The Dutch Institute for Applied Scientific Research (TNO) and a number of Dutch security companies have recently published a report on IPv6 security test methodologies.
While experience on running an IPv6 network is growing, security testing methodologies for IPv6 are less known. Through a combined effort with Fox-IT, ITsec, Madison-Gurkha, Pine Digital Security and Riscure, TNO released a manual that can be used by security researchers to analyse IPv6 computer networks. This manual describes well known implementation problems and contains information that aids in the detection and remediation of these problems.
IPv6
The deployment of IPv6 has been increasing over the past couple of years. If an organisation chooses to use IPv6 as a method for communicating between systems, choices have to be made. For example about how these systems are provided with the correct communication settings and how filtering devices such as firewalls are configured. While these choices are comparable to the choices for IPv4, they require knowledge of the workings of the IPv6 protocol. This knowledge is not as prevalent as the knowledge of IPv4 which can subsequently lead to security weaknesses in IPv6 implementations.
Pentesting
One way to discover security issues is through a so-called ‘penetration test’ or pentest. Comparable to how a cyber criminal operates, it is attempted to break into or cause damage to a system or computer network. A manual that provides a step-by-step tutorial on how to analyse an IPv6 implementation was not yet available. The result of this research has changed that and allows for future security tests to be performed better and more efficiently. Ultimately this should reduce the damage of future cyber attacks.
Conclusions
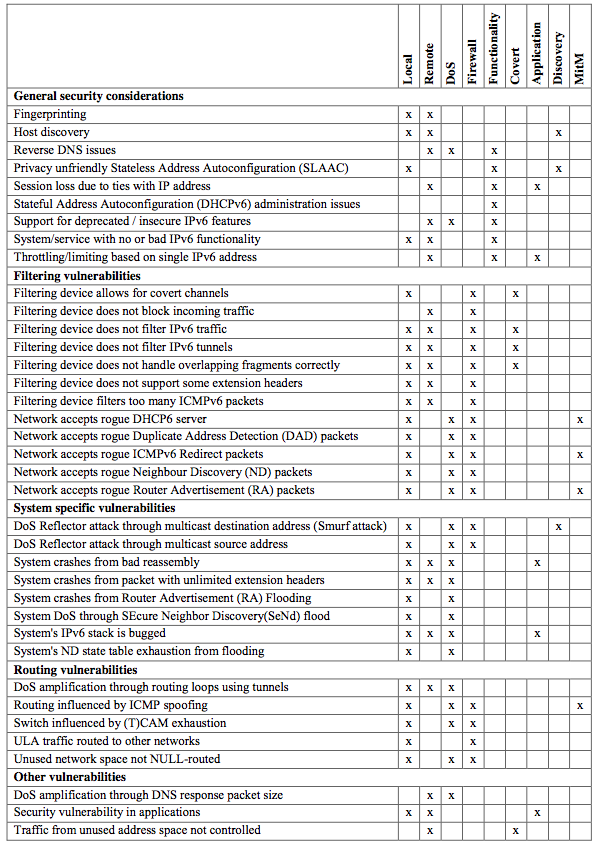
The vulnerabilities in this document can be linked to different categories; these have been identified (ordered by the number of vulnerabilities per category):
- Local - security issues that can be tested for in a local network
- Remote - security issues that can be tested for remotely
- DoS - security issues that can cause a denial of service
- Firewall - security issues related to firewalls or other filtering devices
- Functionality - security issues caused as a side effect of functional design decisions
- Covert - security issues that can result in a covert communication channel
- Application - security issues specifically related to applications
- Discovery - security issues related to the discovery of systems
- MitM - security issues that can be used for man-in-the-middle attacks
Below you can see the mapping between vulnerabilities and the aforementioned categories. This can help with selecting the issues to test for, given a specific scope for a penetration test (you can click on the image to enlarge it).
For more information, please refer to the TNO web site . The full report can be downloaded as pdf .


Comments 0
The comments section is closed for articles published more than a year ago. If you'd like to inform us of any issues, please contact us.