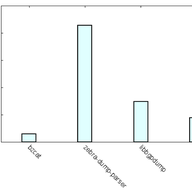
Delta-V Gets Take-off Speed

George Michaelson is currently APNIC's senior R&D scientist. Recently, he has been working on long-baseline IPv6 and DNS statistics using Internet-wide end-user measurement, services logging, audit and analysis, and design and implementation of the Internet Number Resource Certification framework. George is a member of the BCS, and a founder member … More
• 8 min read
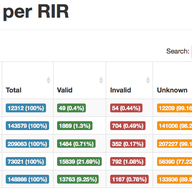
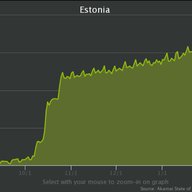
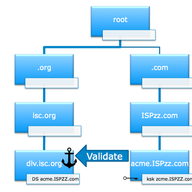
The adoption of the RPKI system is growing rapidly. To make sure the system scales, we’ve developed a new protocol that should drastically improve fetch times for RPKI repositories. This article explains how.