The BGP Large Communities Playground

Pier Carlo Chiodi
Based in Italy
System and network administrator, I started working in the IT/ICT during the late '90s. Area of interest: IPv4 exhaustion and IPv6 transition mechanisms, Internet measurement and network data analysis, infrastructure security. More
• 4 min read
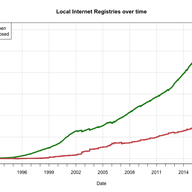
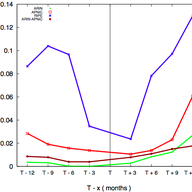
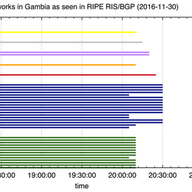
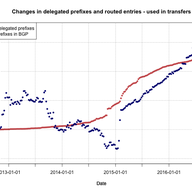
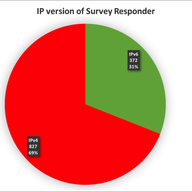
This article describes the BGP Large Communities Playground, and encourages people to utilise automated regression testing and compliance checking when developing new protocol features.