Abuse-c Validation: Update on Progress and Some Numbers

Policy Officer at RIPE NCC, supporting the Policy Development Process (PDP) for the implementation of accepted RIPE community policies. More
• 6 min read
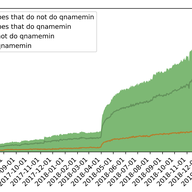
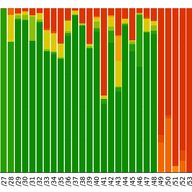
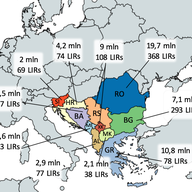
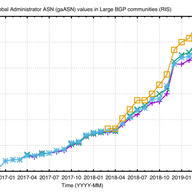
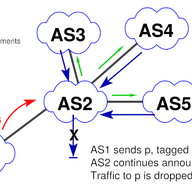
With RIPE 78 around the corner, we want to update you on our work to validate abuse contacts in the RIPE Database.