Phishing attacks are, to this day, one of the most widespread and effective means of getting access to sensitive and financial data. A new study from the team from SIDN Labs combines more than 28,000 phishing domain names in a bid to improve detection and mitigation policies.
Phishing attacks, which trick users into sharing private data, have been a major security threat for years. According to a 2023 FBI report, it is the top digital crime type. In Europe, ENISA states in its 2023 report that "phishing is once again the most common vector for initial access".
In a recent peer-reviewed paper, we reported a longitudinal study characterising phishing attacks observed at three European ccTLDs: the Netherlands' .nl (managed by SIDN), Ireland's .ie (managed by the .IE Registry) and Belgium’s .be (managed by DNS Belgium).
While the ancient Romans loved to mix various fish to create the infamous fish sauce called Garum, we instead combine more than 28,000 phishing domain names with the goal of improving the registries' detection and mitigation policies – the largest study to date. Let’s dive into our findings.
ccTLDs compared
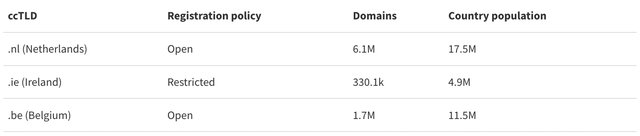
The ccTLDs we evaluate in this study have different characteristics, as shown in the table below:
- Number of domain names: we see a large variation in number of domain names (330k for .ie, to 6.1M to .nl )
- Registration policies: .nl and .be have open registration, meaning anyone can register domain names under their zone, whereas .ie has a restricted registration policy – only individuals and businesses related to Ireland can register domain names.
These differences are taken into account during our analysis.
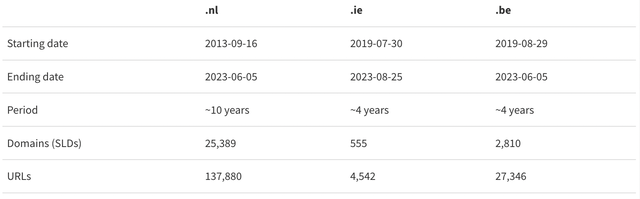
Phishing datasets
The table below presents the phishing datasets we evaluated for each ccTLD. The phishing URLs were obtained from Netcraft, a commercial phishing blocklist provider used by all our registries. Each registry has access only to domain names in its own ccTLD, and has access to historical data. There are other phishing blocklists, and we evaluated a second one in the paper – however, we chose Netcraft in our paper for its coverage and low false positive rates.
Do ccTLDs matter when choosing who to impersonate ?
ccTLDs are closely tied to their countries, with governments, individuals and businesses frequently using them for their domain names. In a way, a ccTLD can be seen as a brand, and humans assign trust levels to brands. We explore whether attackers exploit this trust for phishing attacks.
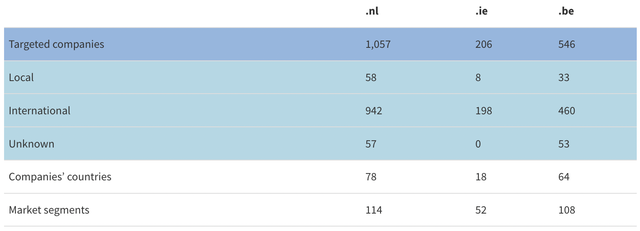
The table below shows that, for the three ccTLDs, most of the impersonated companies are international rather than based in the ccTLD’s country. For instance, we see phishing attacks targeting Asian and African banks using .nl domains, and Microsoft is the most frequently impersonated company across all three ccTLDs. These domains cover up to 78 countries and span 114 market segments, indicating that ccTLDs are being used for global impersonation.
The figure below highlights the most targeted market segments in ccTLDs, based on the number of second-level domains (SLDs). Banking and financial services top the list across all three ccTLDs. Interestingly, these segments were also offered by LabHost, a phishing-as-a-service provider that was shut down in April 2024.

One might conclude that attackers don’t care which ccTLD they use for phishing attacks. But is that really the case?
Two attack strategies
Well, that does not stand close scrutiny, when it includes the domain name age at the phishing notification date. Then, a clear pattern emerges, for both .be and .nl ccTLDs:
- New domains target national companies.
- Old domains target international companies.
So, why this clear difference?
We hypothesise that there are two attack strategies.
- Attackers impersonating national companies prefer to register and host their own domains given they can choose domains that sound like the legit ones, for example,
revalidate-card-bank.nl. A domain name like this, which has the same ccTLD as the original one from the bank, in the local language ( Dutch for the Netherlands), has a higher chance of successfully deceiving users that if it was hosted on a domain likeflowershop.jp, which has a different TLD and no banking keywords. - Attackers impersonating international companies – at least the ones we see in .nl and .be – attackers are indifferent to the ccTLD. They prefer to compromise someone else’s website, given it’s a free resource, in order to carry out their campaigns. (Previous research has shown that websites are often scanned for CMS vulnerabilities). For these attackers, it doesn’t matter if the domain is
flowershop.jpwhen impersonating a South African bank or an American credit union.
This distribution boils down to the attacker’s choice: pay for a domain name, hosting and DNS service to get a cherry-picked name, or go cheap and use someone else’s resources?
Our data shows the following patterns: 20% of phishing attacks use new (maliciously registered) domain names, targeting less than 5% of companies, mostly local. Meanwhile, 80% of attacks use old (likely compromised) domain names, targeting most companies.
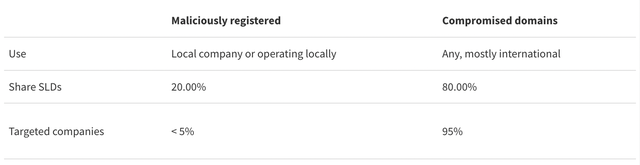
The table below shows the total number of impersonated companies and SLDs used, for companies from all countries and for companies from the ccTLD's own country.
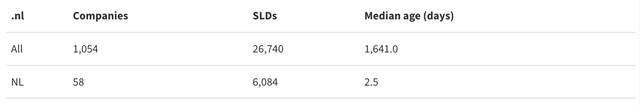
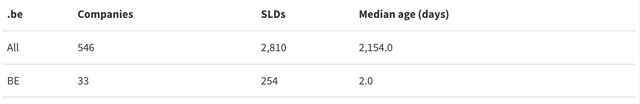
But what about .ie domain names? Why doesn’t this apply to them? Well, .ie has a restricted registration policy, which prevents attackers from easily registering new domains for abuse (though they have done so in the past using forged documents). This policy effectively inhibits phishing attacks using new domains but, unfortunately, doesn’t help with compromised domain names.
Takeaway: phishers can be classified into two groups based on the domain names they use:
- Local attackers: prefer to register new domains to target national companies.
- Other attackers: use any domains to target companies elsewhere.
For our ccTLDs, most attacks actually use old, likely compromised domain names.
Comparing targeted brands across ccTLDs
When we compare the brands which were impersonated in each ccTLD, we see the Venn diagram below.
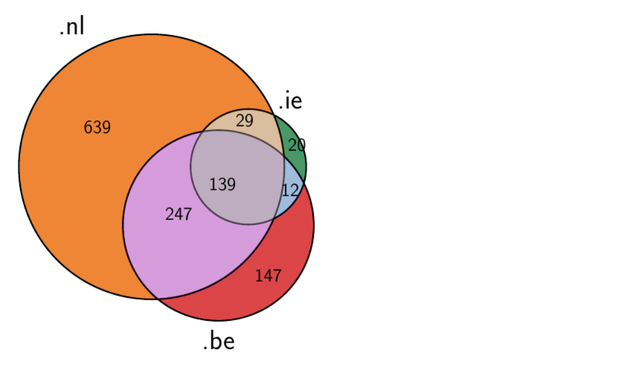
We can observe that:
- 139 companies (11% of total) are found in all ccTLDs. These include global internet giants like Microsoft, Google, Netflix and PayPal. They account for 58% of all SLDs used in attacks.
- 247 companies are impersonated using both .nl and .be domains. Given their cultural, language and financial ties, companies often operate in both countries, explaining the choice of using a .nl or .be domain.
- The remaining companies appear randomly. .nl sees 639 more companies than the rest due to its larger attack surface (6.1M domain names) and the use of almost 10 years of data, compared to 4 years for the others.
Mitigation
Phishing mitigation can occur at two application levels: DNS and web, or both. At the DNS level, the domain name used in phishing can be deleted from the namespace and from the zone file. It can also be suspended, where it is deleted ("delisted") from the DNS zone but not from the namespace. Lastly, it can remain in the zone and namespace, but have its authoritative DNS servers (NS records) changed to a safe server. At web level, it can simply be removed from the website.
Each ccTLD has its own abuse mitigation policy (see .nl, .ie for complete policies).
If a phishing attack is confirmed, for new domain names:
- .be: suspends the domain as soon as possible.
- .nl: notifies other parties (registrar, hosting provider, etc.) and waits 66h. If not fixed, the domain is suspended.
- .ie: does not suspend, as most phishing involves compromised domain names that can be fixed with web mitigation.
We examined the mitigation of phishing domain names for the ccTLDs.
So the type of domain name also influences how it is mitigated:
- Old, compromised domains: for all ccTLDs, there is little DNS-level mitigation. Instead, mitigation occurs at the web application level, handled by hosting providers. For example, if your neighbourhood bakery’s website gets compromised and hosts phishing content.
- Newly registered domains: likely registered by the attacker, these see a mix of DNS and web-level mitigation, depending on the ccTLD. If the domain is maliciously registered, DNS-level mitigation makes sense. For example,
santander-card-update.tldis very likely fake, and the longer it stays online, the more victims it attracts.
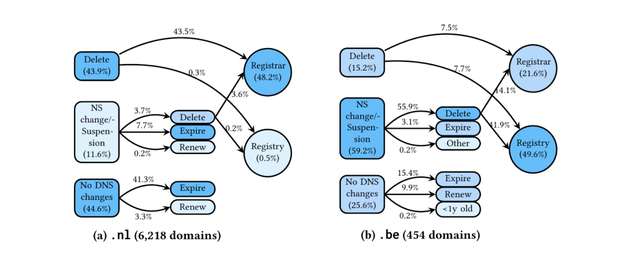
The figure below shows the mitigation chain for all new domain names (<7 days old) for both .nl and .be (recall .ie has a restricted registration policy). The impact of the registry’s policy is clear:
- .nl: 55% of maliciously registered domain names are mitigated at the DNS level, mostly by registrars (48.2%).
- .be: 75% of maliciously registered domain names are mitigated at the DNS level, mostly by the registry (49.6%).
In other words, .be actively removes these domains, while .nl relies on registrars to handle most mitigation first.
Mitigation times
Time is of the essence when mitigating phishing. In the left-hand figure below, we see that, at the DNS level, more than 60% of .be domains are mitigated on the first day, whereas for .nl, that figure is around 40%. However, when considering both DNS and web mitigation together (as reported by Netcraft, available only for .nl and .ie as an extra service), the right-hand figure shows that roughly 80% of domains are mitigated on the first day for .nl, for both new and old domains, and almost at the same rate for .ie.
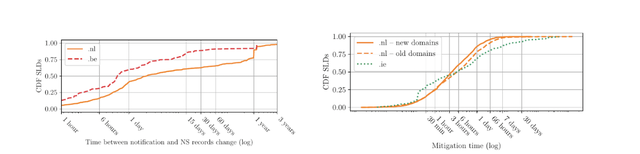
So, what can we conclude from this? Phishing mitigation is not a single event carried out by one actor. In practice, actions are taken independently by registrars, registries, hosting providers and webmasters to mitigate phishing attacks. The right-hand figure above shows the impact of this collaborative effort — phishing sites are mitigated much faster than they could be by a registry acting alone.
What’s next
Our study is the first to compare abuse across three registries with different registration policies. We have demonstrated the impact of both registration and abuse mitigation policies on overall phishing mitigation. Some hackers leverage the ccTLD's brand to impersonate national companies, while most attackers act as freeloaders, exploiting others’ resources — specifically, their vulnerable websites.
We propose the following action points from our study:
- More research on compromised domain names: most research focuses on newly registered domains. We call for action to detect, characterise and mitigate compromised domains, which constitute the bulk of phishing domains, accounting for 80% of current phishing attacks.
- Revisiting registry policies: the results of this research are being discussed internally by the ccTLDs and may lead to policy adjustments to keep up with attackers’ evolving strategies.
For more details of this research and other results, please refer to the peer-reviewed paper that will appear in the 2024 ACM Conference on Computer and Communications Security (CCS 2024).




Comments 0
The comments section is closed for articles published more than a year ago. If you'd like to inform us of any issues, please contact us.