Impact of K-root Expansion as Seen by RIPE Atlas

Rene Wilhelm is a senior research engineer in the R&D department at the RIPE NCC. Coming from a background in particle physics, Rene joined the RIPE NCC in 1996. His interests are in data analysis, routing, Internet measurements and visualisation. More
• 12 min read
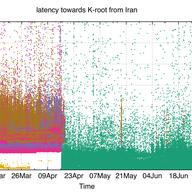
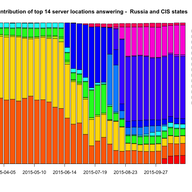
In the course of 2015 we have expanded the K-root anycast cluster with 17 hosted servers in 15 new cities. We look at RIPE Atlas to see what impact this had on performance on both global and regional scales.