Real-time BGP Visualisation with BGPlay


Massimo Candela
Based in Amsterdam
At the time of writing articles listed here, Massimo Candela was Senior Software Engineer with R&D at the RIPE NCC, working mainly on developing web applications that provide a visual and interactive representation of large amounts of network data. Tools he played a key role in developing are go-to resources … More
• 6 min read
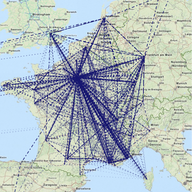
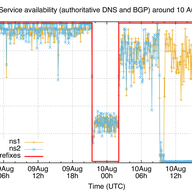
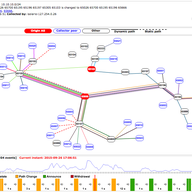
Please read about this new milestone release of the popular BGPlay web application. It can now receive BGP messages using WebSocket and update the visualisation on the fly.