New technical report evaluates DNS defenses in the wild against DDoS attacks and shows some interesting results.
The Internet Domain Name System (DNS) has been a frequent victim of DDoS attacks. Dyn, a large DNS provider, has been the target of a 1.6Tb/s DDoS fulled by the large IoT Mirai botnet. The root DNS servers have been victms of DDoS attacks several times - the November 2015 attack was estimated at 35Gb/s.
The DNS has been designed with several defense strategies to improve availability and resilience, both for authoritative server and recursive resolvers.
Authoritative DNS servers (the ones that host entire zones, like the root servers) heavily rely on replication, either name server replication and/or IP anycast. Nameserver replication means that multiple servers are used for the same zone, as in the case of the root zone, with 13 nameservers. Each of them, in turn, can be further replicated using IP anycast, which allows the same IP address to be announced from multiple physical locations, and allowing BGP to map a client to each location.
On the recursive resolvers side, caching (sometimes using multiple levels) of DNS answers and retrials of queries are the two main features used to provide resilience.
Given these different strategies, we did a study that examines how these strategies affect DNS resilience and latency in the wild, exploring both the client side's DNS user experience and server-side traffic. To do that, we carried out controlled experiments using RIPE Atlas and analyzed traffic from two production zones (.nl and the root zone).
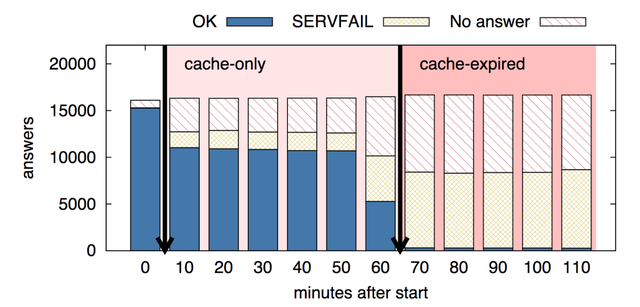
We present here four major findings of our study, which serve as recommendation for operators and developers:
- We find that in the wild, caching often behaves as expected, but about 30% of the time clients do not benefit from caching (Section 3). We confirmed that for the .nl and the root zones (Section 4).
- On the recursive resolver side, caching and retrials provide significant resilience for clients during DDoS attacks (Section 5). Even with very heavy query loss (90%) on all authoritatives, full caches protect half of the clients, and retries protect 30%.
- On the authoritative side, we show that there is a large increase in legitimate traffic during a DDoS attack (up to eight times in our experiments), due mostly to retrials. While DNS servers are typically heavily overprovisioned, this result suggests the need to review the level of overprovisioning (Section 6).
- In the final part of the report we discuss why users have seen relatively little impact from root servers DDoSes while customers from some DNS providers quickly felt attacks (Section 8).
The full report (PDF) can be downloaded from both SIDN and USC/ISI.



Comments 0
The comments section is closed for articles published more than a year ago. If you'd like to inform us of any issues, please contact us.