This artlce looks at the results of a recent survey that was conducted to find out which network security methods are currently in place and how operators are preparing for the introduction of Resource Public Key Infrastructure (RPKI). As part of the study, we also conducted interviews with a number of routing experts and network operators.
Introduction
With the planned launch of the resource certification system by the five Regional Internet Registries (RIRs) in January 2011, the practical deployment of the Resource Public Key Infrastructure (RPKI) can take off. The overall aim of resource certification is to secure the routing infrastructure and to validate that route advertisements are being made by the appropriate address block holders.
In the context of project commissioned by ENISA , the European Network and Information Security Agency that works for European Union Institutions and Member States, we carried out a survey of Internet Service Providers (ISPs) and network engineers. The goal of this survey was to find out more about awareness , deployment , and expectations of inter-domain routing security technology. Opinions on policy and governance in secure inter-domain routing were also inventoried. The results give us some insight into the drivers and barriers of secure routing technology, and can help with the successful realization of a more secure routing infrastructure.
So, what are these issues in routing security and how do they contribute to our insights. Assessing the awareness section of the survey, we can see that security risks in inter-domain routing are recognized and new technologies to improve routing security are welcome. But are organizations ready to invest time and money in routing security? Questions relating to deployment examine the plans to bring secure routing technology into service, and inventory the experience with currently deployed technologies (e.g., MD5, network ingress filtering (BCP 38), prefix/path filtering, monitoring, etc.). This gives some insight into the hurdles to routing security. Looking at the expectation s people have, we get some insight into the perspective of ISPs and network engineers on future secure inter-domain routing solutions, (RPKI, but also S-BGP, soBGP and others). Finally, questions regarding policy and governance issues completed the survey on drivers and barriers to secure routing.
We used two approaches to investigate the issues mentioned above. First an online questionnaire was carried out, and then a series of interviews with network operators/engineers/architects (see Figure 1). The quantitative data from the online questionnaire provided some numbers and statistics that complements the qualitative, insightful results from the interviews.
In the next section we present some general observations from the study, and add our own interpretations and conclusions. In-depth discussion and analysis of the results and recommendations for policymakers can be found in the full report on the ENISA website .
Online questionnaire
The online survey ran from February to March 2010. During this period, about 130 persons from the RIPE, AMSIX, DE-CIX, LINX, and Netnod communities responded to the call for participation and completed the online questionnaire. The questions ranged from high-level awareness to specific technology and deployment experience. The respondents are a 50/50 mix of strategic/architectural and technical/operational level.
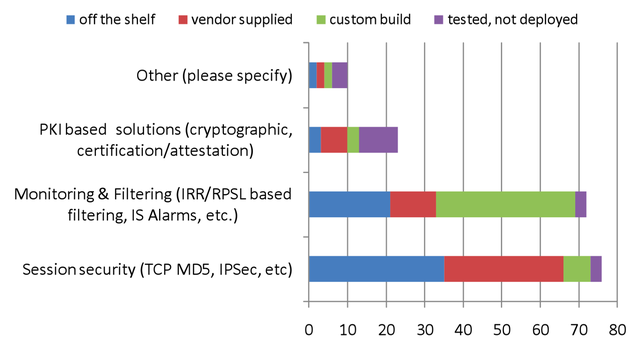
The most remarkable results from the online questionnaire are the perceived effectiveness of session security, the high appreciation of filtering, and the relative unfamiliarity with RPKI (see Figure 2):
- Session security like MD5, TCP TTL hack, etc., has the largest install base, but remarkably only 45% of the respondents see any improvement in security management, while another 45% do not. The remaining 10% indicates that it is even counter productive.
- Filtering, and to a lesser extent monitoring, has a smaller deployment base (about 10% smaller), but is considered much more effective (80% see improvements, 17% not, and 3% counter productive). Deployment of filtering is considered to be more complex than session security, though.
- About 40% of the respondents indicated that they know of RPKI as a technology to improve routing security. This is relatively low for an important technology that will be gradually introduced from January 2011. Respondents also feel that government involvement in routing security should be stimulation, not regulation.
Interviews
A series of interviews were conducted with 21 network engineers and routing experts. Their affiliations range from tier-1 to small ISPs, vendors, and researchers (profit & non-profit). In analysing and interpreting the results of the interviews, we should stress that although the range of subjects appears to represent a plural cross section of the networking community, it is a small and possibly biased sample.
In operating a network, stability is the pivotal operation metric for a network operations center (NOC). This is crucial to understanding why people do not care much about security as long as no problems occur. Generally, we can observe that large networks have experienced NOC staff with a high awareness of security risks. They tend to apply strict security policies for their networks and can therefore prevent security incidents and malicious attacks from propagating further over the Internet.
Most security incidents seen in inter-domain routing are caused by mistakes. It is difficult to get numbers of serious large-scale attacks for a number of reasons: (i) trust matters (in much the same way that banks rarely want to talk about credit fraud), (ii) it is difficult to distinguish between intentional attacks and non-malicious incidents, and (iii) smart and sophisticated attacks are difficult to notice.
The introduction of an RPKI infrastructure is expected to solve a number of these operational problems in prefix filtering. However, there are some concerns with the specific implementation of the infrastructure. Typically, a (R)PKI follows a hierarchy that does not necessarily reflect how the packets flow between the networks. Also, it is not clear yet if there will be a single authoritative trust anchor (as suggested by the NRO and the IAB) or if there will be a trust anchor for each of the 5 RIRs (as preferred by some ISPs).
Other concerns are the costs of the certificates and the period these certificates will be valid. Another concern mentioned by some of the interviewees is that the RPKI infrastructure can itself become a target for security attacks. As is often the case, a risk trade-off between increased complexity and increased routing security is needed.
Wrapping Up
The introduction of RPKI in tier-1 and large tier-2 networks will be a major transition, not only technically, but also in operational procedures. However, these large networks can leverage the deployment of RPKI in the inter-domain routing infrastructure. It is important to recognise that the Internet works because of smart operators, thus security solutions should include enough configuration methods to make them usable for operators. Another concern that was raised is the current shortage in skilled network staff that can implement and operate the new secure routing infrastructure.
See the ENISA website for the full report: Secure routing: State-of-the-art deployment and impact on network resilience
Acknowledgments
This article has been submitted by Benno Overeinder (NLnet Labs) and Maarten Botterman (GNKS Consult).
Thanks to everyone who participated in the survey and the interviews.





Comments 0
The comments section is closed for articles published more than a year ago. If you'd like to inform us of any issues, please contact us.