We experience an increased query load on K-root, the root server operated by the RIPE NCC. See below some analysis and graphs showing the traffic on K-root and other root servers.
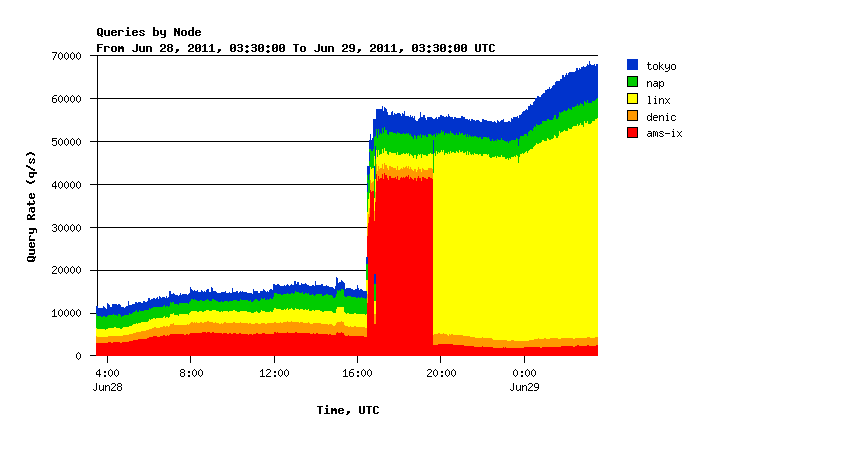
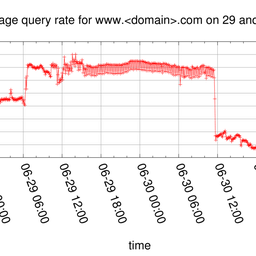
Since 28 June at approximately 17:00 (UTC), we observe an increased number of queries on K-root and other root servers. In Figure 1 below, you can see the number of queries per second seen at all K-root global nodes.
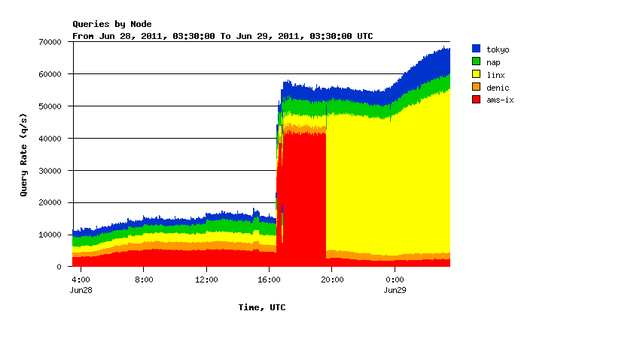
Figure 1: Number of queries per second seen at all K-root global nodes since yesterday
We see around 40,000 - 50,000 queries per second more than usual which is about four times the normal traffic load on the system.
You can see traffic shifting from AMS-IX (Amsterdam) to LINX (London) shortly before 20:00 hours UTC. We intiated this shift in order to gather data about the traffic source.
We are not yet sure what causes this increased query load, but we are in contact with ISPs that are carrying this traffic in order to investigate further. The root name server operators are coordinating observations and keeping a close eye on the developments. We update once we have more information.
Below you can see a series of DNSMON graphs that show how this incident affected the responsiveness of each of the root name servers.
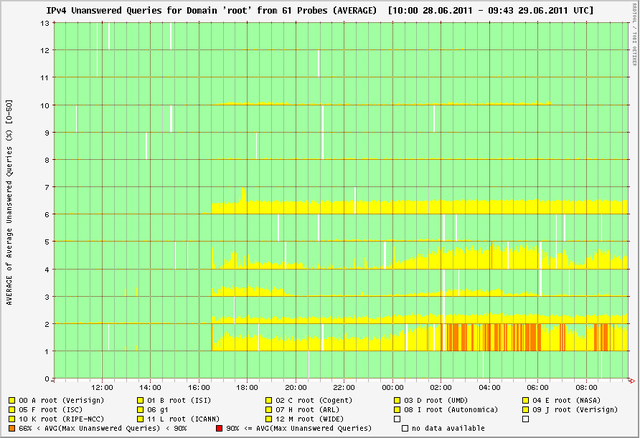
- Yellow = less than 66% of queries on average do not receive a response
- Orange = more than 66% and less than 90% of all queries do not receive a response
- Red = more than 90% of the queries do not receive a response
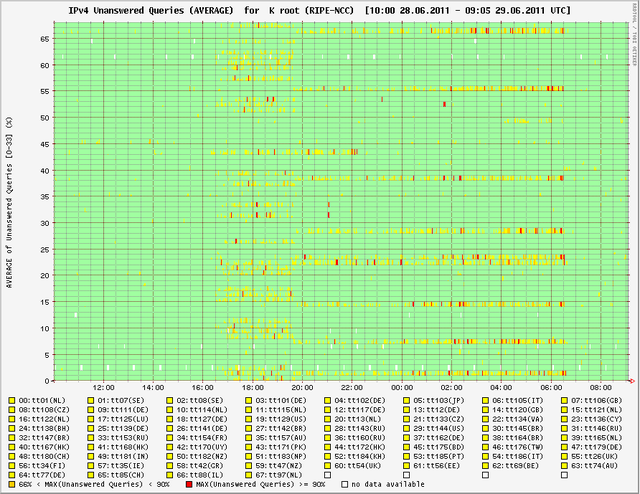
- Horizontal = only single measurement nodes saw a problem
- Vertical = most of the measurement nodes saw a problem
It is important to note that these measurements show that the root zone is fully available even though some root name servers show degraded performance. We expect no noticeable degradation of any Internet services caused by this.


Comments 9
The comments section is closed for articles published more than a year ago. If you'd like to inform us of any issues, please contact us.
Anonymous •
Did you manage to characterise the traffic? I have seen jumps in traffic caused by MX queries which generated large amounts of NXDOMAIN responses previously, though these were not as long lasting.
Anonymous •
So far they have been queries for QTYPE=A.
Anonymous •
Anything new / interesting to note?
Anonymous •
K-root is not having problems in coping with the additional amount of traffic. Our efforts are currently focused on back-tracing the possibly spoofed sources with upstream providers.
Anonymous •
If you're wondering why there are no statistics for the K-root instance in London, it's because we've paused the processing of the stats. We're still collecting them, but not post-processing them, in order to divert all capacity to answering queries. Eventually, all the staticstics will be visible.
Anonymous •
We saw this traffic drop to about half the volume it used to be at it's peak.
Anonymous •
Just a quick update: The number of the "unusual queries" has decreased. We are working to further mitigate the impact by distributing them more evenly among the anycast instances of K-root. We are busy analysing the characteristics of the "unusual queries". So far we do not have publishable conclusions and we do not expect to have them this week; we will of course publish our conclusions once our analysis is solid enough.
Anonymous •
We have seen similar (and larger) jumps in traffic in recent months and also observed the fact hat RD=1 on all the queries, we didn't find any pattern in source addresses though. Would be ver interested in anything you find.
Anonymous •
Hi Brett,<br /><br />We are currently starting our analysis of the events and digging deep into the traffic details. We will share our information as soon as we are finished with this analysis.<br /><br />Regards,<br />Wolfgang