Anycast Latency: How Many Sites are Enough?

JH Kuipers
Based in Enschede, NL
Master's student at the University of Twente. Currently performing research at the DACS group of the EWI faculty. More
• 4 min read
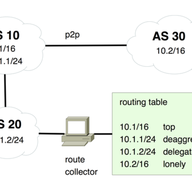
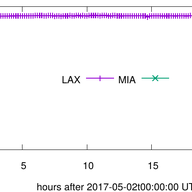
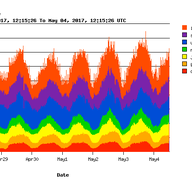
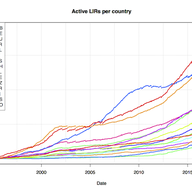
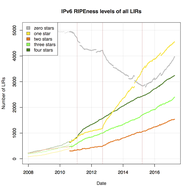
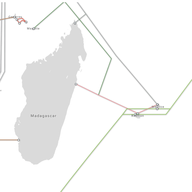
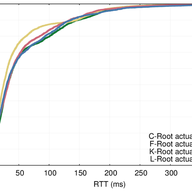
IP anycast is a popular way to scale up and distribute services across the Internet, with the aim of getting closer to end users. Using anycast, the IP address of a service is available in multiple places on the Internet — so-called anycast instances or sites — and Internet routing defines which in…