An Updated DNS Monitoring Service

Former Communications Writer at the RIPE NCC. More
• 4 min read
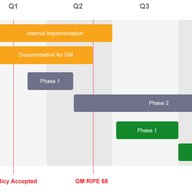
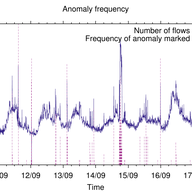
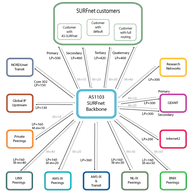
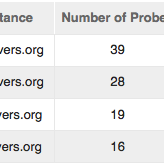
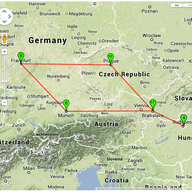
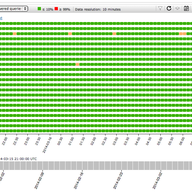
Since 2003, the RIPE NCC’s DNS Monitoring Service (DNSMON), has been providing a comprehensive, objective, and up-to-date overview on the quality of the service offered by TLD and other DNS operators. Due to technical advancements and in line with our aim to provide consolidated services, we are in…