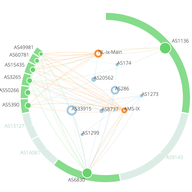
Routing to and from the Netherlands

Marco was acting Manager Public Policy and Internet Governance with the RIPE NCC until moving on from the organisation in 2022. He joined the RIPE NCC in 2011, working for two years in the Training Services team. Prior to joining the RIPE NCC, he worked as a Network Engineer for … More
• 5 min read
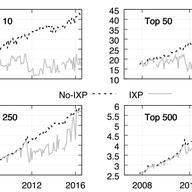
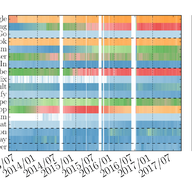
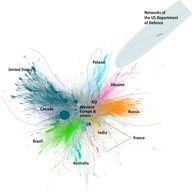
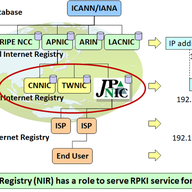
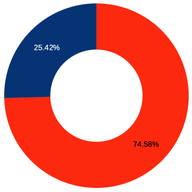
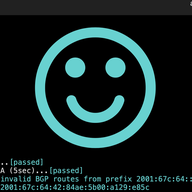
Following earlier publications, Radiocommunications Agency Netherlands asked if we could perform an analysis of the Dutch market – in particular, the routing arrangements between networks.