DNS has been in use on the Internet for more than 30 years — now it is time for its worldwide maintenance that shall, for the first time in the existence of DNS, require coordinated actions from all operators of DNS servers and DNSSEC validators. What actions do you need to take to survive?
This article summarises the crucial steps that operators of DNS servers should take to ensure that their users will not experience any difficulties following the scheduled DNS maintenance at the end of 2018 and early 2019.
The steps required to survive the DNS maintenance differ for DNSSEC-validating resolvers and authoritative servers:
- DNSSEC validators must be updated by 10 October 2018 at the latest
- Authoritative servers must be updated by 31 January 2019 at the latest
After these dates, software with outdated configuration will not work properly. The impact of individual changes is detailed in the relevant chapters below.
Recursive servers and DNSSEC validators
To be updated by: 10 October 2018
Operators of recursive servers and other software that performs DNSSEC validation must update the DNSSEC root key (trust anchor) used to validate signatures obtained from the public DNS. On 11 October 2018 at 4:00 PM UTC, for the first time in history, the DNS root zone will be signed with a new key.
For this reason, the software missing the new DNSSEC root key in the configuration will not be able to resolve any data using DNS starting on 11 October 2018, and from the point of view of a common user, “the Internet will not work”.
How should one prepare?
Operators of DNSSEC validators should make sure that their configuration contains both DNSSEC root keys so that the transition from the old to the new key can take place without human intervention. The key configuration file should contain the following two lines (or their equivalent, depending on the format used by the particular software):
. IN DS 19036 8 2 49AAC11D7B6F6446702E54A1607371607A1A41855200FD2CE1CDDE32F24E8FB5 . IN DS 20326 8 2 E06D44B80B8F1D39A95C0B0D7C65D08458E880409BBC683457104237C7F8EC8D
The first string contains the key with ID 19036 used until 10 October 2018, while the second string contains the new key with ID 20326 that will be used from 11 October 2018.
BIND software uses a key file format, which is different from the most of others, so BIND administrators should make sure that their key file contains the following text:
managed-keys {
. initial-key 257 3 8
"AwEAAagAIKlVZrpC6Ia7gEzahOR+9W29euxhJhVVLOyQbSEW0O8gcCjF
FVQUTf6v58fLjwBd0YI0EzrAcQqBGCzh/RStIoO8g0NfnfL2MTJRkxoX
bfDaUeVPQuYEhg37NZWAJQ9VnMVDxP/VHL496M/QZxkjf5/Efucp2gaD
X6RS6CXpoY68LsvPVjR0ZSwzz1apAzvN9dlzEheX7ICJBBtuA6G3LQpz
W5hOA2hzCTMjJPJ8LbqF6dsV6DoBQzgul0sGIcGOYl7OyQdXfZ57relS
Qageu+ipAdTTJ25AsRTAoub8ONGcLmqrAmRLKBP1dfwhYB4N7knNnulq
QxA+Uk1ihz0=";
. initial-key 257 3 8
"AwEAAaz/tAm8yTn4Mfeh5eyI96WSVexTBAvkMgJzkKTOiW1vkIbzxeF3
+/4RgWOq7HrxRixHlFlExOLAJr5emLvN7SWXgnLh4+B5xQlNVz8Og8kv
ArMtNROxVQuCaSnIDdD5LKyWbRd2n9WGe2R8PzgCmr3EgVLrjyBxWezF
0jLHwVN8efS3rCj/EWgvIWgb9tarpVUDK/b58Da+sqqls3eNbuv7pr+e
oZG+SrDK6nWeL3c6H5Apxz7LjVc1uTIdsIXxuOLYA4/ilBmSVIzuDWfd
RUfhHdY6+cn8HFRm+2hM8AnXGXws9555KrUB5qihylGa8subX2Nn6UwN
R1AkUTV74bU=";
};
File naming and location, as well as their exact format, depend on the specific version of the software and the operating system used. That is why we recommend reviewing guides for usual cases on ICANN pages.
Turris Omnia users with an updated operating system do not have to be afraid of the transition because the new key has been automatically installed on their devices.
Authoritative servers
To be updated by: 31 January 2019
Authoritative server operators should ensure that their name server implementation correctly responds to queries with EDNS extensions by 31 January 2019 at the latest. In accordance with the published plan, major DNS software vendors will discontinue support for servers that violate both the DNS standard RFC 6891 and its predecessor RFC 2671 after 1 February 2019 (also for the first time in history).
In practice this means that servers that do not respond to queries with EDNS extensions will stop functioning after 1 February for clients and domains hosted on these servers will become inaccessible!
How should one prepare?
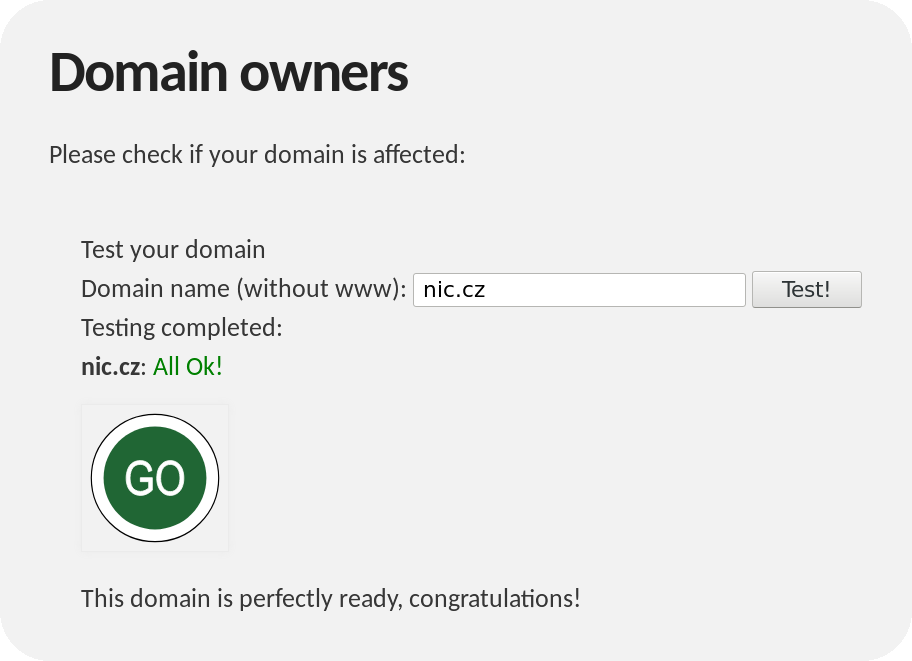
The first step is to make sure that your authoritative DNS server responds correctly. To do this, use the dedicated website dnsflagday.net with a testing tool. In the form, enter the name of any domain that is hosted on your DNS server:
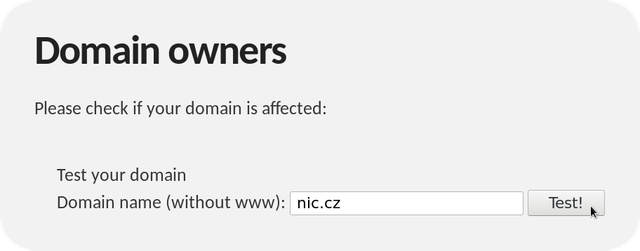
After clicking on the “Test!” button, the vast majority of those reading this article will see the following message:
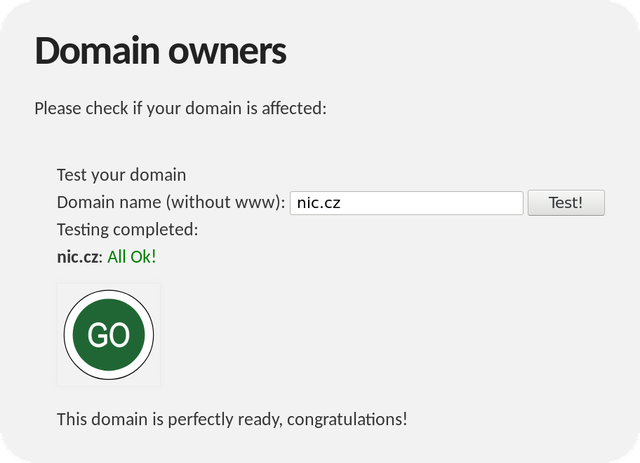
If you see this, no further action is required — your authoritative server is ready. If the testing tool finds a problem, it will let you know as follows:
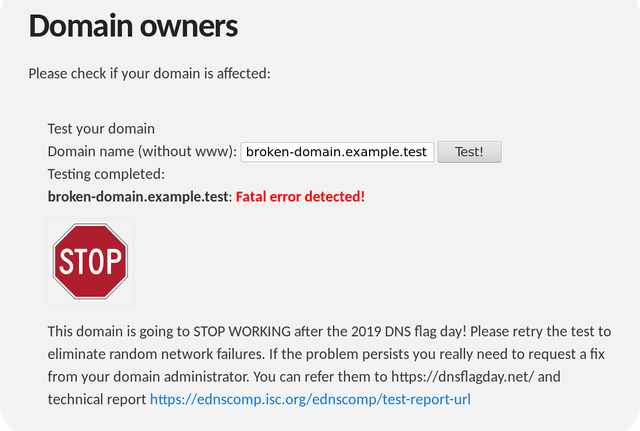
Usually, problems like this can be solved by simply updating DNS software on the name servers hosting the tested domain. In rare cases, the problem may be caused by a too strict firewall that discards DNS queries with EDNS extensions.
See dnsflagday.net for more information along with the test tool and troubleshooting recommendations.
In conclusion, I would like to wish all operators of DNSSEC validators and authoritative servers a smooth update of their software and seamless transition into the next 30-year DNS era.
This article was originally published on the CZ.NIC Blog.

Comments 0
The comments section is closed for articles published more than a year ago. If you'd like to inform us of any issues, please contact us.