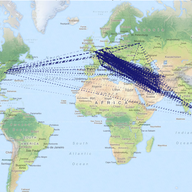
The DNS Root Zone Key-Signing Key is Changing


Mirjam Kühne
Based in Amsterdam, The Netherlands
I wrote the articles collected here during my time as community builder of the RIPE NCC and the maintainer and editor of RIPE Labs. I have since taken on a new role serving as the Chair of the RIPE Community. You can reach my new profile via the website link … More
• 5 min read
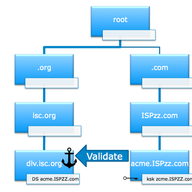
Tony Smith from the APNIC gives an update on the DNS Root Zone Key-Signing and explains how the key-signing-key roll over will be done for the first time.