In order to use the RIPE NCC Resource Certification (RPKI) Service, the only option up to now was to rely on the hosted system in the LIR Portal. Today we are releasing a proof of concept of the Local Certification Service. This allows RIPE NCC members to run Resource Certification on their own systems.
On 1 January 2011, we launched the hosted RIPE NCC Resource Certification Service . This system allows our members to securely create a digital certificate listing their Internet number resources. Using it, they can create Route Origin Authorisation (ROA) objects, stating which Autonomous Systems are authorised to originate their prefixes, through a web interface in the LIR Portal .
The hosted platform caters to the majority of our membership. So far, over 570 LIRs have generated a resource certificate and most have specified their routing information. The result is that almost 180,000 IPv4 /24 equivalents are now covered by a ROA . For detailed information, please refer to our Certification Statistics page .
From the beginning, we have said that the hosted system was only a partial implementation, and that the service would be complemented by the possibility of running Resource Certification on your own systems. This makes the LIR the owner of the private key, allows them to host their own repository with certificates and ROAs, and opens up possibilities for scripting and more integration into their workflows.
Today we are releasing the Local Certification Service. There are two elements that make it work:
- The up/down provisioning protocol, enabling communication between parent and child certificate authorities
- The child certificate authority software, allowing the creation, provisioning, management and publication of your own resource certificate
The up/down protocol is a production implementation, and follows the IETF Internet Draft . This allows for third-party software, such as rpkid , to interoperate with the RIPE NCC parent system through the proposed standards.
To give you an idea of how a software package released by the RIPE NCC could work, we are offering a child certificate authority implementation as a proof of concept. For now, it will only allow you create a resource certificate and demonstrate the provisioning by the RIPE NCC parent system via a pilot server. Also, it will publish the certificate in the LIR's own repository and make it available over rsync. If there is strong community demand for developing this concept into a production software package, allowing the creation and management of ROAs, etc. then we will add that to our roadmap.
Now, let's have a look at how the system works...
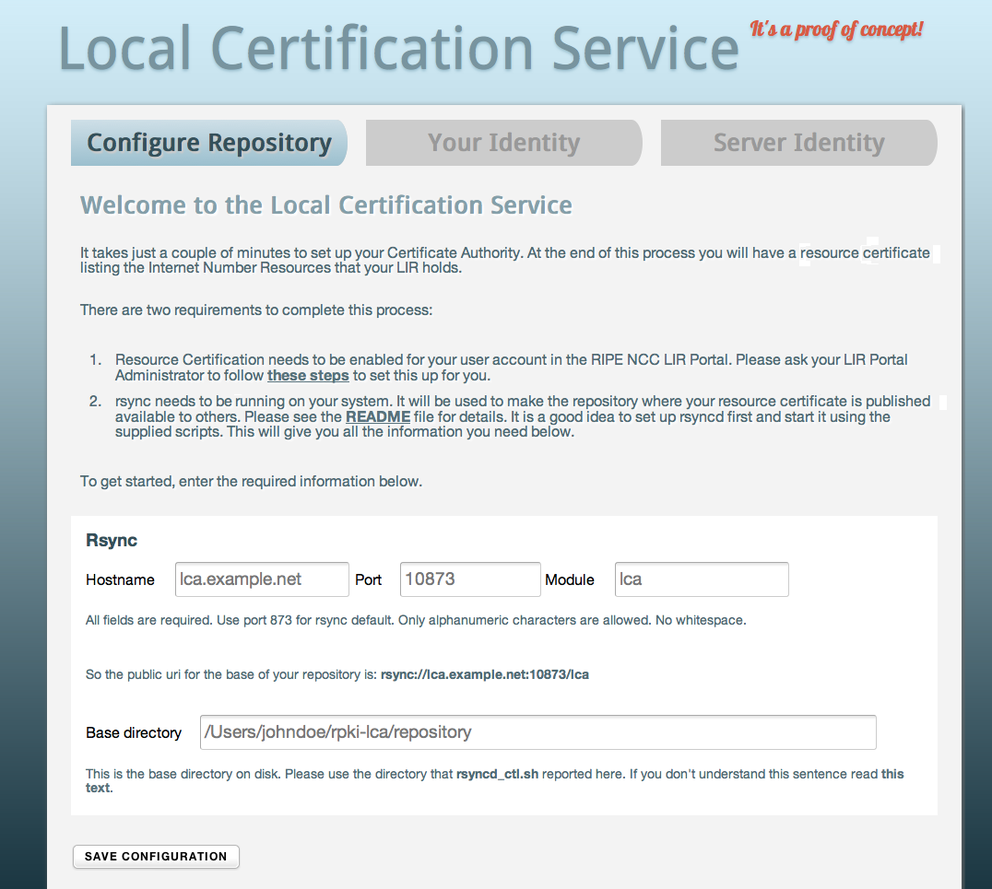
First, download the package containing the Local Certification Service software. The README file will outline all of the steps needed to get started. After configuring rsync, the database files and the web server, it's time to fire up the web-based interface, which looks like this:
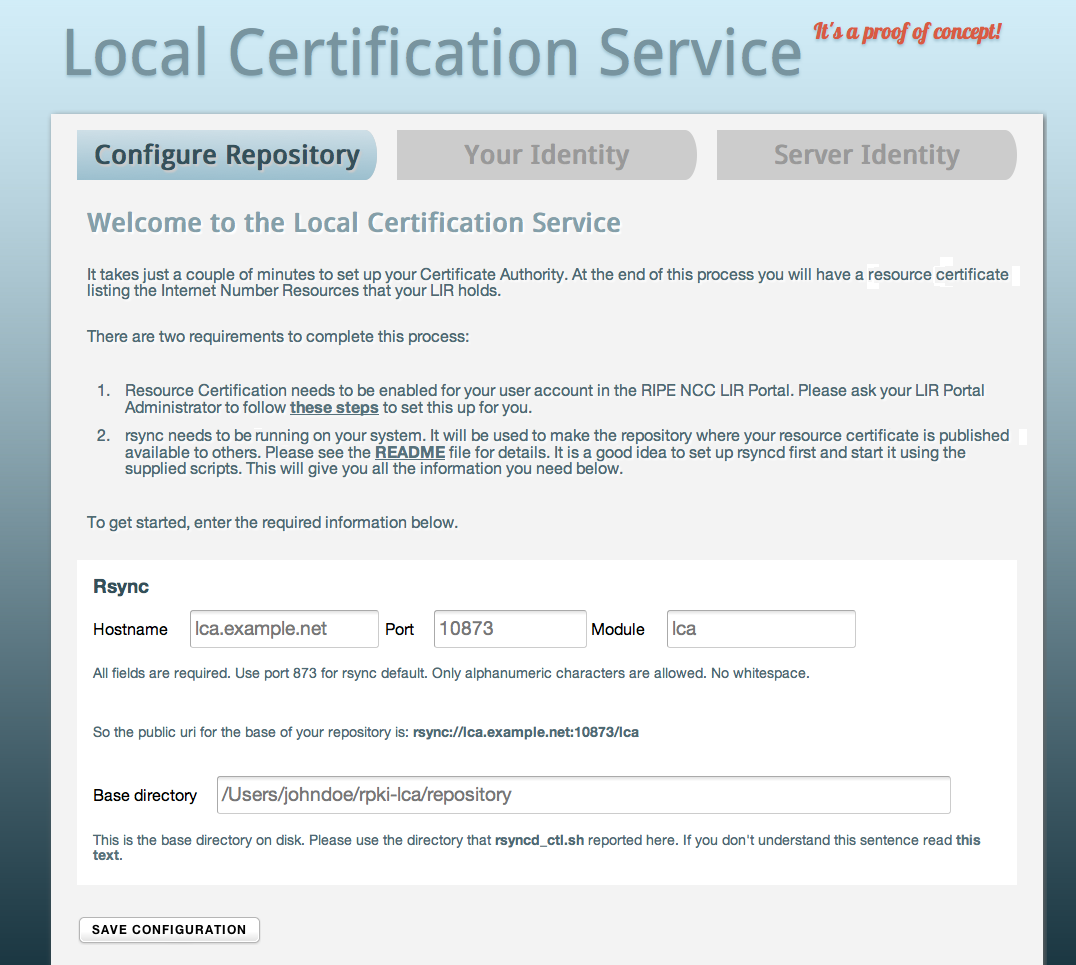 To set up your repository, you will need to enter the rsync hostname, port and module, as well as the base directory on your disk. Once you're done, save the configuration and continue to the second step:
To set up your repository, you will need to enter the rsync hostname, port and module, as well as the base directory on your disk. Once you're done, save the configuration and continue to the second step:
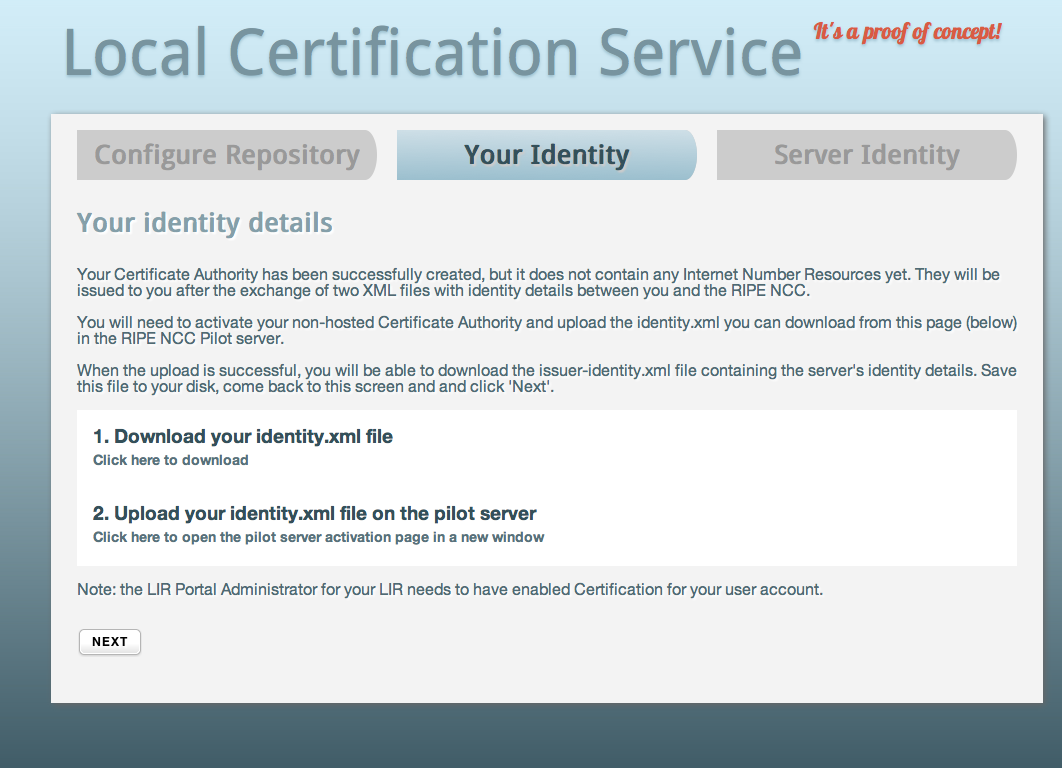 The software package will generate an identity certificate, which is used by the parent system to identify your LIR. You will need to download this file and open the LIR Portal Pilot Server in a new window:
The software package will generate an identity certificate, which is used by the parent system to identify your LIR. You will need to download this file and open the LIR Portal Pilot Server in a new window:
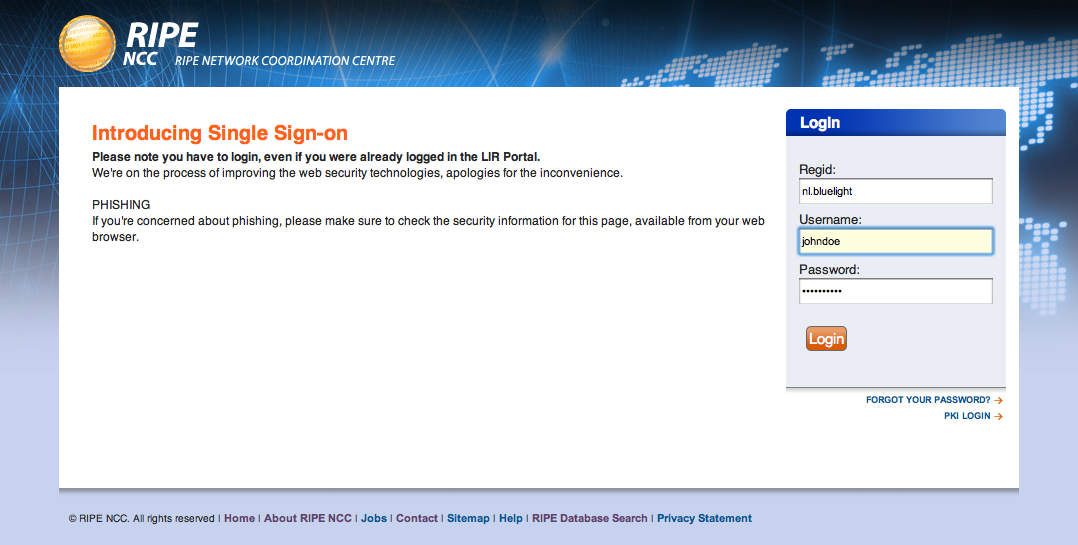
Please note that this is not the regular LIR Portal but a separate server set up for this proof of concept. However, the LIR Portal Administrator will need to have given you permissions for the "Certification" group in the regular LIR Portal for you to gain access. The credentials you enter here are linked to the identity certificate you will upload in the next step:
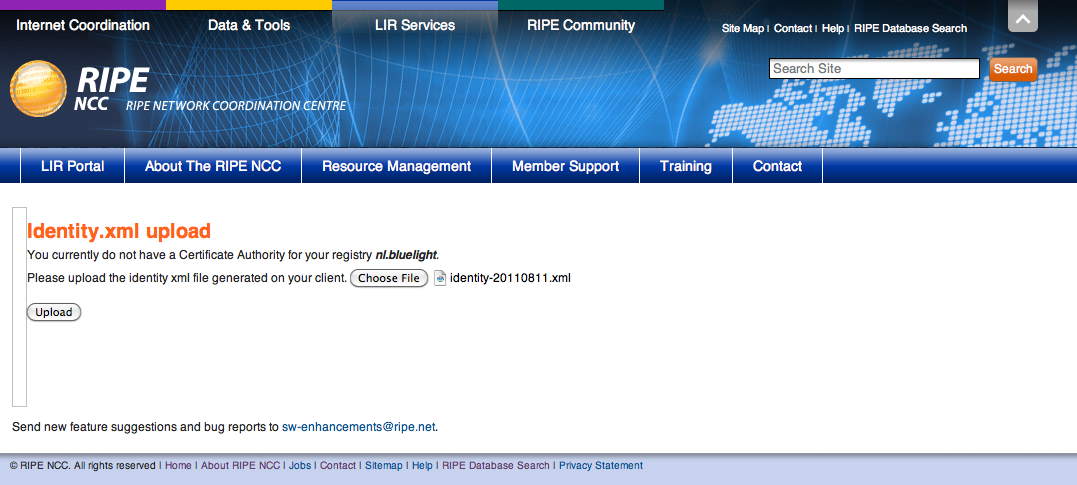 Click "Choose File" and browse to the XML file you just downloaded from the Local Certification Service interface. After clicking "Upload", the certificate will be verified:
Click "Choose File" and browse to the XML file you just downloaded from the Local Certification Service interface. After clicking "Upload", the certificate will be verified:
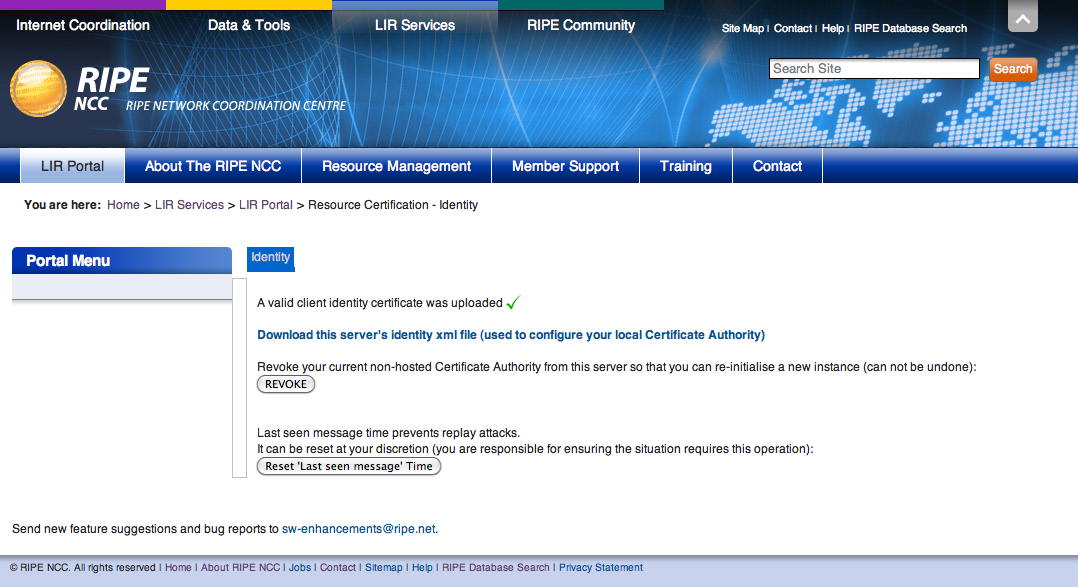 If verification is successful, the RIPE NCC parent system will generate an Issuer Identity Certificate, which you need to download and configure in the Local Certification Service system:
If verification is successful, the RIPE NCC parent system will generate an Issuer Identity Certificate, which you need to download and configure in the Local Certification Service system:
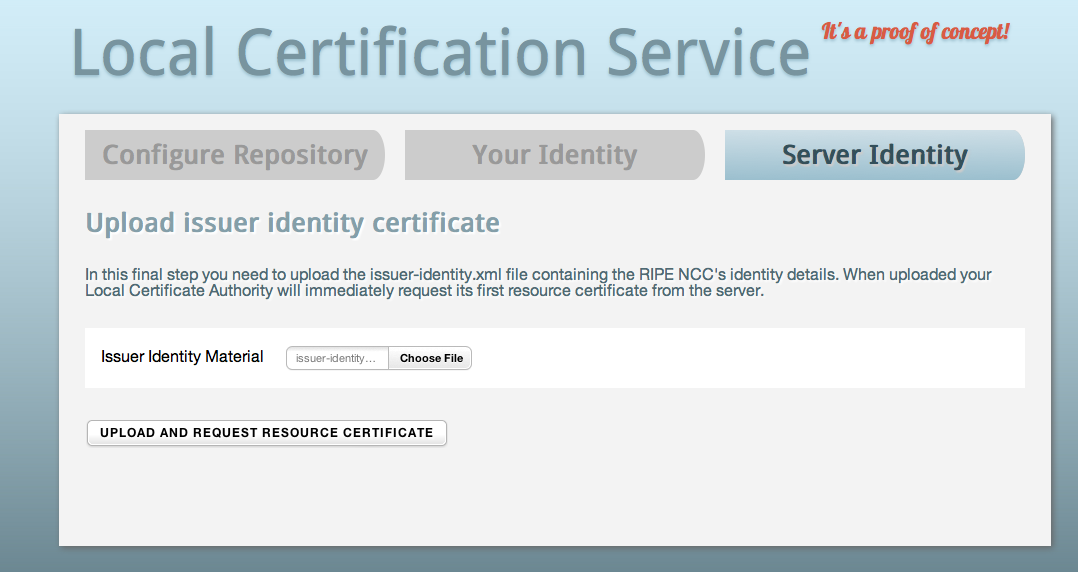 Click "Choose File" and browse to the Issuer Identity Certificate XML file, which also contains the provisioning URL. Through this channel, all updates to the resource certificate will be processed. After clicking "Upload and Request Resource Certificate", the process is complete and you will have a valid resource certificate, listing your Internet number resources, published in your own public repository:
Click "Choose File" and browse to the Issuer Identity Certificate XML file, which also contains the provisioning URL. Through this channel, all updates to the resource certificate will be processed. After clicking "Upload and Request Resource Certificate", the process is complete and you will have a valid resource certificate, listing your Internet number resources, published in your own public repository:
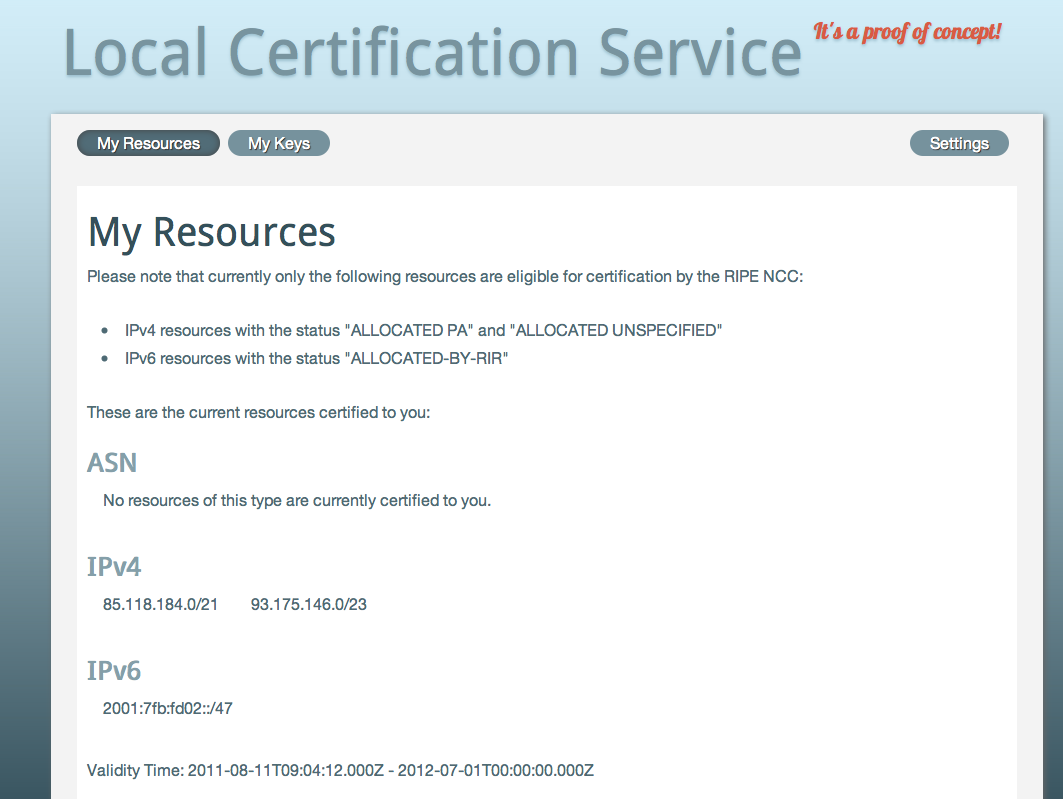 There are some other things this proof of concept will let you do. One is allowing you to update the resource certificate contents if you have received or returned resources. Other things are performing a key rollover and configuring the rsync publication interval.
There are some other things this proof of concept will let you do. One is allowing you to update the resource certificate contents if you have received or returned resources. Other things are performing a key rollover and configuring the rsync publication interval.
Of course, there is much more functionality we can implement. If the community would like us to develop this proof of concept into a production service, we can add features such as the ability to create ROAs, allow you to publish your certificate and ROAs in another repository than your own, build in an alerting system that compares your published ROAs to real world BGP routing and add scripting support as well as an API.
We look forward to your feedback.



Comments 2
The comments section is closed for articles published more than a year ago. If you'd like to inform us of any issues, please contact us.
Anonymous •
Hi Alex,<br /><br />The statement: "almost 180,000 IPv4 /24 equivalents are now covered by a ROA" sounds very impressive but what does it mean? It would be helpful if you could create trend lines for both the proportion of RIPE NCC IPv4 address space covered by a ROA and the proportion of prefixes allocated or assigned by the RIPE NCC covered by a ROA.<br /><br />That way we will be able to evaluate the benefit Relying Parties will be able to gain from the service.<br /><br />Thanks
Anonymous •
Hi Leo,<br /><br />We're not visualizing that data yet, but LACNIC has some interesting daily fresh numbers available here:<br /><a href="http://www.labs.lacnic.net/~rpki/rpki-evolution-report_EN.txt" rel="nofollow">http://www.labs.lacnic.net/[…]/rpki-evolution-report_EN.txt</a><br /><br />In short, almost 10% of RIPE region IPv4 address space is now covered by a ROA.