Monitoring BGP Anomalies on the Internet

Martin Winter is a technical lead and cofounder of the Network Device Education Foundation and he works on the side for Hurricane Electric Internet Services as a Researcher on the RT-BGP (Real-Time BGP) Toolkit. His research interests include routing protocols, platforms, networked systems, and software engineering as well as OpenSourceRouting, … More
• 5 min read
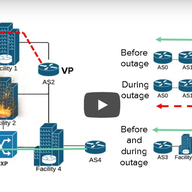
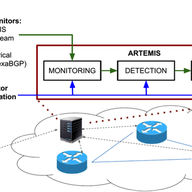
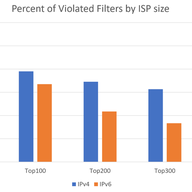
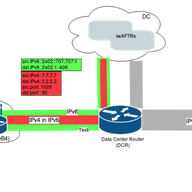
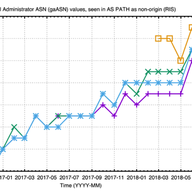
There are many flavours of BGP hijacks, misconfigurations or outdated implementations. Here are some examples and tips how to verify your announcements.