Maria Farrell - Break Ground. Plant Seeds. Rewild the Internet!


Alun Davies
Based in Amsterdam
Hailing from a research background in philosophy, linguistics and computer science, I came to the RIPE NCC back in 2016 and took on the role of RIPE Labs Editor in 2020. More
• 2 min read
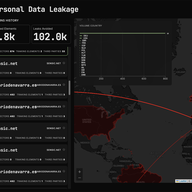
The Internet has long been fertile ground for innovative technologies to grow and openly compete. But having emerged out of these conditions, certain services have come to dominate and stifle the very diversity that made their existence possible. Maria Farrell talks about why we must - and how we c…