Since the exhaustion of the IPv4 address pool, companies across the globe heavily rely on IPv4 transfer and lease markets. Unfortunately, transferred IP address blocks are far more likely to be blocklisted due to IP address abuse. But while abuse negatively affects IP address reputation, the risks can be minimised with the right level of awareness.
The Internet Protocol version 4 (IPv4) addresses have been a scarce resource for over a decade now. With the internet rapidly expanding and the demand for IPv4 increasing, the IPv4 transfer market has opened the door for organisations ready to scale.
Unfortunately, the IP transfer market faces a daunting problem – IP address abuse. In fact, as you will discover by reading this article, a considerable number of transferred IPs eventually get blocklisted, which further aggravates the global scarcity of an already deficient resource.
So, what are the most common types of IP address abuse and how should we approach it? Let’s have a look at the latest data.
The transfer market and what happens after a transfer
The transfer market emerged as a response to the IPv4 address space depletion, which began in 2011 on the IANA level, when the organisation announced the exhaustion of its pool of unused resources. For the RIPE NCC, November 25, 2019 marked the date when new IPv4s could no longer be allocated. Not long after, the RIPE NCC Community Projects Fund funded research focused on IP misuse and abuse within the IP transfer market.
A study led by Vasileios Giotsas demonstrated that the IPv4 transfer market size has significantly grown over the years. Between 2009-2019, the number of intra-RIR transfers (within a region) grew from just 17,408 to 40,463,872 IPs and the number of inter-RIR transfers (between regions) – from 1,792 to 1,885,440 IPs, with the highest activity recorded within RIPE NCC and ARIN regions.
Unfortunately, a significant percentage – nearly 40% – of transferred prefixes that are routed, eventually are blocklisted. In fact, the transferred IP space is between 4 to 25 times more likely to be blocklisted, depending on the type of IP abuse.
What is IP abuse exactly?
IP abuse is any malicious activity conducted by one connected device with an IP address against another device. Despite its type, the abuse can significantly affect IP address reputation, which measures the quality of an IP address. While IP addresses within the transfer market are mostly clean, the state can change drastically depending on the holder’s actions. If an IP address is flagged for suspicious activity, it can be blocklisted in no time.
RIRs have responded to the emergence of the IPv4 transfer market by establishing policy frameworks that aim to preserve registered IPv4 blocks and provide maintenance and transparency on how organisations trade them. Nonetheless, Giotsas’ research revealed that the effectiveness of these policies in preventing abuse of the IPv4 market are yet to be measured.
Spam, Malware, and DDoS - Top 3 threats to leased IPv4 resources
At the end of every quarter, we release IPXO Abuse Prevention statistics to provide a transparent view of the IPXO Marketplace and the health of the resources.
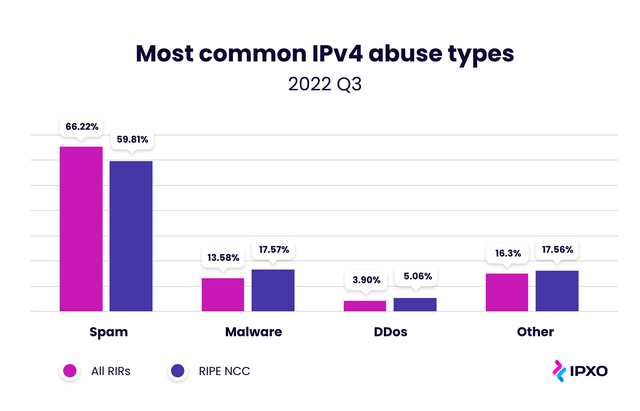
During Q3 – the period between July and September – we recorded 22,498 abuse incidents linked to IPv4 addresses leased via the IPXO Marketplace. The data shows that most of the IPv4 abuse cases were related to spam (66.22%), malware (13.58%) and DDoS (3.90%) attacks.
When comparing the overall abuse landscape with abuse specifically afflicting RIPE NCC-allocated resources, we can see that the trends remain predictable: spam (59.81%), malware (17.57%) and DDoS (5.06%) attacks were also associated with most abuse incidents (Figure 1). This clearly demonstrates that IP address abuse is not more or less prevalent in different regions.
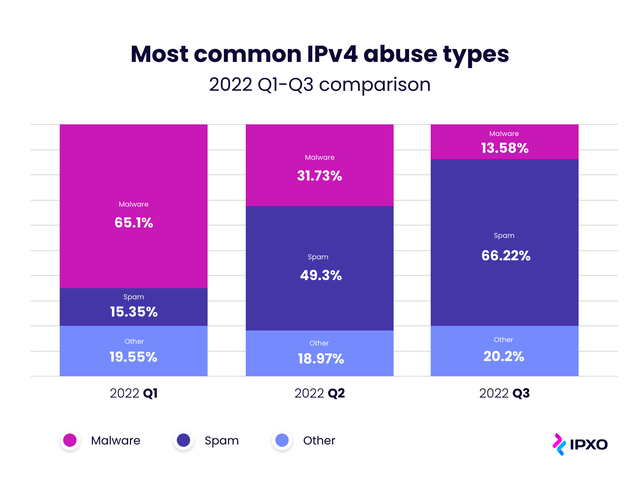
Overall, spam and malware have remained the top two threats to IPv4 addresses on the Marketplace throughout 2022 thus far (Figure 2).
Spam has also remained the #1 culprit behind IP address abuse incidents that required manual handling: 45% of all manually handled cases during Q1, 44.59% during Q2 and 42% during Q3. The share stays pretty much the same when we look at RIPE NCC allocated IPs as 46% of incidents handled manually were linked to spam (Figure 3). Fortunately, the need for manual handling remains low: 4% overall (all RIRs) and 4% for RIPE NCC-allocated IPs.
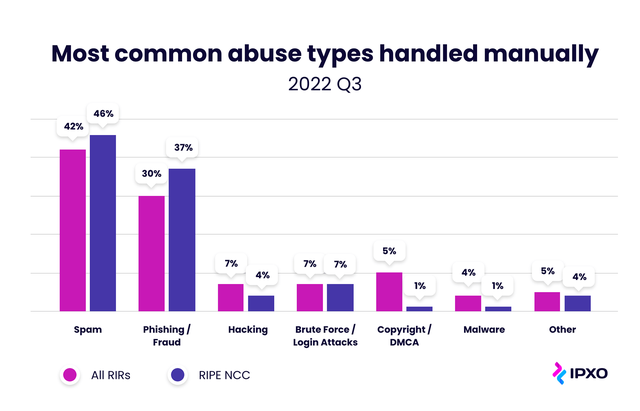
Fortunately, the need for manual handling at the IPXO Marketplace remains low: 4% overall (all RIRs) and 4% for RIPE NCC-allocated IPs. What is manual abuse handling at IPXO? It is the process of clearing all abuse cases that cannot be resolved automatically. These can include law enforcement subpoenas or complicated reports with irregular reporting templates.
Overall, it is possible to mitigate the most common types of threats linked to IP address abuse with in-line or out-of-band protection tools. This is vital because failure to take control of these threats can eventually lead to loss of IP address reputation, which can impact business operations in varying degrees.
When abuse occurs - tips to follow
Before a transfer occurs, it is crucial to check that IP ranges are not blocklisted. After the transfer, it is just as important to add a valid abuse contact for abuse handling. The RIPE NCC has provided a comprehensive guide on how to report IP address abuse using the Abuse Contact card.
Using the RIPE NCC’s Abuse Contact Finder, it is easy to locate the abuse contact and report the incident. Ultimately, while the RIPE NCC cannot control how IPs are used and abused, the RIR plays an important role in helping identify abusers. And if an abuse contact is missing, it is easy to fill out a Contact Form to request help (select ‘Report Incorrect Contact Information in the RIPE Database’). Note, however, that the RIR cannot control whether or not the abuser responds.
How to employ blocklists and IP address blocklist checks
Undeniably, when abuse takes place, time is of the essence, and the timeframe to report abuse must be kept to a minimum. That is because the longer one takes to register an attack, the higher the chances of IP addresses ending up in blocklists. The issue here is it takes time to clear IPs from blocklists, which can add additional pressure on businesses.
IP address reputation is maintained by organisations that manage blocklist databases. Although more than a 100 exist, Spamhaus, Proofpoint and Barracuda have produced some of the most widely used blocklists:
- Spamhaus is an Andorra-based non-profit organisation that uses sophisticated network of spam traps to help identify senders of unsolicited messages. If IP addresses or domains are blocklisted by Spamhaus, it is best to stop all emailing activity and immediately reassess email sending lists, content and sending practices.
- Proofpoint is a US-based security company that analyses messages to identify spam fingerprints and block IPs associated with them. The company also has several other data points and can identify many types of spam with accuracy. Proofpoint maintains the blocklist behind Apple's mailboxes like icloud.com and mac.com.
- Barracuda is another US-based security company that maintains blocklists and performs IP lookups to check for blocklisted IPs in real-time. The Barracuda blocklist is regarded as one of the most comprehensive of its kind, as it has a very low count of false positives in its blocklisted IP range.
Numerous free tools are available to check whether or not IPs exist in any of the blocklists. A few notable examples include the MXToolBox Blacklist Check, WhatIsMyIPAddress Blacklist Check or multirbl.valli.org Blacklist check tool.
While blocklists and IP address check tools can help uncover abused IPs, preventing abuse from occurring in the first place should be the gold standard. Hopefully, with an increasing level of awareness about IP address abuse and the assistance of internet registrars, like the RIPE NCC, we can mitigate the risk of IP abuse and, in ideal cases, prevent it altogether.





Comments 0
The comments section is closed for articles published more than a year ago. If you'd like to inform us of any issues, please contact us.