A brief look at the effects of BGP route origin validation on mis-announcements and hijackings.
Introduction
The Internet’s routing infrastructure is vulnerable to attacks and misconfigurations that can seriously affect the ability of hosts to communicate. One such attack on the global routing system is the injection of false information into BGP (Border Gateway Protocol), which can impair data confidentiality and integrity, and disrupt network operations.
This vulnerability can be substantially reduced through the use of a Resource Public Key Infrastructure (RPKI), a system designed by the Secure Interdomain Routing (SIDR) Working Group at the IETF. An RPKI can be used to certify Internet number resource allocations (IP addresses or Autonomous System (AS) numbers). This enables network operators to generate their routing policies from securely verifiable allocation data, providing much higher confidence in the authenticity of routing information.
Currently, RPKI supports origin validation, which enhances routing security by allowing network operators to check whether an AS is allowed to originate a given route. This can give some protection against bogus announcements and prefix hijacking. But that can still leave networks vulnerable to the attack described here, in which a hijacked route is originated with the valid origin prepended.
This brief study aims to estimate how successful such an attack could be.
The Attack
This attack works by prepending the valid origin onto a fraudulent route announcement. So if AS1 wants to hijack an AS2 prefix, they can announce it with AS2 as the spoofed origin, and transit through their own network:
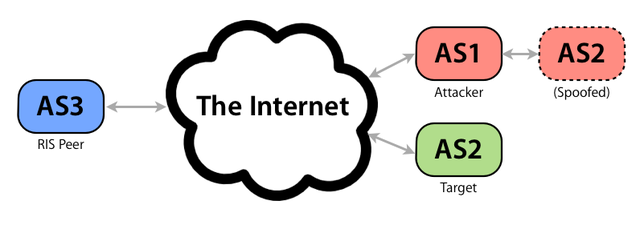
If a network is filtering based on valid origin, the bogus route could pass validation and still propagate. And if the route has a shorter AS path than the genuine route(s), it could likely be preferred in BGP.
Effectiveness
Using publicly available data from the RIPE NCC's Routing Information Service (RIS) , we can estimate how likely these attacks are to succeed. For each peer that provides a full table to the RIS, we estimate how many hijacked routes could be preferred over genuine routes. This was calculated for all combinations of this attack, in which each (visible) AS is simulated as both attacker and target (~34,300 2 combinations).
Of these attacks, 13.6% could have succeeded (13,149,591,970 out of 96,455,687,678). As a comparison, this figure drops from 34.2% when the hijacked AS path length is one shorter (i.e. when a valid origin is not prepended and ROAs are ignored). So this suggests a reduction of ~60% in success when AS paths are one longer.
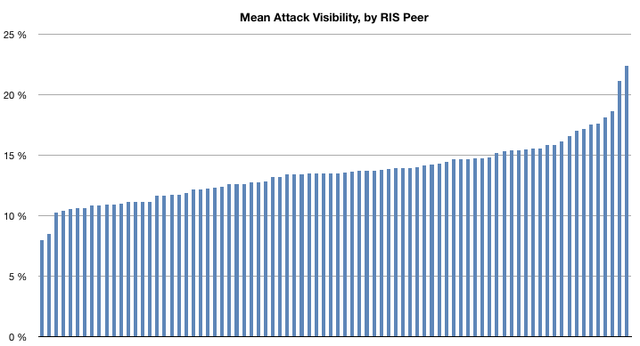
When looking at the variance between RIS peers, we can see that some networks see fewer hijackings than others. Although the RIS peers in the above chart are not identified, the two with the lowest rates (<10%) provide anycast DNS services, and the two with the highest rates use predominantly one upstream provider. So as a loose indicator, those with 'better' connected networks appear less likely to prefer these bogus announcements.
It is interesting to note how successful a given network could be at this type of attack, and the variance in this success between networks. The graph below aims to show this, with the success rate for each AS plotted as its own data point:
Mean Hijacking Success, per Visible AS
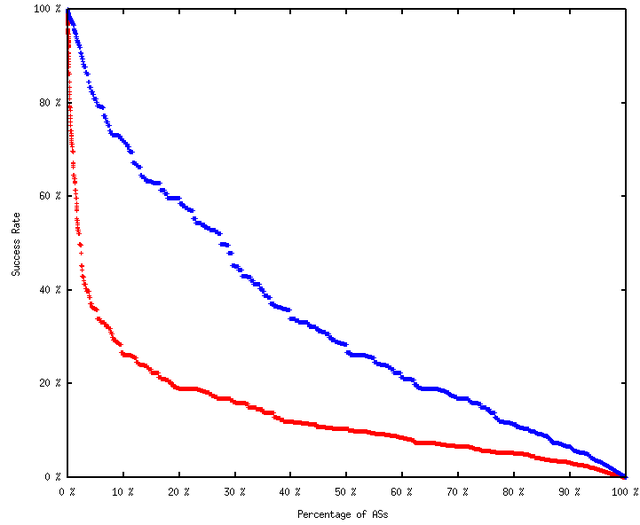
Red - With origin prepending
Blue - No origin prepending (for comparison)
There are a small number of networks (upper left corner) that could hijack a large number of other networks. But the majority show a much lower success rate (for the red plot) resulting in an average of 13.6% .
For comparison, the blue plot shows the equivalent distribution when prepending is not used. The drop in success when AS path length is increased by one is quite significant.
Note that the red plot models a world in which 100% of BGP speakers perform route origin validation. In reality, a partial RPKI uptake would give a distribution in-between the red and blue plots.
Limitations
Naturally, there are some limitations to the results obtained above:
- The calculations assume that routes with shorter AS paths win. This is not always the case, and there are always many factors in determining routing policy.
- Data is sampled from the RIS peers that supply a full BGP feed. Of course, these 82 peers are not a comprehensive view of the whole Internet.
- A more specific route announcement would likely be preferred regardless of AS path length, as seen with Pakistan Telecom and Youtube . However, if the more specific route did not have a valid ROA, operators could choose to filter it.
Conclusion
While still leaving a possibility for an attack, origin validation using RPKI can be an effective tool against prefix hijacking and misconfigurations. A more complete solution to this problem will include path validation, the next phase of securing the global routing system.
More importantly, this technology, as well as existing tools like IRRs, can only be helpful if used by the ISP in their provisioning systems and for routing decisions, which is not always the case today.


Comments 0
The comments section is closed for articles published more than a year ago. If you'd like to inform us of any issues, please contact us.