SPAM and abuse remain persistent challenges across various digital platforms, threatening user trust and operational integrity. Jolita Puzakova and colleagues explore how they tackle this persistent threat with a three-fold approach.
This article explores a comprehensive strategy implemented by IPXO, an Internet Protocol (IP) lease and monetisation platform to combat SPAM, abuse, and malicious activities. While the experience is drawn from the IP leasing industry, the insights offer valuable lessons for organisations across different sectors facing similar issues.
The Challenge
As digital platforms grow, they often experience a surge in abuse reports, primarily related to SPAM originating from their resources. This trend can threaten the integrity of any platform and the reputation of its users – a scenario familiar to many online businesses.
A Data-Driven Approach
Addressing this complex problem requires a methodical and data-driven approach. It involves thorough analyses of abuse patterns, evaluation of existing measures' effectiveness, and iterative development and implementation of new solutions.
Three-Phase Anti-SPAM Strategy
The anti-SPAM strategy unfolded in three key phases, each employing sophisticated techniques to address specific aspects of the SPAM problem.
1. Enhanced Monitoring and Policy Changes
Implementation of automatic scanning and enhanced monitoring to detect suspicious activities, with a particular focus on Pointer Record (PTR) and Reverse Domain Name System (rDNS) usage. This initial step, adaptable to various business models, provides valuable insights into potential abuse patterns.
By introducing automatic PTR scanning and improving monitoring to detect frequent PTR modifications, it becomes possible to quickly identify and respond to potential SPAM sources. This approach reduces the window of opportunity for abusers and improves overall network integrity.
2. Strengthened Know Your Customer (KYC) Procedures
Enhanced KYC processes have proven particularly effective and are widely applicable across industries. A comprehensive approach includes:
- Rigorous validation of user information
- Thorough background checks, including lookups in international sanction lists
- Implementation of stringent procedures for high-risk cases
- Review of user policies and practices
Strengthened KYC procedures can significantly reduce the number of malicious actors accessing a platform. This approach can be adapted by organisations in finance, e-commerce, social media, and other sectors to maintain a secure and trustworthy environment.
3. Advanced Technical Implementations
To address more technical forms of abuse, specialised infrastructure and control mechanisms can be deployed. For example, implementing Resource Public Key Infrastructure (RPKI) and Border Gateway Protocol (BGP) parking in the context of IP resource management.
Such implementations can combat issues like route hijacking more effectively. In the case study, this approach significantly reduced the average handling time for abuse cases from 3-4 days to just 1 day for RPKI-controlled IPs, demonstrating the power of proactive technical measures in abuse prevention.
Results and Lessons Learned
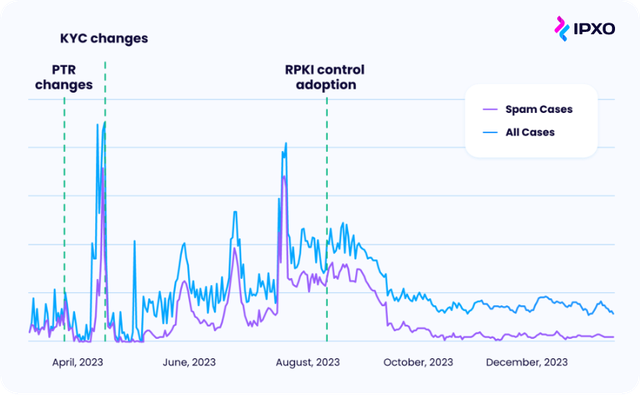
The implementation of these solutions yielded substantial results for an IP leasing and monetisation platform IPXO:
- Reduction in SPAM cases from 70-100% of all abuse cases to just 5-10%
- Decrease in resources listed on industry blocklists
- Significant improvement in abuse case handling time
This success demonstrates the effectiveness of a comprehensive, data-driven approach to security. As organisations across industries face similar challenges in maintaining the integrity of their platforms and protecting their users, several valuable lessons emerge:
- Implement robust monitoring systems to detect suspicious activities early
- Strengthen KYC procedures to prevent malicious actors from accessing your platform
- Deploy technical safeguards tailored to your industry's specific challenges
- Continuously analyse data and iterate on your solutions
Balancing Flexibility and Security
An important consideration highlighted during industry discussions is the potential correlation between shorter resource allocation terms (e.g., short-term leases in IP management) and increased abuse risks. Addressing this challenge requires a balance between flexibility for legitimate users and platform integrity.
Possible approaches include:
- Implementing robust verification procedures
- Offering options for setting minimum allocation durations
- Providing flexible terms while maintaining responsible resource usage
By sharing experiences and strategies, we believe the tech community can contribute to the broader conversation on digital security and resource management, offering insights that can help organisations across various sectors create safer, more trustworthy online environments.


Comments 0
The comments section is closed for articles published more than a year ago. If you'd like to inform us of any issues, please contact us.