Honeypot-based Monitoring of Amplification DDoS Attacks

Johannes Krupp
Based in Saarbrücken
Johannes Krupp is a researcher at the CISPA Helmholtz Center for Information Security in Saarbrücken, Germany. He joined CISPA as a Ph.D. candidate after receiving a bachelor degree in computer science from Saarland University in 2014. His research on DDoS attacks and attack attribution has been recognized by the academic … More
• 5 min read
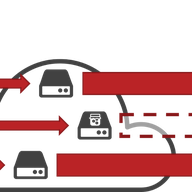
Amplification DDoS attacks are one of the most prevalent forms of denial-of-service attacks. The SISSDEN project (sissden.eu) operates a network of honeypots designed to detect these attacks, observing 10,000 per day.