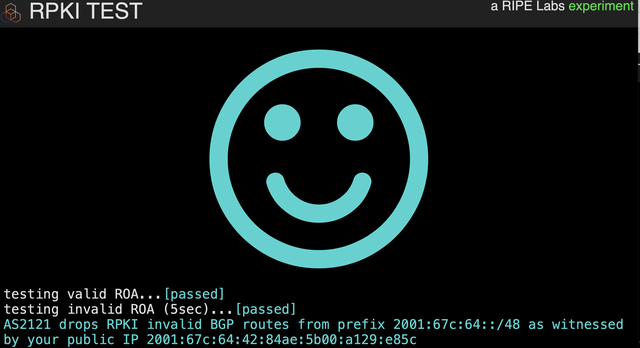
How can you quickly figure out if a network you are using is dropping invalid Resource Public Key Infrastructure (RPKI) BGP announcements? You can do so by opening up a browser and visiting our RPKI test web page.
During RIPE 78, the community asked us to configure the meeting's network in a way so invalid RPKI BGP announcements are dropped. This is indeed the current configuration, but it is not easy to check. So we built an experimental webpage where you can check if the network you are using is doing RPKI Origin Validation.
We have a short URL that redirects to this test page: https://www.ripe.net/s/rpki-test
This is not a new trick, it was also used before for IPv6 testing. To adjust this to work for RPKI, we used two test prefixes (courtesy of NTT Communications):
- One that is covered by a valid ROA
- Another one that is invalid (on purpose of course)
There is a webserver in both that serves content, so if you cannot fetch the content from the invalid and you can do so from the valid, this is a strong indication that the network you are on is dropping invalid RPKI BGP routes.
Please test this tool and check if the network you are on drops invalid RPKI BGP announcements.
Currently, this is only available on IPv4 as we wanted to have this finished before the end of the RIPE 78. We are aiming to make it available to IPv6 too, and be future-proof soon!
If you are interested in what RPKI is, and how it improves routing security, please find more information on our RPKI web pages.
The source code for this little application can found on GitHub.




Comments 12
The comments section is closed for articles published more than a year ago. If you'd like to inform us of any issues, please contact us.
Ondřej Caletka •
Awesome job, thank you for that! Just don't forget to deploy HTTPS for the test as well. Actually, it may be an interesting test how easily one can do domain control validation for a domain name pointing to a network with an invalid ROA.
Alex Band •
This is brilliant! By the way, the RIPE NCC also has RIS beacons with each RPKI Validation state that can be used for this purpose: https://labs.ripe.net/Members/markd/routing-certification-beacons/
Jac •
These RIS servers (and other tools) will slowly become blind to RPKI invalid routes as these get dropped more and more by ISPs.
Arnold Dechamps •
Will it soon be available to test IPv6?
Nathalie Trenaman •
Hi Arnold, we are working on it, and hope to have this enabled in about a week. Stay tuned!
Konstantin •
Please, enable IPv6 validation :)
Milan Pässler •
Unfortunately the test fails for me with the following message: "testing valid ROA...[error (what does that mean?)]![passed]" https://img.pbb.lc/id/N4A1VRYFq6muEsbs
Jasper den Hertog •
Hi Milan, what happens is that the test receives an error instead of a timeout for the request over the invalid path. The test doesn't exactly know what to do with that, hence the error message you're seeing. The CORS warning is not relevant here, that just tells us that the error response doesn't have the right headers (very common). I've seen instances where the invalid path is not dropped (so no response, so the test goes to timeout) but actually rejected with an error response. This may be the case with the response you're seeing (I am not sure, maybe if you expand the `events` object in the console and then expand the `invalidAwait` event in there, you would see a more elaborate error message). The trouble is that I've no clue what thing generates this rejection (middlebox? firewall?). As a consequence the test is not sure what to do with it.
Tassos •
Any news about IPv6 prefixes support?
Jbond •
Thanks for the great work, Is there a plan to release the code?
Jasper den Hertog •
hi John, The code is release and it lives here: https://github.com/density215/rpki-web-test (sorry for the late reply)
Stefano •
The test does not work anymore since a few weeks. Any update?