Large BGP Communities - Largely Accepted Now?


Emile Aben
Based in Amsterdam, NL
I'm a data scientist at the RIPE NCC. I'm a chemist by training, but have been working since 1998 on Internet related things, as a sysadmin, security consultant, web developer and researcher. I am interested in technology changes (like IPv6 deployment), Internet measurement, data analysis, data visualisation, sustainability and security. … More
• 11 min read
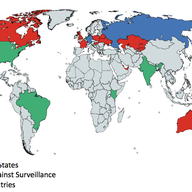
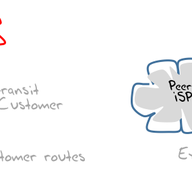
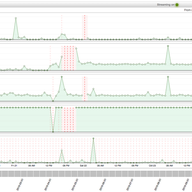
Large BGP Communities are an addition to BGP that solves a communication problem between networks that want to use 32-bit AS Numbers. We measured how Large BGP Communities behave "in the wild" and if they create any problems.