The secondary IP address market has become a viable source of IPv4 address space, but it may also present opportunities to malicious networks to bypass reputation-based security mechanisms. In this article we summarise the results of our first detailed study of how transferred IPv4 prefixes are misused in the wild by synthesising an array of longitudinal IP blacklists, honeypot data, and AS reputation lists.
This research was funded by the RIPE NCC Community Projects Fund 2019.
The depletion of unallocated IPv4 addresses combined with the slow transition to IPv6 has led to the emergence of a secondary market for transfers of IPv4 addresses.
In 2009, the first documented transfer took place within the ARIN region. Since then, IPv4 transfers have become a viable solution for acquiring IPv4 address space (Figure 1).
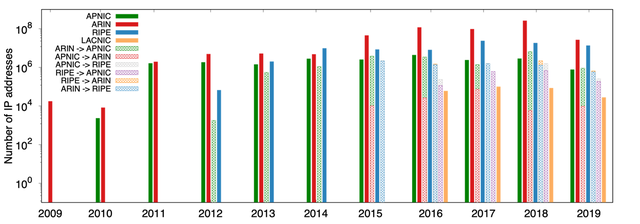
Figure 1: The number of IP addresses involved in intra- and inter-RIR transfers.
The Regional Internet Registries (RIRs) have responded to the emergence of the IPv4 market by establishing policies that aim to safeguard the accuracy of registered IP address blocks and provide oversight and transparency on how organisations trade IPv4 address blocks.
However, there have been multiple reported attempts to exploit the transfer market as part of malicious operations - such as the hijacking of dormant address space and spamming, which, judging by exchanges between operators on mailing lists and messaging boards, is of concern to network operators.
In our recent paper, my colleagues and I at Lancaster University, Simula Metropolitan and the University College London sought to shed light on the misuse and abuse of the IPv4 transfer market and to understand how malicious actors target it.
How we did it
Our overall approach, summarised in Figure 2, aimed to correlate IPv4 address transfers with malicious activity. We collected the list of IPv4 transfers through the RIR reports published between 12 October 2009 and 24 August 2019. To understand malicious activities connected to the transfer prefixes, we synthesised an array of datasets including blacklists, honeypot traces, and reports on prefix hijackers. We used a large array of data sources on malicious activities to address the shortage of longitudinal data on misbehaviour and to explore distinct types of exploits. Consequently, data covered spamming, malware, phishing, unsolicited scans, distribution of unwanted programs and illegal content, Command and Control (C&C) botnet servers, and IP prefix hijacking.
While the reported IPv4 transfers provide only organisation names, malicious data on prefix hijacking and C&C/bulletproof hosters are encoded at the level of Autonomous Systems (ASes). To study the involvement of those ASes in the transfer market we needed to map organisation names to AS Numbers (ASNs).
For 48% of the transfers, we could match the organisation names to ASNs using historical WHOIS data. We mapped an additional 23% of transfers to ASNs by detecting permanent changes in the ASNs that originate a transferred prefix in the BGP routing data when such changes correlated with the reported transfer date.
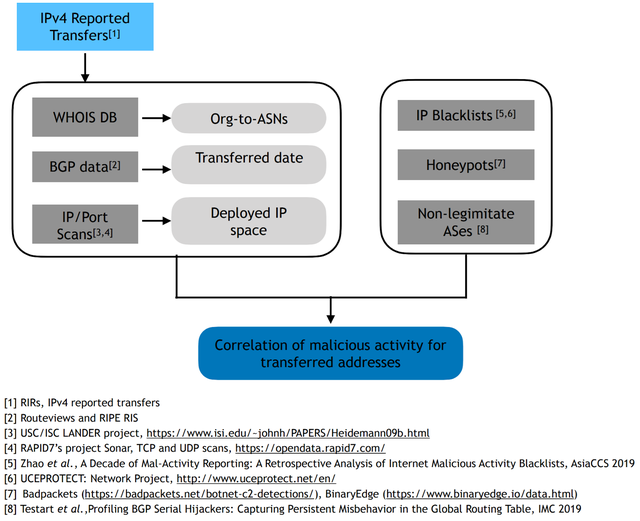
Figure 2: Overview of our method and datasets used to analyse malicious activity correlated with IPv4 transfers
An AS that has part of its address space blacklisted is not necessarily malicious. For example, botnet operators often exploit cloud platforms to deploy malware on short-lived virtual machines to evade detection. Similarly, broadband providers may have large parts of the address space blacklisted because end-users who are not security-aware may have their personal computers infected.
To identify potentially legitimate ASes with a disproportionately high fraction of their addresses blacklisted, we adapted techniques for the identification of Internet hypergiants and large providers. Consequently, we created a dataset of filtered ASes without those legitimate networks to prevent skewing of our results.
A significant percentage of transferred prefixes appear as blacklisted
We compared the malicious activity emanating from transferred and non-transferred prefixes as reflected by the IP blacklist reports. Almost 40% of the transferred prefixes that are routed, i.e. that are visible in the BGP tables of RouteViews and the RIPE Routing Information Service (RIS), have at least one blacklist report, compared to only 6% of the non-transferred routed prefixes (see Figure 3).
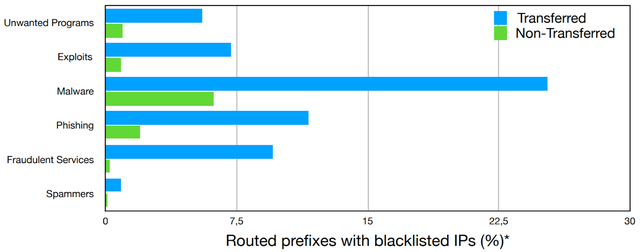
Figure 3: Distribution of transferred and non-transferred prefixes with blacklist reports
Although the blacklisting activity does not originate uniformly across the address space, breaking down the IPv4 space into /24 prefixes results in a similar conclusion: transferred /24 sub-prefixes are 6x more likely to be blacklisted compared to non-transferred prefixes. Moreover, transferred prefixes are disproportionately represented in the blacklist for every type of malicious activity as shown in Figure 4.
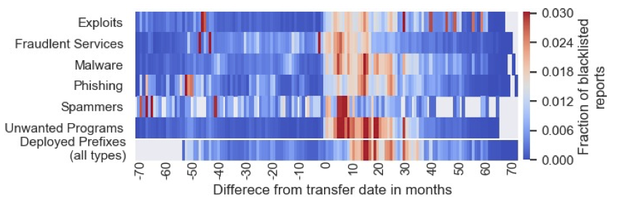
Figure 4: Transferred prefixes are disproportionately represented in blacklists for every type of malicious activity
When do transferred IPv4 addresses get blacklisted?
We also explored the dynamics between malicious activity and IPv4 transfers. Since the date in the transfer reports may not be the exact date when the prefix routing changed, we used the date when the BGP origin ASN changed as a reference transfer date.
Additionally, we analysed only prefixes with IPv4 addresses encountered in longitudinal IP census lists, before and after the effective transfer date, since prefixes whose IPv4 addresses are deployed only after the transfer cannot be encountered in IP blacklists before the transfer. For these active prefixes, we compared the timing of blacklisting to the transfer date.
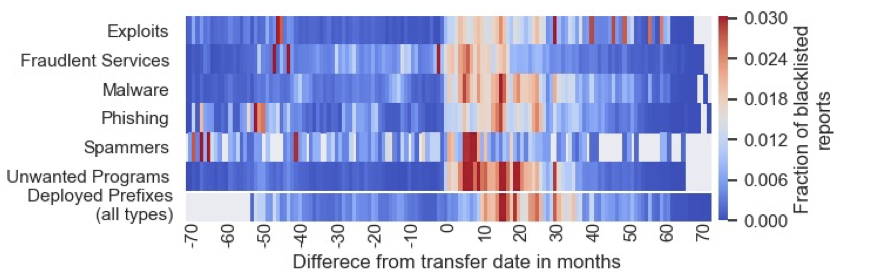
As shown in Figure 5, the number of blacklisted IPv4 addresses peaks within a year of the transfer date for all types of malicious activity. We also found that ASes that are both sellers and buyers of prefixes are twice as likely to have their address space blacklisted, compared to sellers or buyers alone.

Figure 5: Blacklist reports per type of malicious activity for transferred IPs, compared to the transfer date
Next steps
Our findings show that the ASes involved in the transfer market exhibit consistently higher malicious behaviour compared to the rest of the ASes, even when we account for factors such as business models and network span.
We do recognise that our findings are likely to be a lower bound of malicious activity from within transferred IP addresses since a number of transactions may occur without being reported to the RIRs.
As part of our future work, we plan to extend our analysis to non-reported IPv4 transfers and develop predictive techniques for blacklisting based on the monitoring of the IPv4 transfer market. We believe that these insights can inform the discussion and development of RIR policies regarding the regulation of IPv4 markets, and help operators and brokers conduct better-informed due-diligence to avoid the misuse of the transferred address space or unintentionally support malicious actors.
Comments 1
The comments section is closed for articles published more than a year ago. If you'd like to inform us of any issues, please contact us.
Wolfgang Zenker •
That's an interesting analysis. I would also like to see that kind of analysis for the addresses handed out by the RIRs under their "final /8" policies; for RIPE especially with a comparison between members that just got their final /22 and those members that opened additional LIRs to get more addresses. A totally non-scientific look at my own blacklists shows a high number of networks in 185/8, but this might be due to those networks being smaller than average.