Ahead of CAPIF 4, we once again pause to examine the latest in Central Asia’s digital transformation. Against a backdrop of deepening regional cooperation, we chart improvements in routing security and IPv6 adoption, while also probing interconnection patterns as seen in K-root data.
Cкачайте перевод статьи на русский язык
As we return to Kazakhstan for the fourth RIPE NCC Central Asian Peering and Interconnection Forum (CAPIF 4), we find a region with deepening local ties and a strong sense of its role as a vital digital crossroads. Regional cooperation has advanced over the past year through border settlements and trade agreements, and international engagement continues via platforms such as the SCO, the C5+1, and the CIS.
The rapid development of the local Internet continues apace, with clear signs that the region is set on shaping the architecture of its own digital future. In his recent Address to the Nation, Kazakhstan’s President Kassym-Jomart Tokayev set out plans to make Kazakhstan a “fully digital nation” within three years, pointing to a heavy strategic focus on AI adoption. Meanwhile, Uzbekistan’s ‘Uzbekistan–2030’ strategy sets the goal of transforming the country into a regional IT hub, with an estimated $3 billion having already been invested in the sector in recent years.
Our goal here is to once again plot out a new set of data points to help track the trajectory of Central Asia’s digital transformation. We’ll look for improvements in routing security - particularly in terms of ROA and ROV deployment - and IPv6 adoption since CAPIF 3. We’ll examine government infrastructure and RPKI adoption across government domains. And we'll be looking at DNS query distribution across the K-root anycast network to map the region's foundational BGP routing preferences and traffic localisation.
As in earlier reports, we’ll also track similar developments in Iran - an active CAPIF participant from the start, whose geography positions it as a gateway linking landlocked Central Asia to the Middle East and Europe, making it a key stakeholder in resilient interconnection in the region.
Overview of resources in Central Asia
IP addresses are critical elements of our connected world, serving as essential unique identifiers for every device connected to the Internet.
In the face of Central Asia’s accelerating digital growth, the availability of both IPv4 and IPv6 resources is becoming increasingly important to meet rising demand. The exhaustion of IPv4 (more on that here) makes the transition to IPv6 essential for accommodating future growth.
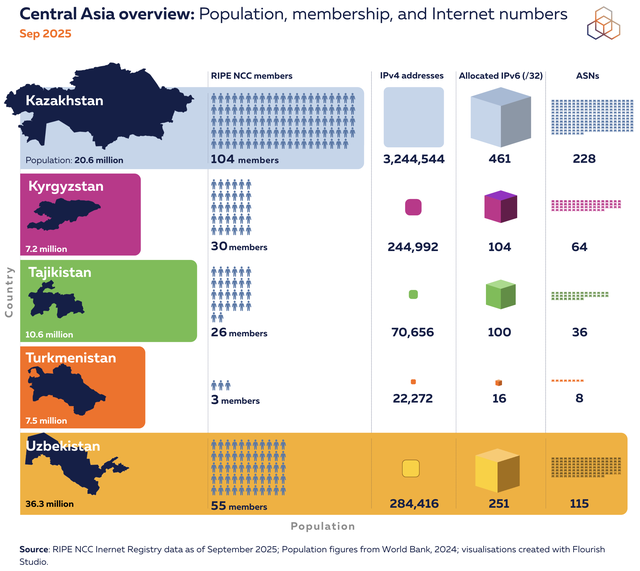
Analysis of resource distribution reveals significant regional disparities. Kazakhstan shows the highest ratio of RIPE NCC members to its population in the region, followed by Kyrgyzstan. In contrast, Uzbekistan, despite its larger population, exhibits a lower member-to-population ratio and fewer allocated IPv4 addresses per capita. However, its IPv6 allocation per member is comparable to regional peers, indicating readiness for future network expansion.
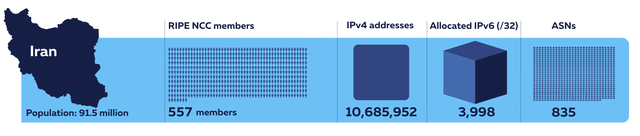
On a different scale, Iran's network landscape is substantially larger. It holds significantly more IPv4 and IPv6 address space and possesses a greater number of active Autonomous System Numbers (ASNs). This reflects a more mature and densely interconnected internet ecosystem compared to the Central Asian nations.
K-root and interconnectivity
The DNS maps human readable domain names to machine readable IP addresses. The RIPE NCC operates K-root, one of the 13 authoritative root servers for the DNS root zone.
To understand real-world Internet connectivity, our analysis examines DNS queries sent from each country's resolvers to the K-root global anycast network. K-root, operated by the RIPE NCC, is a fundamental part of the Internet's infrastructure, its servers being responsible for the first step in resolving most domain names. By observing which specific K-root server instance answers a query, we can map a country's foundational BGP routing preferences, revealing whether its internet traffic is localised or distributed across various regional and international hubs.
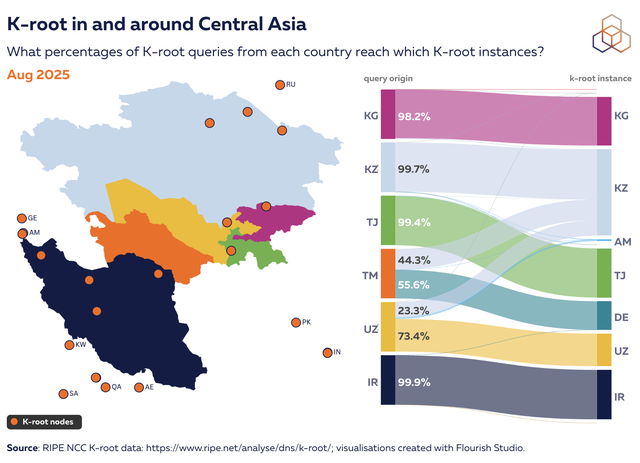
Across Central Asia and neighbouring countries that host their own K-root instances, such as Iran, Kazakhstan, and Tajikistan, traffic patterns are highly uniform on 1 August 2025. The figure shows the distribution of queries from resolver IPs, geo-located using IPinfo, to the K-root instances that handle their traffic. In these countries, the vast majority of queries are served by the local instance, reflecting strong domestic catchments.
Uzbekistan stands out: on the same date, roughly two-thirds of queries reached the instance in UZ, while about one-third were served by the instance in Kazakhstan, with a smaller share directed to Armenia. Turkmenistan, by contrast, has no local instance, and its traffic is split between instances in Kazakhstan and Germany.
Our analysis, based on resolver IPs rather than direct end-user traffic, highlights a marked contrast with neighbouring countries. While IP-based geolocation can introduce some uncertainty, the differences in catchment behaviour remain striking. We will examine potential drivers of these patterns in more detail during the presentation.
To learn more, watch the presentation from James Cowie on 25 September at CAPIF 4.
Routing security
RPKI allows IP address space holders to publish Route Origin Authorisations (ROAs), which specify which ASes are authorised to originate their prefixes. Through Route Origin Validation (ROV), networks validate BGP announcements against published ROAs, allowing them to reject announcements with unauthorised origin ASes and thereby mitigating prefix hijacks and certain origin misconfigurations.
RPKI provides a cryptographic framework that allows operators to verify whether BGP announcements are consistent with the origin authorisations published by prefix holders. Below we show BGP route origin incidents in Central Asia and neighbouring countries as seen by the Global Routing Intelligence Platform (GRIP). Each incident is counted once per country, using GRIP’s unique event ID together with the set of ASNs involved (both originating and covered/affected).
GRIP provides near-real-time observability of suspicious BGP routing events, including:
- MOAS (Multiple Origin AS): where the same prefix is announced by more than one AS
- Sub-MOAS: an event in which an AS announces a more specific prefix that lies within a covering prefix announced by another AS
Our analysis focuses on MOAS and Sub-MOAS events, as these can be mitigated by RPKI when invalid origins are detected, limiting their propagation in networks that enforce Route Origin Validation. To add geographic context, each ASN involved is annotated with its country of registration as recorded in the RIPE Database. We note that registration country does not necessarily reflect where an AS operates.
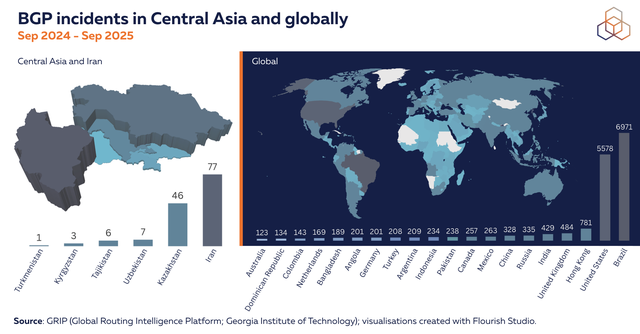
While the number of incidents across Central Asia and Iran is relatively low when compared to global figures, making good decisions around routing security now will help ensure a stable routing ecosystem as the region’s Internet matures.
ROA coverage
At present, ROA coverage in the region varies across countries, with only very slight changes since our last report.
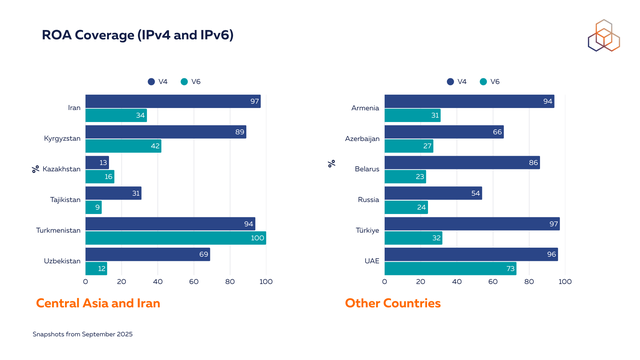
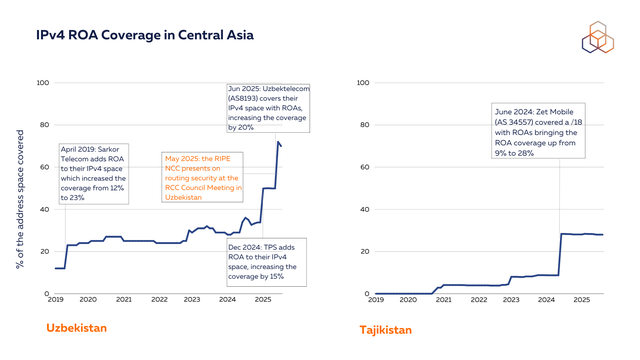
There have, however, been notable improvements in Uzbekistan’s IPv4 ROA coverage that grew from under 40% last year to about 70% this year. In May 2025, the RIPE NCC had engagements on routing security with the Uzbek Ministry of Digital Technologies and presented at the RCC Council of Operators meeting that was held in Tashkent.
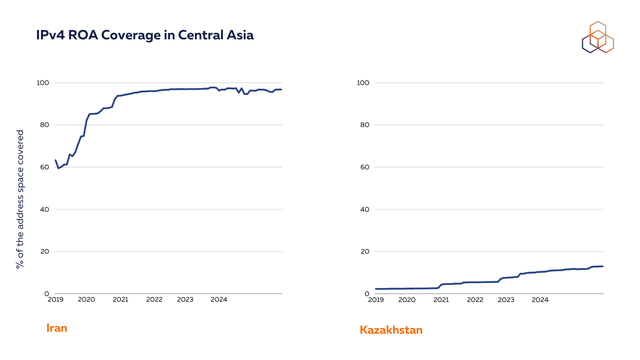
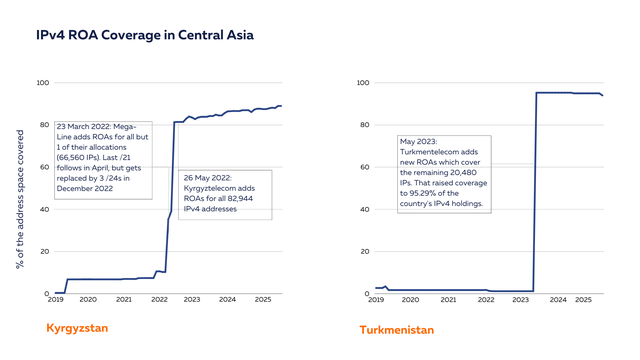
Turkmenistan, Kyrgyzstan and Iran have a very high level of ROA coverage for their IPv4 address space. Meanwhile, for Kazakhstan and Tajikistan, this remains low. It is important to note that we measure the coverage in % of address space, so the numbers are relative to the resources registered in each country.
Protecting digital infrastructure for government domains
As countries in the region accelerate their digital agendas across all sectors, from e-government to essential services, it becomes crucial that government infrastructure is both resilient and secure. Most government websites across Central Asia are registered under national ‘.gov’ second-level domains (e.g.: .gov.kg; .gov.uz). This year in Uzbekistan it was announced that, as of 1 March, all official websites for government agencies in Uzbekistan started to operate exclusively on the Government Portal (gov.uz) as part of broader reforms on digitalisation and security. This can help ensure a more consistent and centralised approach to security, providing a single point of control for monitoring, auditing, and policy enforcement.
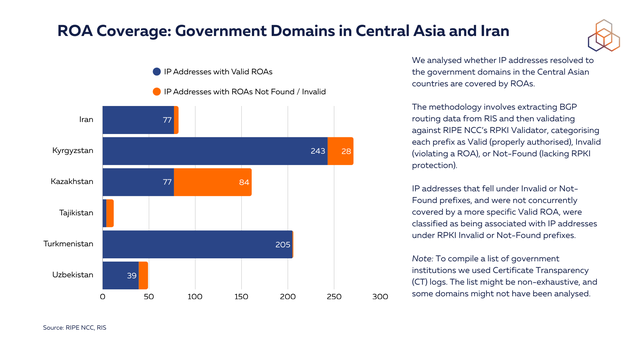
To assess the security of these domains, we wanted to examine their ROA coverage. To do this, we extracted the relevant BGP routing data from RIS and then validated against RIPE NCC’s RPKI Validator, categorising each prefix as Valid (properly authorised), Invalid (violating a ROA), or Not-Found (lacking RPKI protection). IP addresses that resolved to these domains and fell under RPKI Invalid or Not-Found prefixes - and were not concurrently covered by a more specific Valid ROA - were classified as belonging to RPKI Invalid or Not-Found prefixes (to see how we compiled a list of government domain, see the note at the bottom of this article.)
The graph below shows counts for IP addresses behind the identified domains that are and are not covered by ROAs. The results point to varying levels of ROA adoption among government domains in the analysed countries. For example, in Iran, of 114 tested domains and subdomains (82 IP addresses), only 5 were not covered by ROAs. In Kazakhstan of 420 domains and subdomains tested (271 IP addresses), 238 (84 IP addresses) were not covered.
ROV: From authorisation to validation
To analyse the deployment and impact of ROV in the region, we combined data from RoVISTA with a view of network centrality derived from AS Hegemony methodology, an approach that gives us a measure of the centrality of autonomous systems within a country.
Based on what we see in the RoVISTA data, there seem to have been positive changes in both Kyrgyzstan and Turkmenistan. In Kyrgyzstan, networks such as ElCat (AS8449) and Megaline (AS41750) - or their upstreams - seem to deploy ROV. Elcat also has a particularly high hegemony score, suggesting that it plays a significant role for interconnection in the country. By deploying ROV (themselves or by their upstreams), they create substantial collateral benefits, enhancing routing security for their downstream networks, whether from malicious prefix origin hijacks or accidental misconfigurations.

According to RoVista, ROV is now visible in paths involving Turkmentelecom in Turkmenistan, suggesting that invalid announcements are being filtered either by Turkmentelecom itself or by one of its upstream providers. However, it’s important to note that the ROV data can have biases, as the score can vary significantly from day to day.

To help you explore this data further, take a look at this interactive version of the above visualisation in Flourish Studio.
Improving routing security in Central Asia is a shared responsibility. Network operators play the central role, but governments and industry bodies can support progress through policy, training, and outreach. As digital infrastructure in the region continues to expand, consistent implementation of route security measures like RPKI will be essential to maintaining stability and trust in the global routing system.
IPv6 uptake
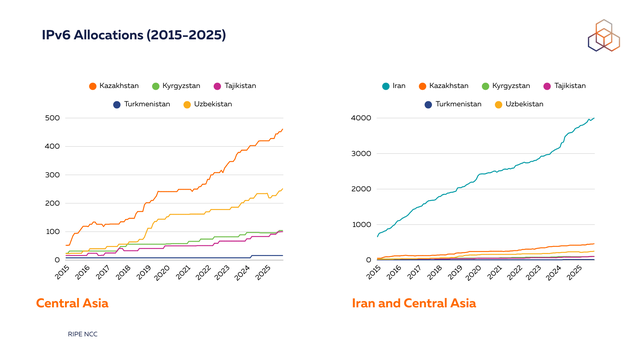
IPv6 allocations have been steadily growing in the region in recent years. Iran has significantly more IPv6 allocations than the five Central Asian republics (see graph below for comparison), highlighting both the scale of its Internet market and the stronger push for IPv6 deployment by its operators. However, the steady growth across Central Asia suggests increasing readiness for IPv6 adoption and future integration into the global Internet ecosystem.
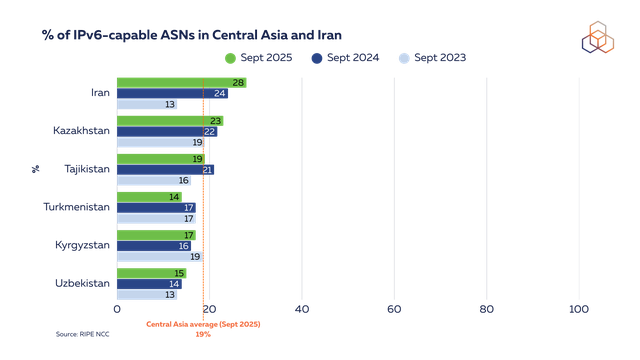
Since CAPIF 3, there have been no striking changes in IPv6 capability. Iran still leads at 28%, followed by Kazakhstan with 23% and Tajikistan with 19%. Average capability across the region has increased by just 1% this year to 19%.
While IPv6 capability indicates the readiness of networks to use IPv6, actual adoption is not easy to measure. We looked at measurements reported by some major Content Delivery Networks (CDNs) on IPv6 adoption in the region. Recent data reveals varying levels of IPv6 adoption across Central Asia and Iran. Kazakhstan and Iran are leading in IPv6 adoption with varying levels reported by Google, Facebook, and Cloudflare. The latter’s IPv6 acceleration is majorly driven by IPv6 Council, the national body promoting best practices for IPv6 deployment. In Uzbekistan, IPv6 adoption was at 0% as of September 2024, though efforts on this front were officially launched the previous year through collaboration between RIPE NCC and the national telecom operator Uzbektelecom. As of September 2025, the adoption rate had risen significantly to 14%, reflecting real progress in deployment.

Towards a resilient and secure Central Asian Internet
Central Asia’s Internet is evolving rapidly, shaped by both strong national ambitions and growing regional cooperation. Progress in routing security - through wider ROA coverage and initial steps in ROV deployment in Turkmenistan and Kyrgyzstan - highlights a strengthening commitment to resilience. Uzbekistan’s rapid rise in IPv6 adoption and improvements in routing security across the region reflect growing commitment from governments, operators, and international partners. Of course, challenges remain. But the momentum is clear: Central Asia is positioning itself as an active player in shaping a secure, connected, and future-ready digital landscape.
Join us at the fourth edition of the Central Asia Peering and Interconnection Forum (CAPIF 4) to be part of the discussion around the future resilience and interconnection in Central Asia.
Note on methodology
To compile a list of government domains, we utilised Certificate Transparency (CT) logs, which are publicly accessible records of all issued SSL/TLS certificates. The primary tool for this is crt.sh, a web-based interface that allows for searching these extensive logs.
The methodology involves querying crt.sh with a wildcard search for a specific government top-level domain, such as %.gov.xx. This initial query retrieves all certificates issued for subdomains under that parent domain. The raw data from these certificates, including common names and subject alternative names, is then systematically extracted and normalised. This involves cleaning the data by removing wildcard prefixes (e.g., converting *.example.gov to example.gov), splitting entries that contain multiple domain names, and standardising the text to create a clean, deduplicated list of unique government hostnames.








Comments 0