The Center for Internet Security (CIS) recently published an updated version of the CIS Controls. CIS Controls v8 helps organisations break the zero trust journey down into achievable steps that are prioritised in a meaningful way.
Zero trust improves the security of IT environments as demonstrated over time by reduced attacker dwell time. The challenge many people face is understanding where to begin.
If you look at a particular vendor’s zero trust-aligned products, you may think of zero trust as being specific to their product set, whether it be identity and access management, microservices, or some other technology-specific solution. Zero trust has evolved, however, and the best description of it today, in my opinion, is the NIST Special Publication 800-207 on Zero Trust Architecture:
An operative definition of zero trust and zero trust architecture is as follows:
Zero trust (ZT) provides a collection of concepts and ideas designed to minimise uncertainty in enforcing accurate, least privilege per-request access decisions in information systems and services in the face of a network viewed as compromised. Zero trust architecture (ZTA) is an enterprise’s cybersecurity plan that utilises zero trust concepts and encompasses component relationships, workflow planning, and access policies. Therefore, a zero trust enterprise is the network infrastructure (physical and virtual) and operational policies that are in place for an enterprise as a product of a zero trust architecture plan.
Zero trust architectures are not only comprehensive, but also granular. We’ve moved from the zero trust definitions of a decade ago that provide isolation between applications with networking controls, to a model where isolation is at a component level within an application. Additionally, all of the tenets of zero trust apply at that granular level.
Zero Trust: Moving Security in the Right Direction
The pervasiveness of zero trust may seem overwhelming, on two points. First, if I can’t manage what I have today, how do I support zero trust? And second, how do I begin a zero trust journey?
The good news is that zero trust gives us a pivot point. We are transitioning to a new architectural model that positions security controls and management at the endpoint. Due to the use of pervasive encryption, we have an opportunity to build in security with management patterns that scale. Vendors following zero trust will provide an assurance that their products and the modules in their products meet expectations and are automatically verifiable. While this is not available today, zero trust is moving security in this direction.
Easier Detection of Unexpected Behaviours
This type of transformation builds in security and provides an opportunity for organisations to select a scalable model that reduces resource needs. If security is built in by the vendor and verified automatically, we can also begin to shift to allow list approaches that enable easier detection of unexpected behaviours. In other words, you can prevent and detect attacks from allow list approaches. This is instead of relying on products that compare artefacts and behaviours to known bad lists or deny lists after the fact.
This transition is supported by the recent Cybersecurity Executive Order published in May 2021. It will take time, but it can happen. A focus on how to scale management should be a consideration for vendors and consumers in their product selection as we make this transition. While that’s great, it sounds far off. What can organisations do today?
Prioritise Initiatives with CIS Controls v8 on Your Zero Trust Journey
The Center for Internet Security (CIS) recently published an updated version of the CIS Controls (version 8). This new version refined previous recommendations. It adjusted prioritisations of some Controls and Safeguards based on expert consensus and validated by current threats to have the most impact in reducing risk.
Within each of the 18 Controls, there is a set of Safeguards. The Safeguards comprise the more fine-grained recommendations to address the associated threats for that Control. Each Safeguard is categorised into one of three Implementation Groups (IGs), providing the prioritised recommendations that span the 18 CIS Controls. Controls v8 supports a zero trust architecture, while also aligning to the recommendations for built-in security, pervasive encryption, allow-list functionality, and supply chain security risk reduction called out specifically in the Cybersecurity Executive Order published in May 2021.
A Great Starting Point for Your Zero Trust Journey
If you are looking for a starting point on your zero trust journey, consider using the CIS Controls v8 to prioritise your journey and have the greatest impact on risk reduction based on current threats. By breaking the journey down into achievable steps, an organisation can make progress in the journey while being assured that the steps taken are prioritised in a meaningful way.
The CIS Community Defense Model process to validate the Controls and Safeguards prioritisation found that IG1 addresses the top five attacks from the Verizon Data Breach Report. The prioritisation is based on a complex assessment of threats from numerous breach reports. This includes Multi-State Information Sharing and Analysis Center (MS-ISAC) data.
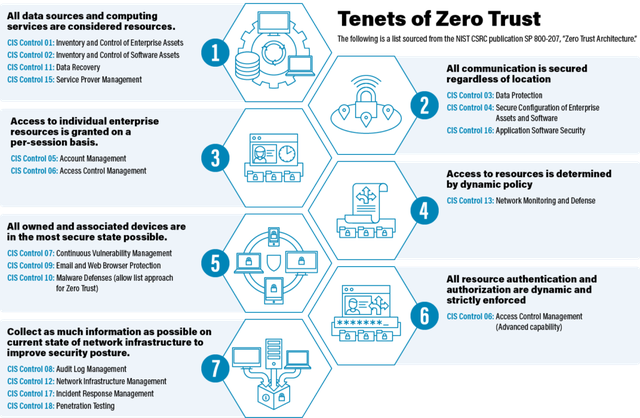
CIS Controls v8 Mapping to NIST SP 800-207 Zero Trust Tenets
The chart included below describes the mapping of CIS Controls v8 as they align to the NIST SP 800-207 Zero Trust Tenets.





Comments 0
The comments section is closed for articles published more than a year ago. If you'd like to inform us of any issues, please contact us.