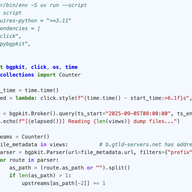
The IRR Landscape: Where Do ASes Keep Their Routes?


Stavros Konstantaras
Based in Amsterdam
Stavros Konstantaras is an enthusiastic all-around network engineer, holding an MSc from University of Amsterdam in the field of System & Network Engineering. His experience at NLnet Labs and the University of Amsterdam has supplied him with valuable skills and knowledge like scripting, system virtualization and network programming. He has … More
• 18 min read
We map where networks actually publish routing data - across RIR-run and third-party IRRs - and how that data is used in practice. Connecting our findings with RPKI growth and exploring regional patterns, we examine legacy space and operational risks to suggest clear clean-up priorities.