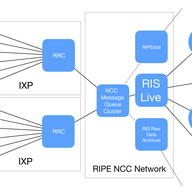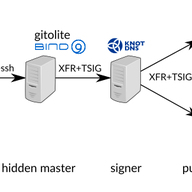
BGP Communities - A Weapon for the Internet (Part 1)


Florian Streibelt
Based in Saarbrücken, Germany
Florian Streibelt is a PhD candidate at the Max Planck Institute for Informatics in Saarbrücken, Germany, supervised by Anja Feldmann. In 2013 he graduated with a Diploma Degree in computer science from Technische Universität Berlin. During his undergrad time at TU Berlin he worked as a systems administrator and as … More
• 9 min read
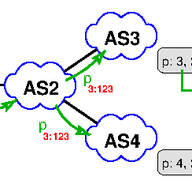
This is the first of two articles in which we present a new attack vector on the routing infrastructure of the Internet using BGP communities.