IP anycast has been widely used to replicate services in multiple locations as a way to deliver better performance and resilience. It has been largely employed by CDNs and DNS operators, such as on the root server system. However, there is little evaluation of anycast under stress.
With this in mind, we have released a new technical report which provides the first evaluation of several anycast services under stress with public data – including RIPE Atlas data. The report, which covers the Nov. 2015 DDoS events on the Root DNS , is entitled “ Anycast vs. DDoS: Evaluating the November 2015 Root DNS Event” , ISI-TR-2016-709, is also publicly available.
From the abstract:
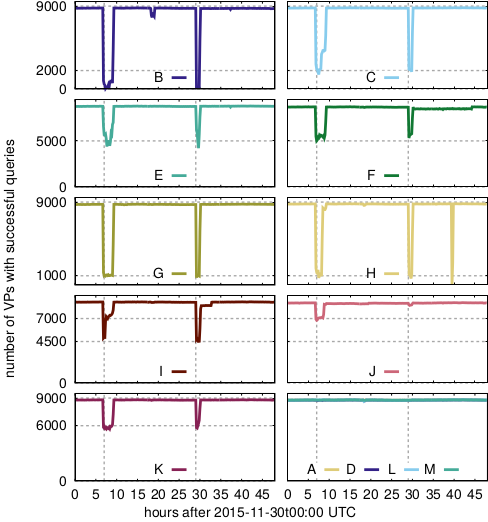
“ Distributed Denial-of-Service (DDoS) attacks continue to be a major threat in the Internet today. DDoS attacks overwhelm target services with requests or other traffic, causing requests from legitimate users to be shut out. A common defense against DDoS is to replicate the service in multiple physical locations or sites. If all sites announce a common IP address, BGP will associate users around the Internet with a nearby site, defining the catchment of that site. Anycast addresses DDoS both by increasing capacity to the aggregate of many sites, and allowing each catchment to contain attack traffic leaving other sites unaffected. IP anycast is widely used for commercial CDNs and essential infrastructure such as DNS, but there is little evaluation of anycast under stress. This paper provides the first evaluation of several anycast services under stress with public data . Our subject is the Internet’s Root Domain Name Service, made up of 13 independently designed services (“letters”, 11 with IP anycast) running at more than 500 sites. Many of these services were stressed by sustained traffic at 100× normal load on Nov. 30 and Dec. 1, 2015. We use public data for most of our analysis to examine how different services respond to the these events. We see how different anycast deployments respond to stress, and identify two policies: sites may absorb attack traffic, containing the damage but reducing service to some users, or they may withdraw routes to shift both good and bad traffic to other sites. We study how these deployments policies result in different levels of service to different users. We also show evidence of collateral damage on other services located near the attacks.”
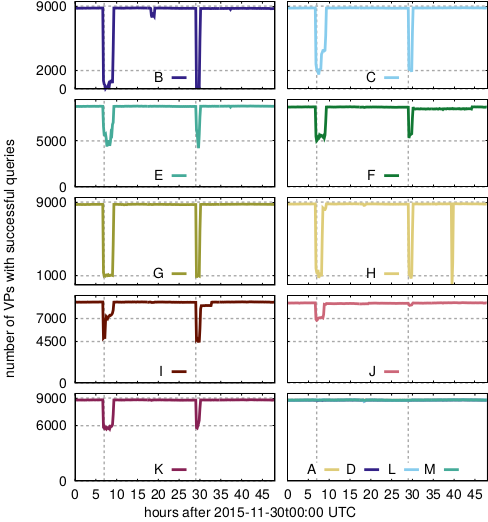
Figure 1: Reachability at several root letters (anycast instances) during two events with very heavy traffic .
This technical report is joint work of Giovane C. M. Moura, Moritz Müller, Cristian Hesselman ( SIDN Labs ), Ricardo de O. Schmidt, Wouter B. de Vries ( University of Twente ), John Heidemann, Lan Wei ( USC/ISI ). Datasets in this paper are derived from RIPE Atlas and are available at http://traces.simpleweb.org/ and at https://ant.isi.edu/datasets/ .



Comments 2
The comments section is closed for articles published more than a year ago. If you'd like to inform us of any issues, please contact us.
xxdesmus •
"IP anycast is widely used for commercial CDNs and essential infrastructure such as DNS, but there is little evaluation of anycast under stress." This simply is not true. I'd encourage you to research CloudFlare just a little bit...
Giovane Moura •
thanks for your comment. We refer to the fact that there's little publicly available evaluation -- and presented in a comprehensive way as ours.