Good intentions don’t always result in good outcomes. This is especially the case with recent suggestions regarding end-to-end-encryption adaptability requirements for number independent communication services. Not only is security an issue, the suggestions themselves go against the design of the Internet, as well as digitisation itself.
This article was runner up in the RIPE Labs article competition for RIPE 91.
The context
Recent years have seen a renewed interest in breaking end-to-end-encryption for communications services to combat organised crime and child sexual abuse, at the EU-level as well as in several member states. This blog post will focus on what has been taking place in Sweden where, since 2023, parts of the Swedish government have been in favour of breaking end-to-end encryption through a proposal to the Swedish parliament. At an EU-level both the former #ChatControl proposal and the current, although yet quite undefined, ProtectEU strategy venture in a similar direction.
There are other parts of the Swedish proposal, such as increased metadata retention, which warrant nuanced discussion (perhaps in a later blogpost). This blogpost focuses on the security issues and the long-term architectural consequences for the Internet and digitisation of breaking end-to-end-encryption.
If you are interested in what has been happening in Sweden, a good place to start is Netnod’s answers to two public consultations in Sweden: Netnod response to the Swedish data storage act and Netnod response to the Swedish Data Storage Act (2).
At an EU-level, the ProtectEU main document mentions the “High Level Group (HLG) on access to data for effective law enforcement” and makes the following statement, which is repeated over and over again as the rationale for breaking end-to-end encryption:
The HLG experts were of the view that a data retention regime should include obligations for service providers to provide data in clear while ensuring strong cybersecurity and full compliance with data protection and privacy law, and without undermining encryption. - Concluding report of the High-Level Group on access to data for effective law enforcement, p. 35
This statement is well intentioned, but is asking for the impossible. It is simply not possible to provide clear text information for a third party outside the communications channel of two parties who encrypt their communications without undermining either the encryption itself or the application running the encryption. This is precisely what the terminology “end-to-end encryption” means, i.e. that the communication is encrypted from end to end, from sending to receiving application or device, without the possibility for any third party along the way to decrypt the traffic.
It should be said here that classical telecommunications services, such as telephony, work in such a way that if communications are encrypted, the telecommunications service holds the keys, or at least one set of keys used for derivation purposes. It’s also worth noting that such classical telecommunications services are often based in singular jurisdictions, so that the users, the provider and the relevant law enforcement agency are under the same laws.
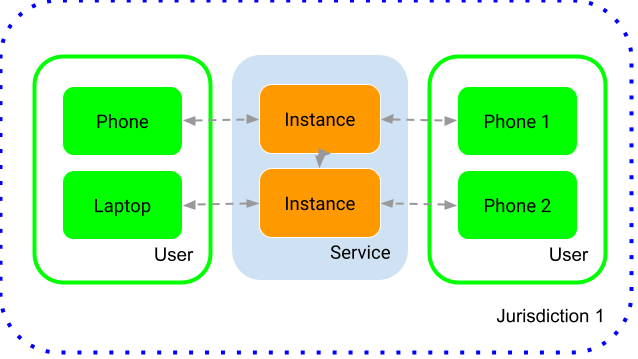
This is not the case for publicly available number independent interpersonal communication services, where service providers can be based in one jurisdiction, running servers in another jurisdiction, with users in many other jurisdictions, and law enforcement in yet another jurisdiction. The previously mentioned HLG report mentions this, but does not provide any solutions. One of the major issues here is that different jurisdictions have different views on who is a criminal. For example, someone who is considered a refugee in one country can be considered a dissident and a criminal in another.
For Internet-based services, it is technically impossible to locate an end-user to a specific jurisdiction with 100% certainty as end-users can, for example, proxy traffic to hide their true network identifier and / or physical location.
Number independent communications services not only include communication apps in app stores, but also email, services used for intra- and inter-business communication, and so forth. The current proposals, as they are written, are ambiguous on whether they also cover VPN-services and similar. In my opinion, I think that the intention is to cover such services as well, if not immediately, then over time.
In addition to the legal issues noted above, there are a range of technical issues that need to be discussed.
Technical issues and the suggested solutions
Encrypted services can be implemented in different ways, but at their core they are quite similar in design. Each participant device in a conversation has a public key and a private key, where the public key is available to all participants in a conversation, and the private key is secret and only exists on one device, and could even reside in a secure element on that device.
These keys are then used to exchange symmetric keys, often called session keys, which stay the same for a specific set of time, or for a specific conversation or thread (for a deeper understanding of how keys can be derived and rotated for a specific implementation or standard, see the Messaging Layer Security Protocol, RFC-9420).
Some services are open source, and can therefore be inspected by third parties, as has been done with Signal here. Being open source also means that clients can be modified, and inspected, even at runtime. I will return to this later.
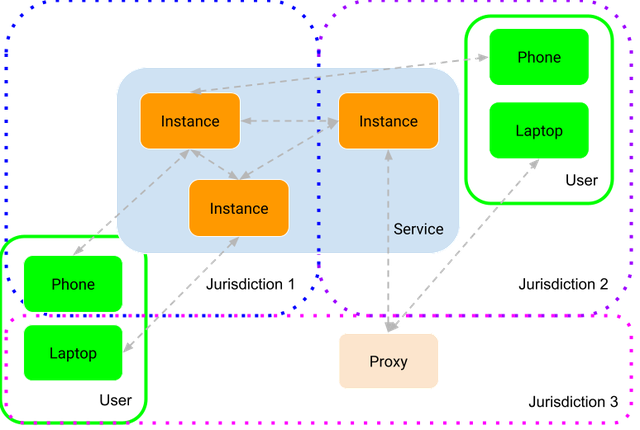
Figure 2 illustrates an example or typical use of number independent communication service usage today. Users often have multiple devices, which do not have to be in the same jurisdiction, and a user can use proxies to connect to the service. This is the case with all Internet services.
Figure 2 and the legislative proposal in Sweden are in the context of number independent communications services intended to be used by individuals, but for all intents and purposes the phone or laptop in the figure could also be a payment terminal, a surveillance camera or a server. As per the Internet model, services can be used by different kinds of users, it does not matter if the message originates from a human or a machine, or if the intended recipient is a human or a machine.
Regardless of who the sender and receiver of the communication are, or what type of information is being communicated, only the sender and the receiver can read the clear text information of the message. This could be a “Hello”, a firmware update, an image, a credit card transaction, an already encrypted message, or something else entirely.
We have discussed several ways which, in a general sense, could be used to implement adaptability requirements on end-to-end encrypted communication. We will now look at two in particular.
Key Escrow
The first solution, key escrow, means that there is a system, somewhere, which has a copy of the keys used for encrypted messages. These copied keys could be session keys, or even the keys used for identifying devices. Depending on the implementation, session keys will allow reading of encrypted messages, and possibly the creation of spoofed messages in an already existing conversation. However, most solutions that I am aware of use keys for signing message hashes as well, so spoofing is not always possible, as the key escrow will lack all keys necessary to fully spoof a client.
The key escrow would here become a primary target for an antagonist who wants access to the encrypted contents of conversations. Such an antagonist might be a sovereign power looking into conversations between politicians in a foreign country, a conversation between security professionals, or engaging in industrial espionage.
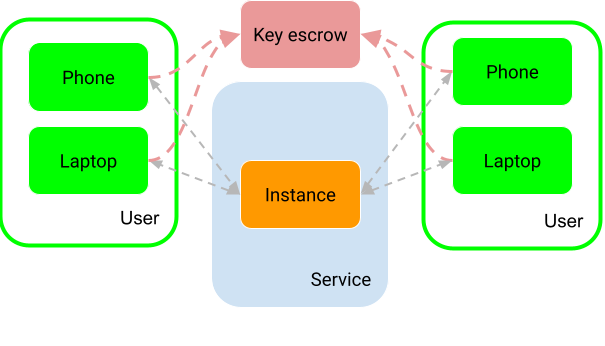
Key escrow can be completely avoided by modifying the client app so that keys are not sent to the key escrow. Real world examples include the Clipper Chip.
Hidden group members
In the second solution, hidden group member, all messages are also sent to a hidden group member, which in reality would be a server hosted by a law enforcement agency or similar which behaves as a normal client, except that it is hidden. This solution implies that end-user applications would need to encrypt additional messages for the hidden group user.
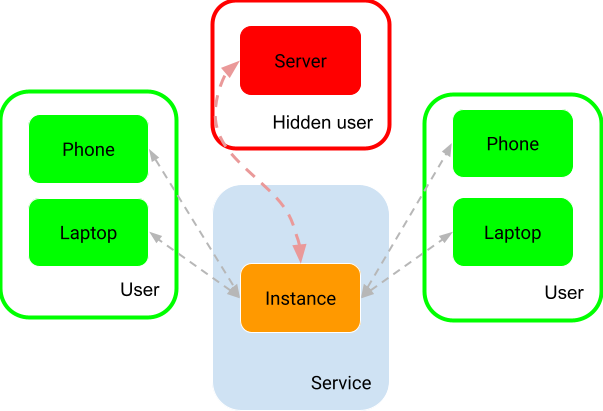
Hidden group user approaches can be completely mitigated by using a modified client app which does not encrypt messages for the hidden user. Wickr uses the hidden group member approach, although they use the expression “Customer-Controlled Data Retention” as the “hidden user” is known to all users for data retention and compliance purposes. The “hidden user” could be hosted by a law enforcement agency, or another entity entirely, and this “hidden user” would be known for any end-user inspecting network traffic or application code.
In short, both methods are easy to avoid for a competent user, and they introduce backdoors and vulnerabilities into the services themselves or the larger ecosystem the services are part of. There are no known successful implementations in terms of ensuring security of either of these two solutions where the key escrow or hidden user organisation is different from the user organisation, or any other solution for that matter, and as assessed by the Swedish Armed Forces:
The Swedish Armed Forces assess that the requirement for adaptability of number-independent interpersonal communication services will not be able to be met without introducing vulnerabilities and backdoors that can be exploited by third parties. - Translated into English from response by Swedish Armed Forces to Ju2024/02286, p. 1.
The architectural error
Taking a step back from the technical and legal aspects of the proposal, it is worth asking: why does this proposal even exist in its current form? I think, and hope, that the proposal stems from well meaning ideas but does not take into account that services today are global, digitised and use the Internet. This means that services are no longer vertically integrated and offered in their entirety within singular jurisdictions.
There is no technical reason to assume that Internet services can be regulated in the same way as vertically integrated telecommunications services. This is mentioned to different extents in the travaux préparatoires of both the European and Swedish codes for electronic communications.
Regulation, as all sanctions and power enacted by governments, needs to be grounded and target legal subjects within their jurisdiction. The cross-border, or rather border-agnostic, nature of many Internet services make Internet services a bad regulatory target.
This is the primary reason Netnod has a strong opinion on the subject. Breaking end-to-end-encryption is dangerous since it cannot be done for Internet-based services without significantly impacting the security of those services. Modern public policy making and governance structures need to account for how the Internet and digitised services functions are built, maintained and developed.
Summary
Though well meaning, the current push towards breaking end-to-end encryption has far reaching consequences. Not only does it impact security but also innovation, as private actors are likely to leave or never enter markets where regulation like this is in place.
It would no longer be possible for private businesses, citizens, refugees or political dissidents to communicate securely without modifying their apps. In some sense, these proposals have no effect on crime-prevention or evidence gathering as the adaptations can be avoided. Rather the requirements introduce backdoors and potential vulnerabilities to be used by competent antagonists.
Lawmakers should take a moment and think: if the main benefactors of the proposed adaptability requirements are foreign state actors, are we sure this is a good idea?
This article was originally published over on the Netnod blog.




Comments 0