Live-Event Blocking at Scale: Effectiveness vs. Collateral Damage in Italy’s Piracy Shield


Antonio Prado
Based in ITALY
I hold a Ph.D. in Computer Science, with a research focus on Internet Routing Security, where I developed tools and methodologies for the automated verification of BGP configurations. With over 30 years of technical and project experience, I am coauthor of the book BGP from Theory to Practice, aimed at … More
• 9 min read
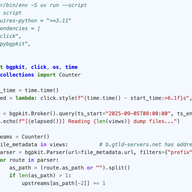
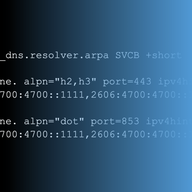
Italy’s Piracy Shield blocks IPs and domains within minutes, but measurements performed by researchers at the University of Twente and colleagues show broad collateral damage to legitimate services. We share the results of those measurements in the hopes of sparking a community discussion around th…