Network anomalies are not understood the same way among the network experts. However, establishing a unified view is important for the development of anomaly detection tools. The survey described below will help to develop such a unified view.
Many networks are monitored using a Network Behavior Anomaly Detection (NBAD) tool as an additional security mechanism. Such tools are commonly based on the detection of deviations from expected volume of measured network statistic (number of flows, packets, bytes etc.).
There is, however, a significant difference between signature-based and anomaly detection methods that requires a different approach.
In case of signature-based detection methods, usually a specific network event is detected (possible DoS/DDos attack, TCP SYN scan, etc.). Therefore it is possible to achieve better accuracy of detection that may allow implementation of automatic responses.
In case of anomalies, achieving such an accuracy and setting appropriate responses beforehand seems to be very difficult. The reason behind this lays in the difference in detection targets. We are targeting a broad range of network events – anomalies – that may or may not have been caused by harmful activity. Such a general detection can, by itself, produce only general alerts that require evaluation from a network administrator.
Therefore anomaly detection tools should report only the events that an experienced network expert would have considered to be an anomaly. In other words the tool should serve as an additional all-seeing eye that constantly watches network charts and suggests events that require proper evaluation – network anomalies.
However, the term network anomaly is not understood the same way among the network experts. There are many different points of view. For example, some may consider a periodic peak to be an anomaly while others may not because of its periodicity. The size of a peak and the time of day could also be important.
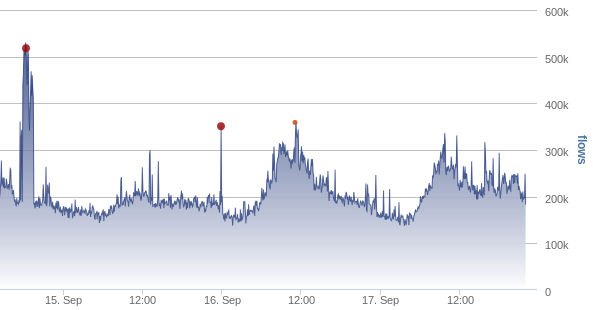
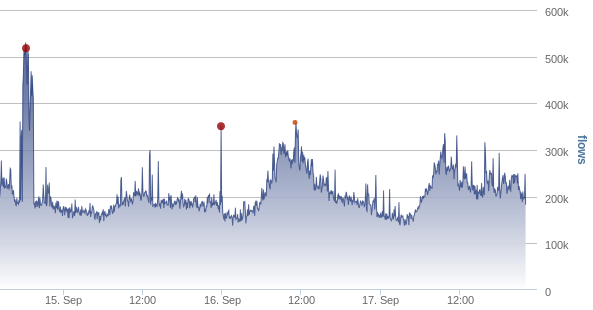
Figure 1: Example of an anomaly shown in a flow monitoring graph
There doesn't seem to be any relevant research that provides a unified view of the network experts on anomalies. Such view is, however, important for the development and evaluation of network anomaly detection tools.
That is why we created a short survey focused on network anomalies. The survey is intended to provide information about how the term "network anomaly" is understood by network experts.
The quality of respondents is very important for us. Therefore we would like use this RIPE Labs page to target the community of network experts and kindly ask you to fill out our survey. We will also publish the results on RIPE Labs in Q1 of 2014.
The survey is available at the following page until the end of this year:
https://security.ics.muni.cz/anomaly_survey/
We would like to thank all participants for their time and effort.
Comments 0
The comments section is closed for articles published more than a year ago. If you'd like to inform us of any issues, please contact us.