Twelve Steps to Enable IPv6 in Government and Enterprise Networks
• 10 min read
In the first part of this two-part series, I shared a recent IPv6 deployment case study I worked on for a government network in the LACNIC region, concentrating on the hereditary peculiarities in the network that we had to overcome, many of which are common among government and organisational netwo…

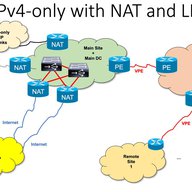



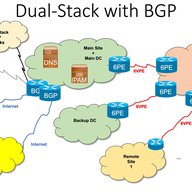
“In the diagram, why are the IPv6-related options rendered in orange, suggesting danger, while the IPv4-related options are all rendered in green, despite their generally higher cost and/or longer lead times?”
Very good points ... I guess was not on purpose, but worth considering replacing the colors and making sure it doesn't happen again.
“Jordi, you bring up good points about 464XLAT and CGN challenges. But why label Jolita’s comment as spam? IPXO is the only platform fully compliant with all RIR policies, supporting thousands of businesses globally in accessing IPv4 addresses. Isn’t that a valuable solution for those still navigating the IPv6 transition?”
Because articles aren't to promote specific companies? I don't think, in general, any company should be allowed to be self-promoted by "opinions" in an article. Not going to respond if IPXO or other brokers are or not fully compliant with all RIR policies ... Not planing to loop around this thread, so not responding again to this kind of questions.
“IPv4 leasing would be a fantastic addition to the list, since it's a quick, flexible way to get IPs without the long-term commitment. IPXO makes it easy and affordable to lease and manage them. Worth considering!”
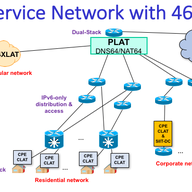
The previous message clearly is a marketing spam and I don't think should be authorized, specially considering that the report already mention leasing (renting). Instead, I think the report is missing the use of 464XLAT (IPv6-only as a Service), as a cheaper way to avoid CGN. Also the report doesn't mention the danger of CGN, with services such as Sony PSN that block for ever the IPv4 ranges used in CGN, so the cost of the CGN and every 6-8 months of IPv4 address space, exceeds the cost of an actual IPv6-only with IPv4aaS deployment.
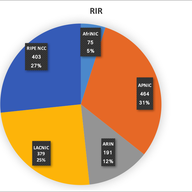
I feel that the main problem in this region is that we allow a "wild west" by not requiring justification of the need in transfers and we should resolve that. Same with the lack of policy regarding leasing. All this clearly goes against the community and the membership. To make it worst, address-policy WG chairs ignore proposals from community members which will facilitate the allocation of IPv6 (avoiding the need for at least some of those transfers), against the PDP, and discriminate those members by "selecting" by themselves that a later submitted policy proposal is accepted or presented in the WG instead of the 1st one already submitted much ahead, disallowing the normal community defined process, presumably even against the code of conduct. No wonder that the community just don't care and avoids investing time in discussing topics that the staff warned about and some participants submitted proposals that have been ignored, for example for the ASs. Going back to the specific topic in this posting, it will be interesting to know if the NCC is getting escalated abuse reports coming from those IPv6 blocks or any other information that can tell us how much of that space is being used for good and bad.
A clear change should be the title of the ICP-2, something like "ICP-2 - Criteria for the establishment Regional Internet Registries and obligations for their continued recognition"
“Hi, Jordi: 0) There is still time. 1) Please have a look at the following discussion thread on the "state of IPv6", http://www.circleid.com/posts/20190529_digging_into_ipv6_traffic_to_google_is_28_percent_deployment_limit/ 2) Then, you may like to have a look at the feasibility demonstration report below about our proposal for expanding IPv4 address pool, etc.: https://www.avinta.com/phoenix-1/home/RegionalAreaNetworkArchitecture.pdf These should provide some material for furthering the dialog. Abe (2020-08-29 22:31 EDT)”
The Ericsson publicacion has a lot of wrong misconceptions as starting point and consequently, anything that starts from there, is broken. When and if IETF approves the use of 240/4, and all the vendors start having firmware updated to users to support it, then we can talk about this. Meanwhile, the only solution *BEING* deployed, is IPv6.
Very informative. Thanks a lot! I love the "legacy IPv4" bit :--)
Hi Axel, I can't let you go without saying this: Yes please, join the mailing list. Now that you will be non-staff (I always said that staff is also community and should be able to speak openly from a personal perspective + additional knowledge), you can contribute a lot with your "internal" knowledge of so many aspects that aren't easy to see from the community side. Thanks!
Of course, the problem of this system is that *ANY* valid email will pass the validation, even if actually is from someone else and not just a real abuse contact ... For example, a bad guy can just find the RIPE NCC contact email, and use that one. Nobody will notice, the validation will pass. We need something else. Stay tuned!
“It may seem to be after the fact. However, with so many twists involved in rolling out IPv6 because it was not designed with the very basic engineering discipline of being backward compatible with IPv4, we really should look at the whole thing seriously one more time. Below is the result of a study that we accidentally ventured into. It utilizes nothing more than the original RFC791 and the long-reserved yet hardly-utilized 240/4 address block. We call it EzIP (phonetic for Easy IPv4) and submitted a draft to IETF: https://tools.ietf.org/html/draft-chen-ati-adaptive-ipv4-address-space-03 Basically, the EzIP approach will not only resolve IPv4 address shortage issues, but also largely mitigate the root cause to cyber security vulnerabilities, plus open up new possibilities for the Internet, all within the confines of the IPv4 domain. In fact, this scheme may be deployed "stealthily" at isolated sites where needed. These should relieve the urgency to deploy the IPv6 for an appreciable length of time. Any thought or comment would be much appreciated. Abe (2018-07-13 16:39)”
I really think is too late to consider other approaches. IPv6 is already there and artificially extending IPv4 life is a non-sense in my opinion. We just need to make sure that IPv6 continues being deployed and customers with IPv4 needs can also get that service, even if this is somehow limited.
Showing 26 comment(s)