Discovering the Discovery of Designated Resolvers
• 6 min read
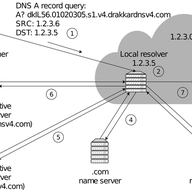
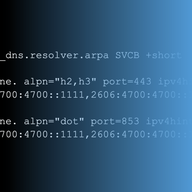
DNS encryption is gaining momentum with proposed standards such as DoT, DoH, and DoQ protecting DNS exchanges from external observers. But these standards introduce non-trivial changes to the original specification. Here we look at the Discovery of Designated Resolvers (DDR) - a mechanism that all…