GuardXP: From Data Privacy to Improved Cybersecurity


Pere Barlet
Based in Barcelona, Spain
I am a Full Professor with UPC BarcelonaTech and Scientific Director at the Barcelona Neural Networking Center (BNN). Between 2013-2018, I was co-founder and chairman at Talaia Networks, an AI-based cybersecurity startup. For this activity I received research valorization awards from both the Catalan Government and UPC, including the Fiber … More
• 6 min read
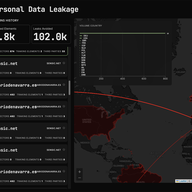
GuardXP is a collaborative project between UPC and CSUC supported by the RIPE NCC Community Projects Fund 2024. It aims to develop a privacy-enhancing tool to combat web tracking and data exploitation. Unlike traditional blacklist-based solutions, GuardXP uses code analysis to detect and block trac…