Reporting from the hackathon is difficult: the spirit of the event lies in direct participation and shared experiences. In this article, we celebrate the achievements of the fifth RIPE NCC hackathon, document and promote results, and create a memento for participants.

Giant inflatable stroopwafel symbol of the prize in the non-competitive hackathon
The RIPE NCC's fifth hackathon happened in Amsterdam in April 2017. DNS operators, designers, researchers and developers took on the challenge and joined in to develop new tools and visualisations for DNS measurements.

- The event lasted two days
- There were 31 participants; 6 RIPE NCC staff; 3 jury members
- People were mostly using RIPE Atlas data
- We had 3 sponsoring organisations
- Stroopwafels were given as a prize
- The closing party was in the beer brewery
- We visited the local hackerspace
Differences from previous hackathons:
- We didn’t do it over the weekend
- Larger number of women participating (6 out of 40)
- More people than usual canceling last-moment
- It was in Amsterdam, but not in the RIPE NCC office
- Not in conjunction with a RIPE meeting
- however, presentations were delivered at RIPE74
- DNS-WG report slides & video
Results
The results were impressive! After two days of hard work, we had eight final projects, presented in five minutes each, and the discussion continued over the beers at the closing dinner. All software is available on Github, and all the presentations are published there too.
1. “Monitoring DNS Propagation Time”, by “Team USA and Friends” - Tom Arnfeld (Cloudflare), Shane Kerr (Dyn), Kai Storbeck (xs4all), Jon Mercereau (ex-LinkedIn)
This project was based on an idea that originally came from Shane - monitoring DNS server (SOA timestamp) propagation time to try to answer the question “How consistent is DNS?”. Short answer: it can get crazy out there! Method: looking at the moments when a change is made by one of the registrars, and following how quickly these changes propagate. Looking at the “first seen” timestamp for a specific SOA at various name servers, by using RIPE Atlas DSNMON of .com data. Python scripts, Elasticsearch and Kibana were used as tools. Several detailed findings regarding inconsistencies were visualised and shown in the slides. There were also some curious findings. Next step: an analysis based on the real-time streaming of data.
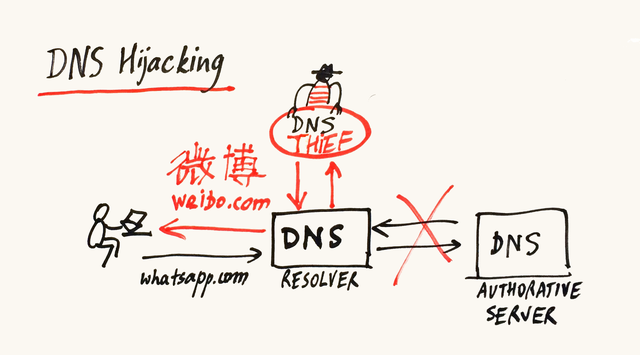
2. “I know what you did…” aka “DNS resolver hijack tester” aka “DNS Censorship” by Edward Zambrano (Spotify), Nick Wolf (consultant), Sergey Krasnopivets (Selectel), Konstantin Novakovsky (Selectel)
Trying to answer the questions: how do you protect from “bad actors” on the Internet? How do you know that DNS resolution is coming from the “proper” place? Method: active measurements - use RIPE Atlas probes to query a pre-set DNS record on your own server, and to use a public DNS resolver with known IP addresses; match the responses; mark the probes that show inconsistent responses. Result: out of 6,700 probes, 113 are “suspicious” or “being weird”, which might mean there is DNS hijacking going on, or something else - and that requires further analysis. They established cooperation with another team who did “DNS Fingerprinting”, and got some overlapping results - but in general, these two tools are complementary.
What I liked about this approach is that, although the goal is to measure censorship, the users involved in measurements are not put in danger, since there is no direct attempt to reach “forbidden” web sites - only the public resolver is used.
3. “DNS Fingerprinting” by “Polish Guys” - Pawel Formski (FarSight Security), Maciej Andzinski (NASK), Marta van der Haagen (design), Mateusz Kaczanowsk (Facebook)
This team tackled the same problem as the previous one - identify hijacked DNS resolvers - but with a different method: by building “fingerprints” of recursive DNS servers. Using RIPE Atlas measurements, observing characteristic features in replies, and machine learning algorithms to train a computer to be able to discern between a legitimate server and a hijacked one.
Results were presented as a map and a table with the number of probes per country that were judged as “hijacked”. Not surprisingly, the density of probe distribution corresponds with the absolute numbers of affected probes. In relative terms, top-5 countries were: VN, MG, IQ, ID and KR.
Interesting side result: this fingerprinting approach can also be used to detect a somehow opposite problem: an ISP pretending to be operating their own caching recursive DNS servers, but in reality redirecting their traffic to Google or OpenDNS resolvers.
4. "Reverse DNS statistics" by “RIR team” - Sofia (APNIC, ex-LACNIC), Anand & Max (RIPE NCC), Sara Bagheri (student)
The goal was to dig (pun intended) into the wealth of reverse DNS data, and find how consistent it is: percentage of delegations with issues (lame), latency in domain object creation, coverage of address space with reverse delegations. The data sources used included the whois database, RIPE NCC Delegated stats file and RIPE Stat. Although only 100 prefixes were used as a sample, the results were not encouraging: the quality of reverse DNS delegations is quite low, and the DNSSEC situation is “very sad”. There is a lot of room for improvement among LIRs!
5. “Everything you ever wanted to know about caching resolvers but were afraid to ask” by Team “DNSThought” - Andrea Barberio (Facebook), Petros Gigis (RIPE NCC/FORTH), Jerry Lundström (DNS-OARC), Teemu Rytilahti (HGI, Ruhr-University Bochum), Willem Tooroop (NLNetLabs)
The goal of this project was to provide insight into caching a resolver's availability and capabilities. By querying a custom-created server, and using multiple measurements from all RIPE Atlas probes, and finally analysing received results, the final output was possible to query on the live dashboard , that you can query per probe, per resolver, or show all on the map.
Additional results of the work of this team are: the existence of new RIPE Atlas measurements, that will be useful to other researchers and DNS operators in the future; and several new feature requests for improving RIPE Atlas. Personally, I liked their team name.
Good news that we received after the hackathon was that the work goes on, and the "Go bindings" code was contributed, as a continuation of this project.
6. “Passive DNS Collection (and Statistics) from RIPE Atlas Sensors” by Alexandre Dulaunoy (CIRLL.lu)
Alex was working like a one-man team, and he finished his project!
7. “Anomaly Detection on DNS Auths” by Team "Anomalizers" aka "Platypus" - Christian Doerr (TU Delft), Ella Titova (VivaCell), Giovane Moura (SIDN Labs), Jan Harm Kuipers (University of Twente/SIDN Labs), Moritz Mueller (SIDN Labs/University of Twente), Ricardo Schmidt (University of Twente), Wouter de Vries (University of Twente)
This team's objective was to implement existing anomaly detection algorithms to RIPE Atlas DNS measurements. They used DNS measurements with chaos.id support and traceroute measurements, and analysed path changes and reachability/latency. The results were presented in a live demo. Possible next steps are to: automate it to continuously probe it; detect and create notifications.
8. “RIPE Atlas Stream To Anywhere” by Team “World Peace” - Ulrich Wisser (IIS), Stefan Jakob (DENIC)
This small team’s goal was to use an existing monitoring tool (Telegraf) and “feed it” the RIPE Atlas “status updates” results. “Telegraf” is a plugin-driven server agent for collecting and reporting metrics. After writing the code in Go, the team has achieved their goal, imported data, and visualised results.
And the Stroopwafels go to…
The focus of this hackathon was on cooperation, not competition, so we did not want to have a winner-as-such. However, some projects were better in certain aspects than others, and we had a limited amount of stroopwafels to give away. After a short discussion, the jury decided to distribute stroopwafels in this way:
- The work by “Team Anomalyzer” has been awarded the LARGEST BOX of stroopwafels, for the combination of their scientific approach, their use of existing measurements, and good teamwork
- Two teams that worked very closely together, on the same topic of DNS censorship, but with two different approaches, received six packages of traditionally-tinned stroopwafels to share for collaboration
- For the most-completed project, Alex received the “hipster” package of stroopwafels
Big thanks to the excellent jury, that had a hard work twice: first to select participant from many applicants, and then again to make judgement-call between so many good final works: Jim Reid, Desiree Milosevic and Jaap Akkerhuis.

Collection of stroopwafels as prizes for various categories of best projects
Other awards included:
- T-shirts
- RIPE Atlas credits
- The opportunity to present the project at the RIPE 74 meeting
…and the most important reward will be the continuous support that the RIPE NCC wants to extend to the projects that are being maintained in the future. We can help by providing resources, administrative support, and opportunities to support follow-up work, if needed.
We are grateful to sponsors who made this hackathon possible: DENIC, Afilias and FarSight Security.
We are looking forward to the continuous cooperation with, and also between, the hackathon participants. See you at the next hackathon!
Table of results
| Team / project | Project | Code | Slides | Website / Demo |
| 1 | Monitoring DNS Propagation Times | Code | Slides | |
| 2 | DNS Resolver Hijack Tester | Code | Slides | |
| 3 | DNS Fingerprinting | Code | Documentation | Comments on HackerNews / Y Combinator |
| 4 | Reverse DNS Statistics | Code | Slides | |
| 5 | Everything you ever wanted to know about caching resolvers but were afraid to ask |
Code + Go bindings for RIPE Atlas API |
Slides | Demo |
| 6 | Passive DNS | Code |
Results Example |
|
| 7 | Anomaly Detection on DNS Auths | Code | Slides |
Demo Blog |
| 8 | Ripe Atlas Stream To Anywhere | Slides |
Other Activities
Before the hackathon, a smaller group visited a local hackerspace, in order to connect with the local community, as the tradition requires. Then after the event, an even smaller group visited the hot-tubs on the top of the hotel, to relax and get ready for the closing party.
For more documentation about local craft beer places, take a look at the collaboratively edited document.
Venue
The venue of the hackathon was VolksHotel, the history of which is symbolic of the history of the gentrification of Amsterdam: the building started like a publishing house for the Volkskrant newspaper, which it remained for 42 years; then, for 6 years it was a "creativity incubator" (a so-called "broedplaats"), which was a replacement for the Dutch practice of squatting the derelict buildings and the artists, students and designers taking over; and finally, 3 years ago it turned into a hipster hotel, just like almost every "free" building in Amsterdam.
New Potential Partner
While promoting our symbolic prize, we got in touch with the company Stroopwafel World, who might want to be a partner in our future events. Looking forward to the possible cooperation!





Comments 1
The comments section is closed for articles published more than a year ago. If you'd like to inform us of any issues, please contact us.
Vesna Manojlovic •
A follow-up article about the Reverse DNS statistics by RIR team: https://blog.apnic.net/2017/05/25/investigating-status-reverse-dns/