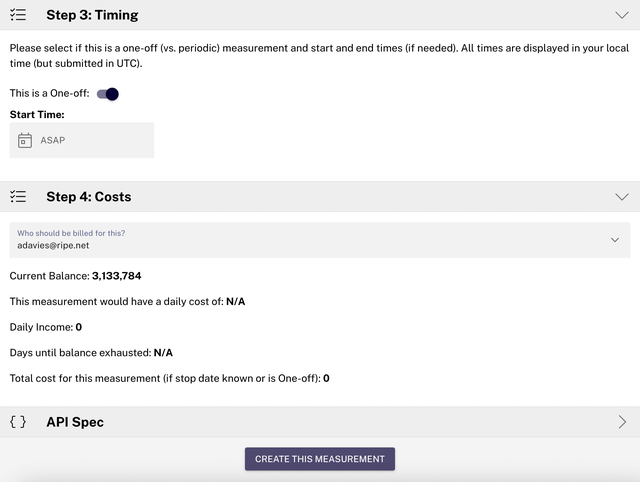
Once the telemetry is created, the probes will start taking measurements. Keep in mind that the time it takes to obtain results depends on how quickly all the probes complete the requested task.
So how do each of the measurement types contribute to the analysis of malicious sites?
PING
This method uses ICMP messages distributed across the probes. It’s useful for identifying which probes can reach the suspicious IP address. Keep in mind that this option is effective when the malicious content is hosted on a single IP address that doesn’t share content.
Periodic scans can be scheduled to check whether the IP address remains active. It should be noted that not all servers respond to ICMP requests, so local tests must be run before using Atlas to measure the malicious site.

DNS
This is an interesting option, as it allows for highly customised DNS measurements. It’s useful for analysing how DNS responses vary depending on the geographic area where the probes are located. Periodic measurements can be scheduled to follow the evolution of the IP addresses used by attackers and monitor the lifetime of the malicious domain.
This option is valuable for conducting highly customized DNS measurements and allows analyzing how responses vary based on the geographic location of the probes. Additionally, by scheduling these measurements periodically, it’s possible to track the evolution of the IP addresses used by attackers and monitor the lifetime of malicious domains.
Traceroute
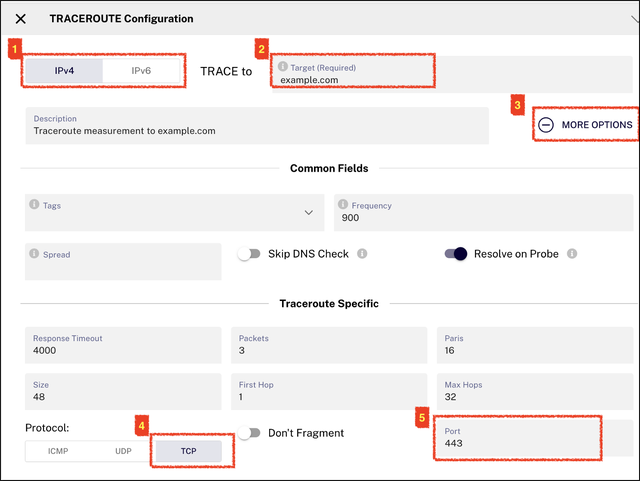
If this method is selected, the probes will perform a traditional traceroute test, which consists of sending a sequence of ICMP, UDP, or TCP packets with increasing TTL (Time To Live) values until the destination is reached. For our purposes, we will select the TCP protocol and use port 80 or 443, depending on whether the malicious site uses HTTP or HTTPS, respectively. We must also select either IPv4 or IPv6, as appropriate. It’s possible to include multiple measurements in a single telemetry session. For example, we can double-click the Traceroute button and configure a measurement for IPv4 and another one for IPv6.
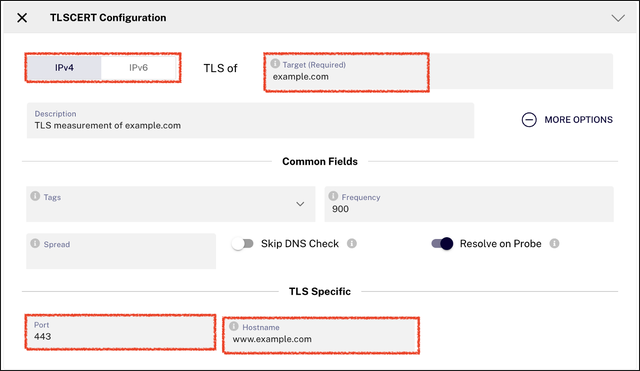
TLS
This feature allows us to analyse certificates from malicious sites to determine their status, activity, and geographic location. It also identifies related domains and extracts the certificate’s fingerprint for further analysis.
Interpretation of the data
Once RIPE Atlas measurements have been performed, it’s essential to interpret the results accurately to identify patterns of behaviour. As we carry out that interpretation, here are some of the things we focus on:
- Detecting whether the domain is still active or has been deactivated
- Verifying whether it is accessible from all regions or applies geo-blocking
- Analysing the network infrastructure used by the attackers
- Examining the digital certificates to identify potential patterns or links to other malicious campaigns
Analysis of a real-world phishing attack
To illustrate how periodic RIPE Atlas measurements can be used in a real world scenario, let's turn to a phishing case targeting users in Uruguay.
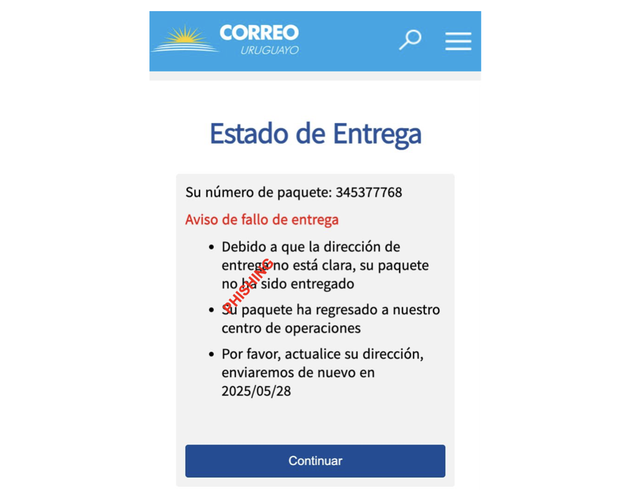
This phishing scam impersonates the Uruguayan national post office with the aim of stealing personal data and credit card numbers.
Once the necessary information about the attack is collected, several reports are prepared and submitted to the proper entities for the removal of the malicious site, including CERTs and Whois abuse contacts.
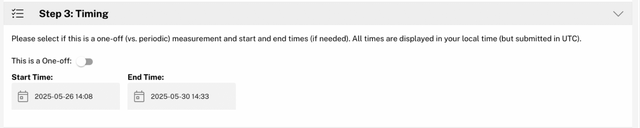
A DNS measurement is performed with RIPE Atlas every ten minutes for four days to analyse the validity of the domains, including their IP assignments and any potential changes. Two measurements are performed: one for A records (IPv4), another for AAAA records (IPv6).
The results are displayed in the maps below:
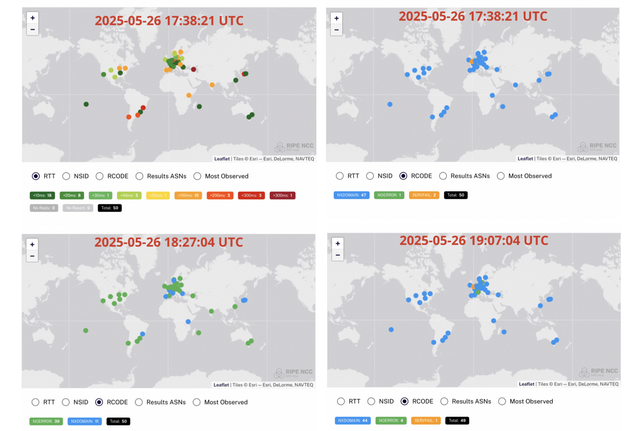
Breaking this down in more detail:
- At approximately 5:38 PM UTC, the phishing incident was reported to the entities it involved. The selected probes showed DNS response times below 300 ms.
- One hour after the report was submitted, 11 probes had stopped resolving the domain’s IP address. Some began returning blackhole IP addresses, suggesting that DNS protection was being used and had blocked access to the phishing site.
- After 90 minutes of measurements, half of the probes had stopped resolving the domain. Shortly after, all probes stopped resolving it, marking the end of malicious activity on that domain.
- Measurements stopped when the absence of an IP response was confirmed. However, they might be extended to monitor a potential reactivation of the domain under a new IP address.
It’s important to note that no IPv6 addresses were resolved by the probe during the period of activity.
Other use cases
There are a variety of potential cases where the use of RIPE Atlas in this type of research can provide useful results thanks to the wide geographical distribution of probes.
Analysis of malicious domains and IP addresses
RIPE Atlas allows us to observe how domains used in phishing or malware distribution campaigns are resolved and responded to from various regions around the world. This is useful for identifying geographically targeted attacks or documenting targeted detection evasion.
Detecting geoblocking
By running measurements from probes located in different countries, it’s possible to detect whether a malicious website is applying regional restrictions, making its content visible only to users in certain locations.
Tracking infrastructure changes
Scheduled measurements (such as DNS queries or Traceroutes) help monitor changes to the attackers’ infrastructure, including changes to IP addresses, network routes, or DNS servers.
Collecting information to support incident reports
Data obtained via RIPE Atlas supplements technical security reports, facilitating analyses by CSIRTs, CERTs, hosting providers, or domain registrars.
Supplementing other tools
Using the API feature, RIPE Atlas can be integrated with other platforms to correlate TLS certificates, domains and IP addresses data with other open sources tools and enrich the analysis.
Monitoring potential threat domains
RIPE Atlas allows measuring domains that could be used to launch attacks against our organisations. This includes IDN homograph attacks, where domains visually similar to ours are used to deceive users and conduct spoofing campaigns.
Limitations
It’s important to keep in mind that most website activity occurs in the upper layers of the TCP/IP model, particularly in the application layer. Although RIPE Atlas probes allow measurements that reach certain protocols in this layer (e.g., DNS and TLS), their focus is primarily connectivity and resolution testing, not interacting with the website content itself.
This represents a major limitation: it’s not possible to analyse the entirety of a website’s behaviour directly at the application level, so aspects such as forms, redirects, geolocation-based access restrictions, or authentication mechanisms cannot be assessed. So, if a phishing site implements restrictions or dynamic behaviors in its web development, these cannot be evaluated using RIPE Atlas alone.
Conclusions and call to action
RIPE Atlas offers a powerful, geographically distributed tool for the technical analysis of malicious websites. It allows the detection of targeted campaigns, infrastructure changes, and evasive behavior. Although it does not replace other tools that focus on the application layer, it is a valuable complement that enhances incident reporting by incorporating distributed and objective evidence.
Researchers, threat analysts, and CSIRTs are encouraged to include RIPE Atlas in their analysis and incident reporting workflows. Its potential to provide technical evidence from multiple locations makes it a valuable tool against increasingly sophisticated malware and phishing campaigns. We also encourage automating measurements and combining results with other sources, such as certificate analysis engines or domain reputation systems, for a more comprehensive and effective monitoring.
This article was originally published over on the LACNIC Blog


Comments 0