How Secure Are My Sessions?

Kathleen Moriarty, founder of SecurityBiaS is technology strategist and board advisor, working with SaaS providers on security to Build-in at Scale benefiting both the provider and their customer base. Adjunct Professor at Georgetown SCS, teaching Security Architecture and Design and Cyber Threat Intelligence. Formerly as the Chief Technology Officer, Center … More
• 10 min read
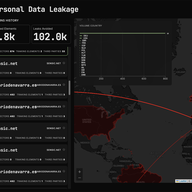
TLS session security isn't just about encryption - it’s about where and how that encryption is terminated. This article explores common risks in TLS deployments and how to align them with modern security principles like Zero Trust.